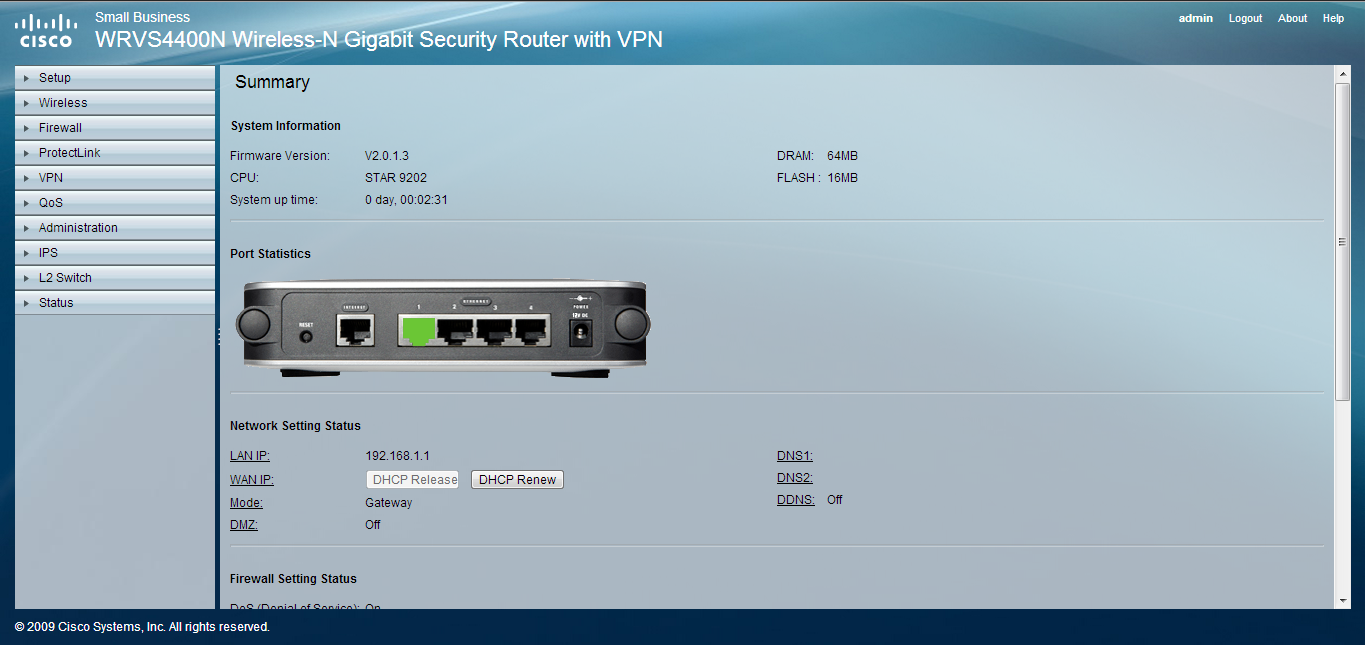
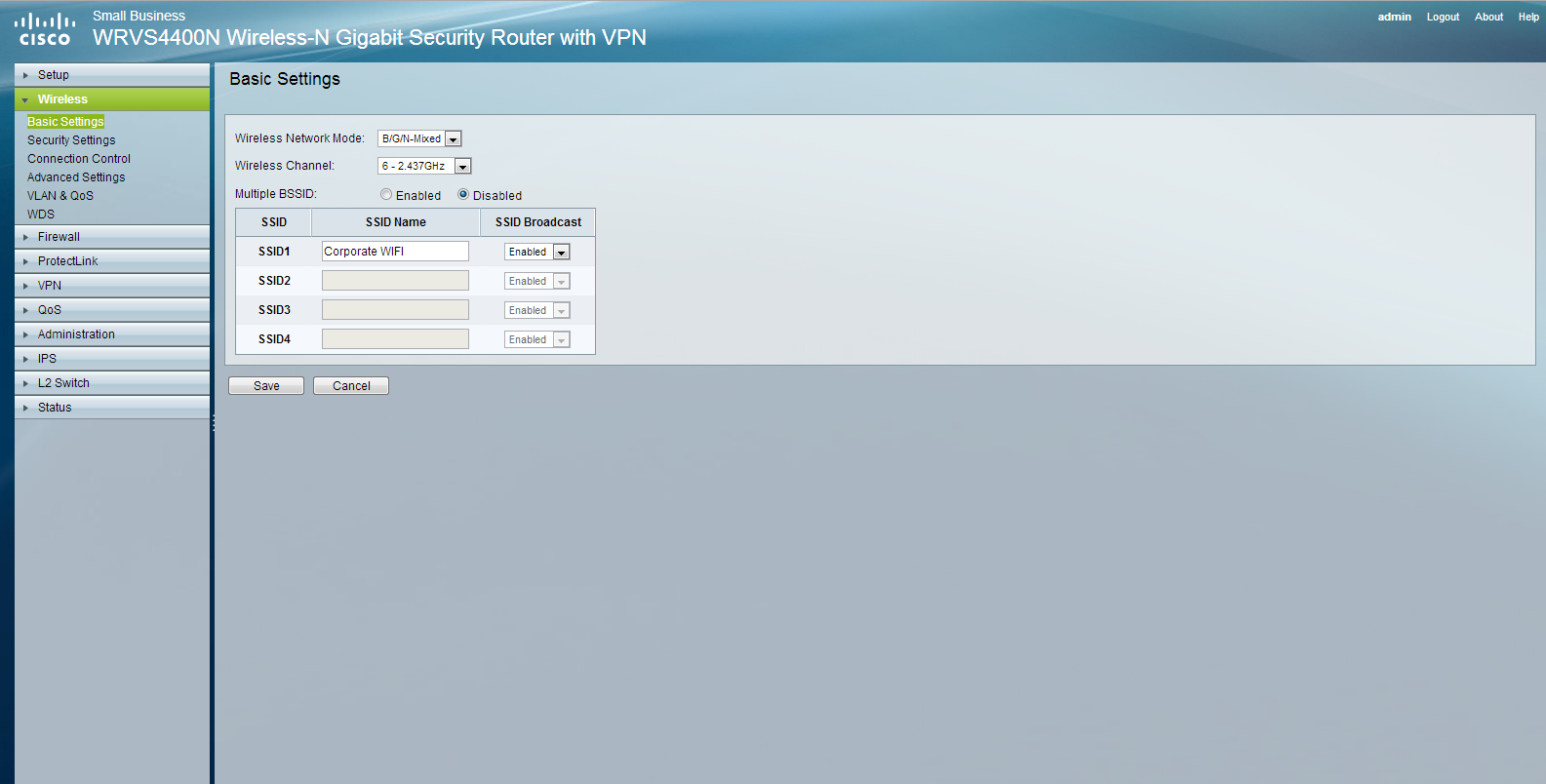
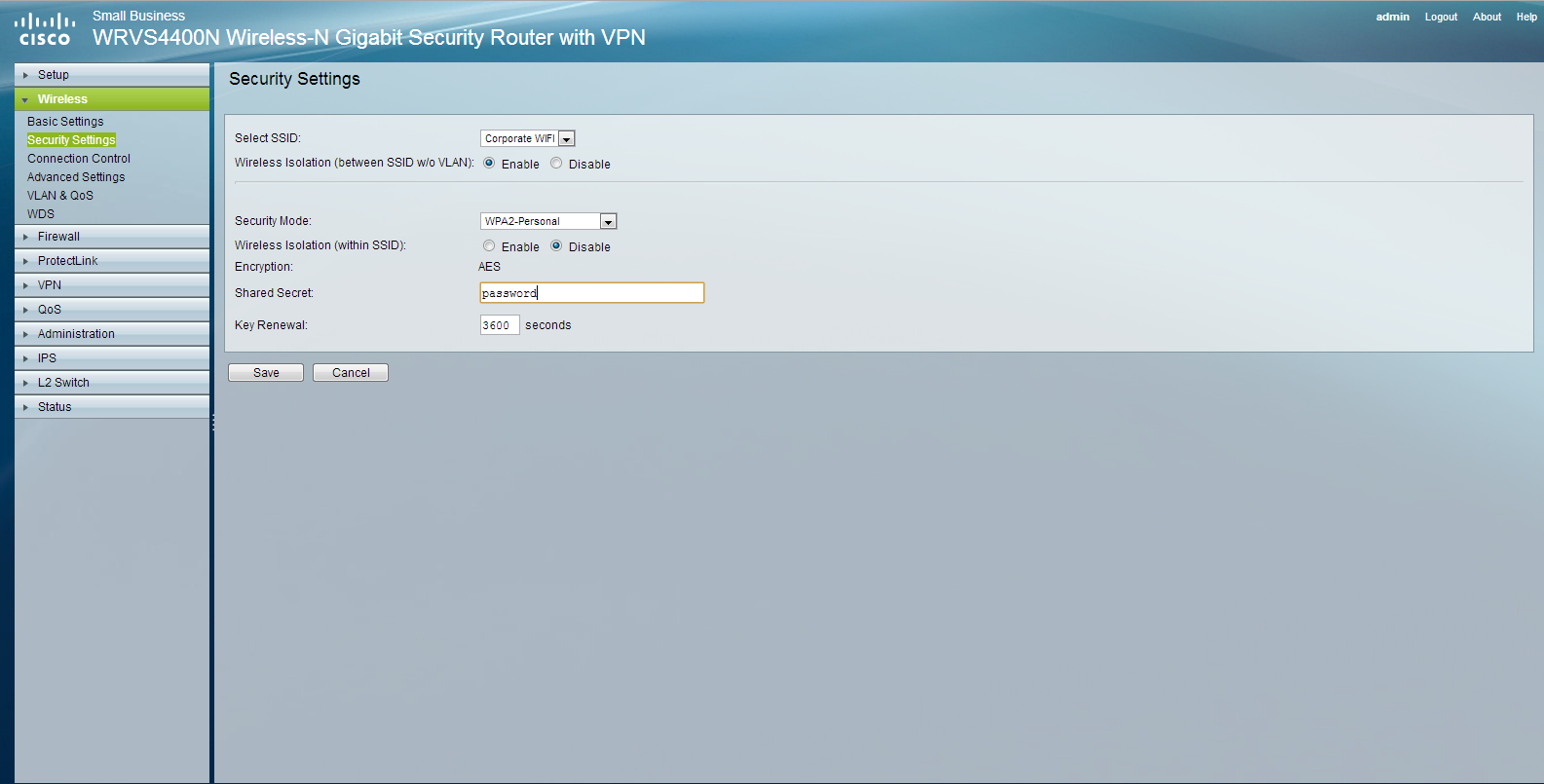
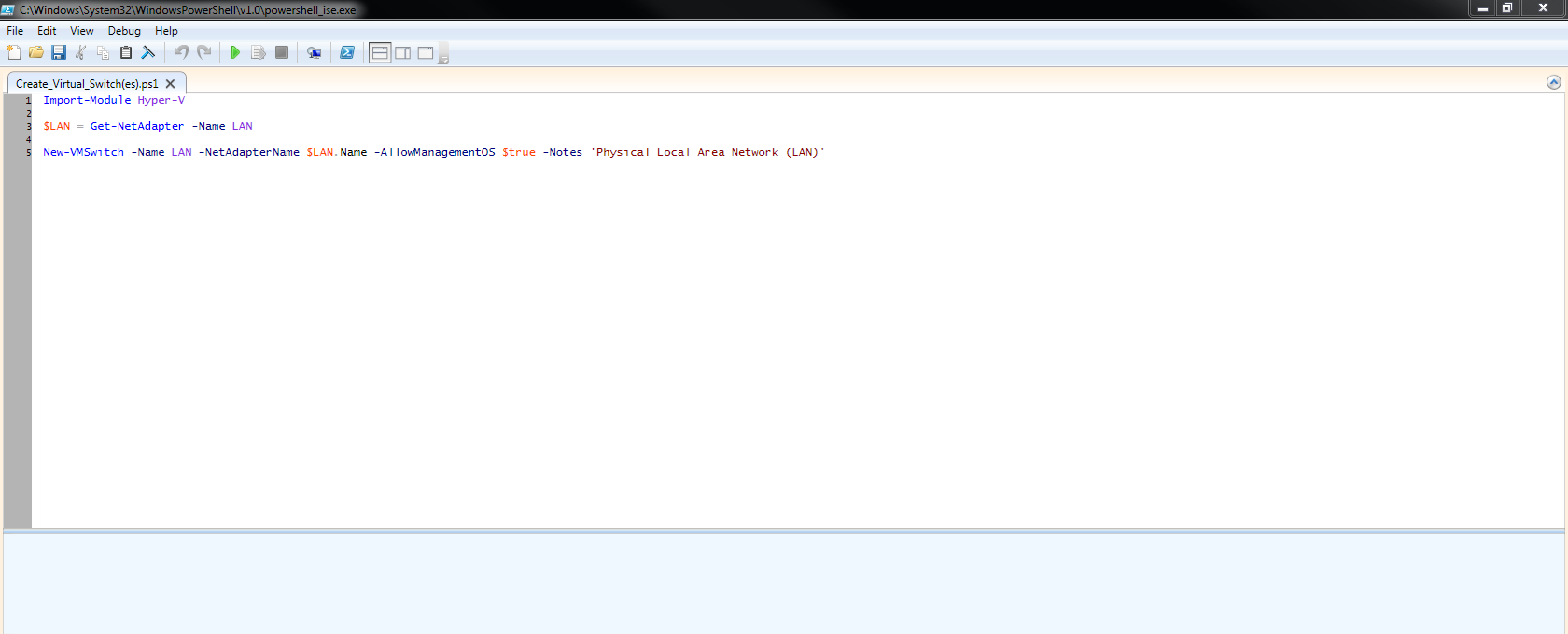
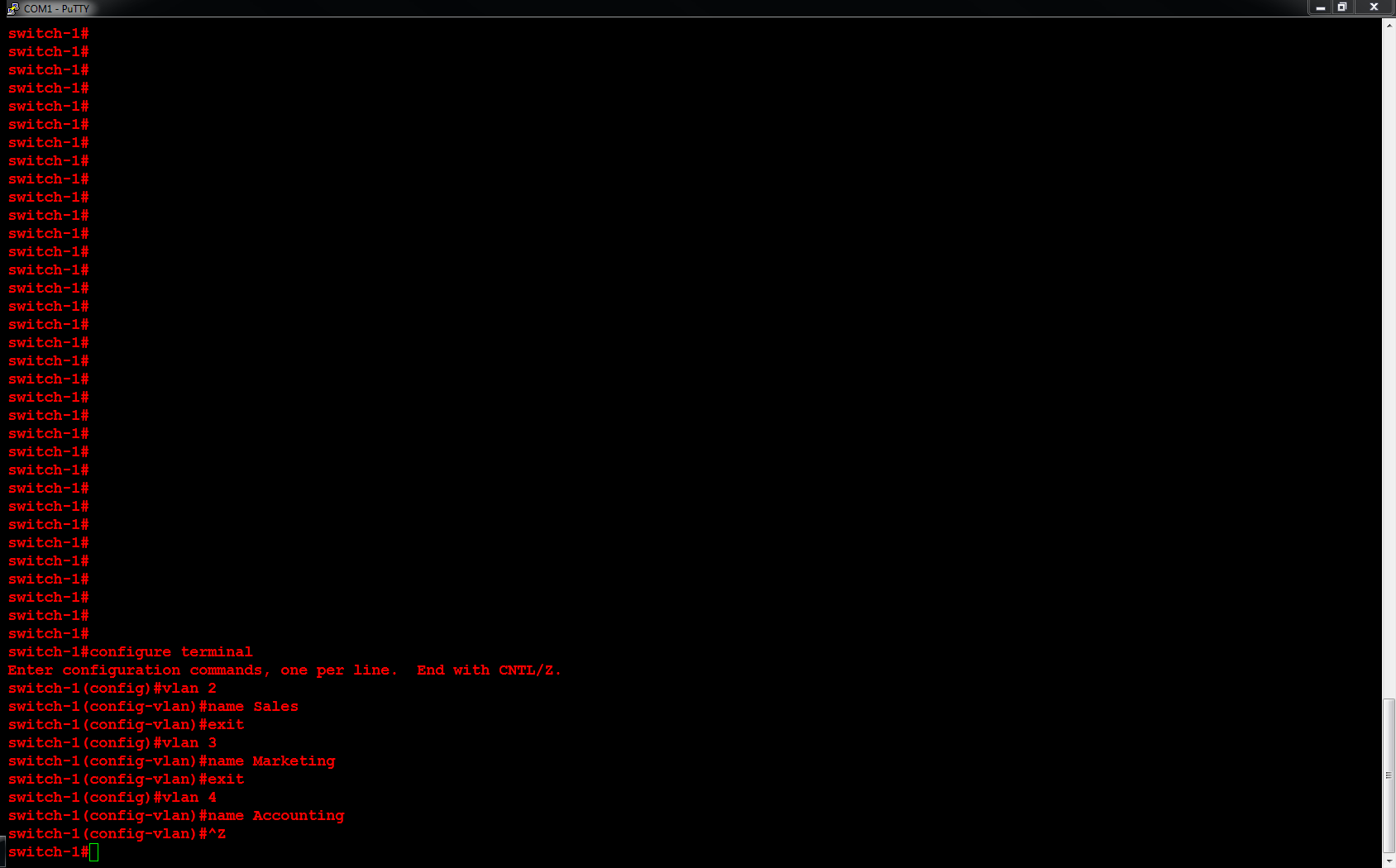
Microsoft Hyper-V allows you to create (3) types of virtual switches (External, Internal and Private). These virtual switches may be created manually using the Hyper-V Manager or you may use a PowerShell (.ps1) script to automate the process. Below you will find a script to create an External virtual switch.
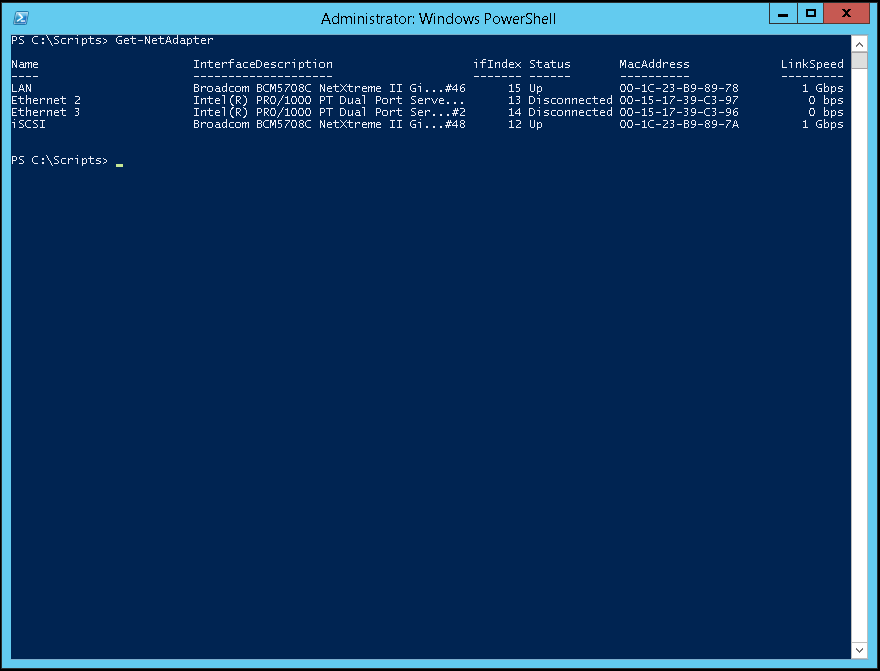
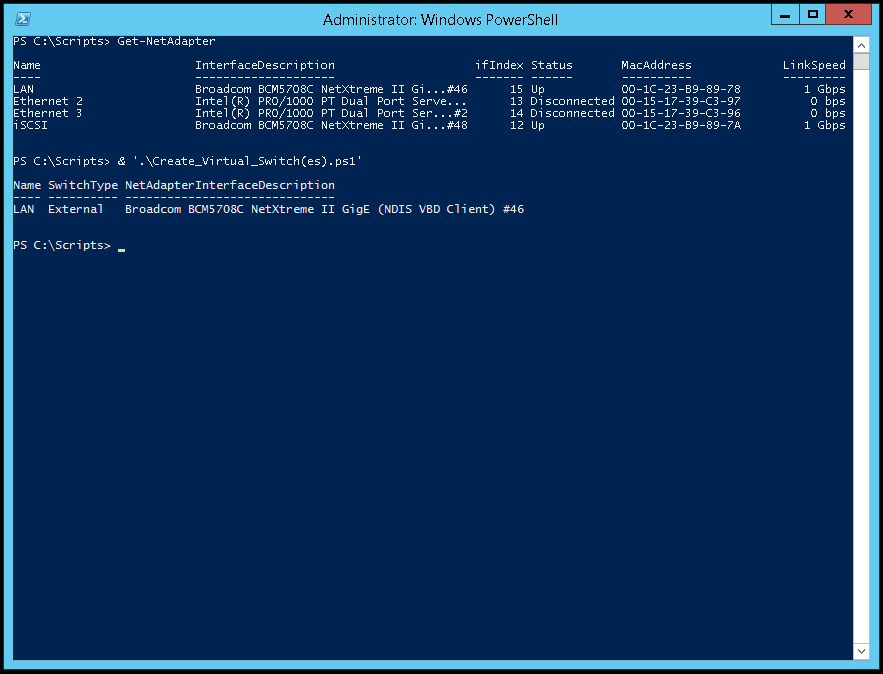
1. Issue the Get-NetAdapter command to provide a list of physical network interface (NIC) card(s) on the host. Take note of the name of the NIC that will be used for the external virtual switch.
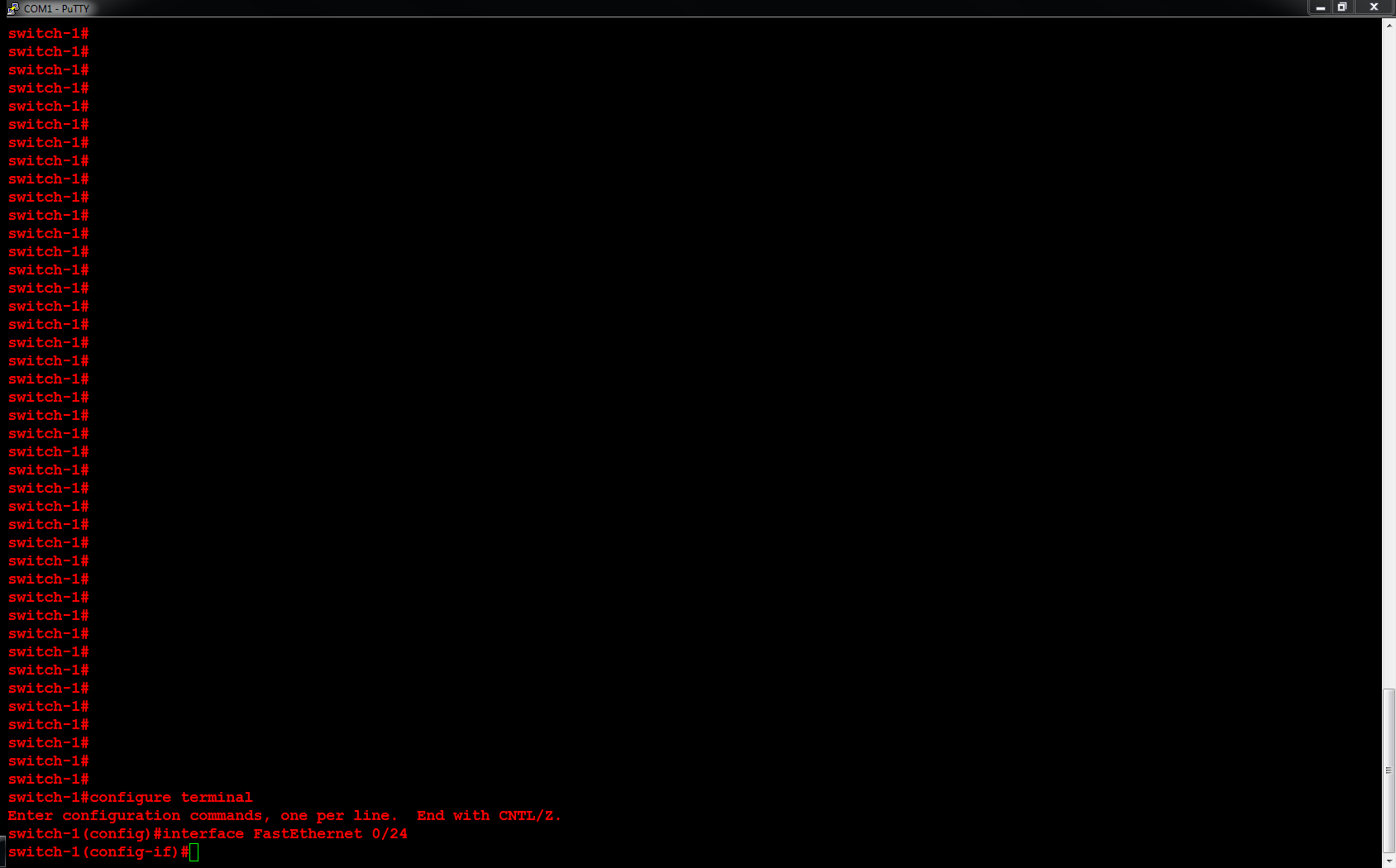
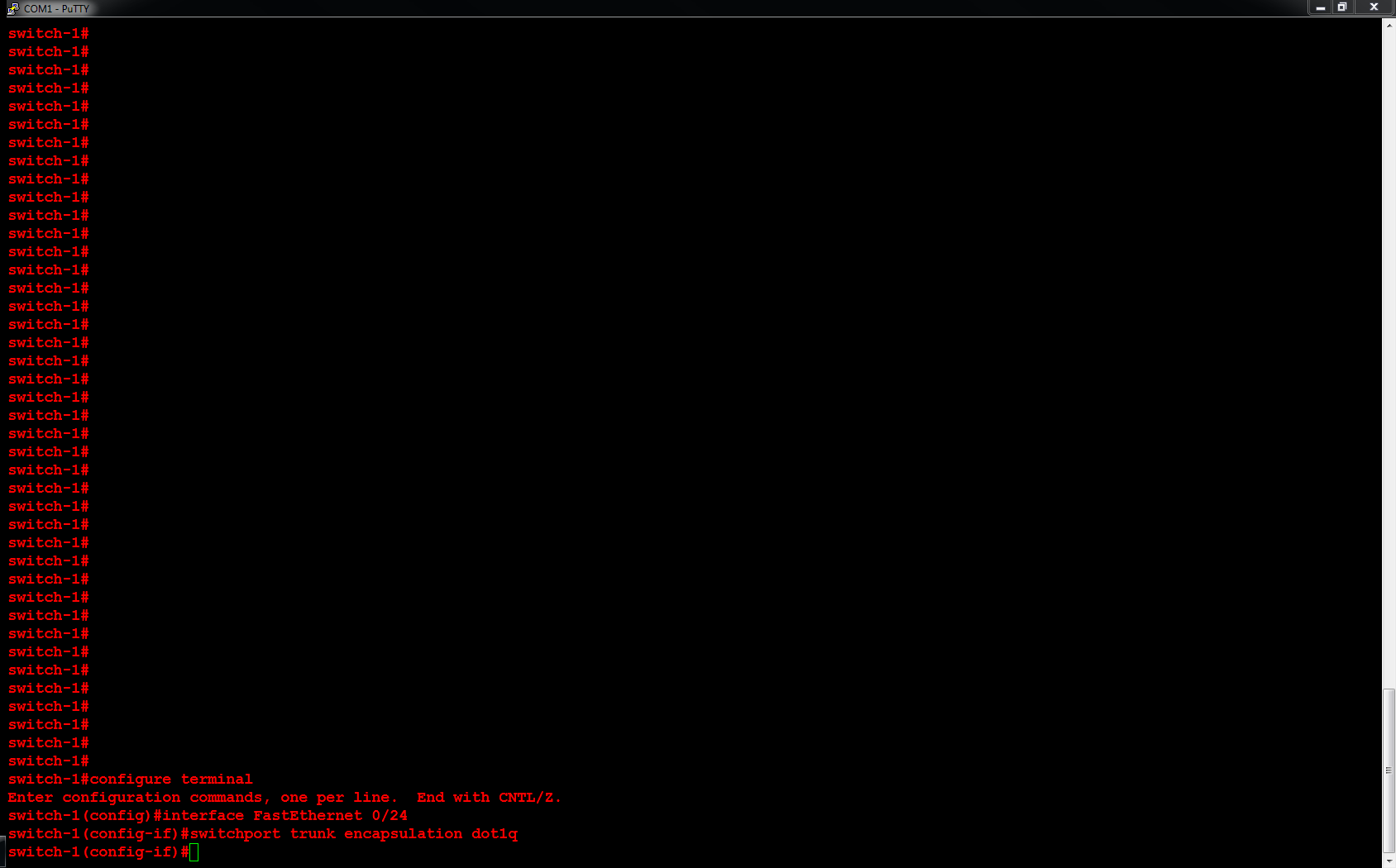
2. You may modify the script below to create an external virtual switch.
3. Run Microsoft Powershell (as an Administrator) to create the external virtual switch.
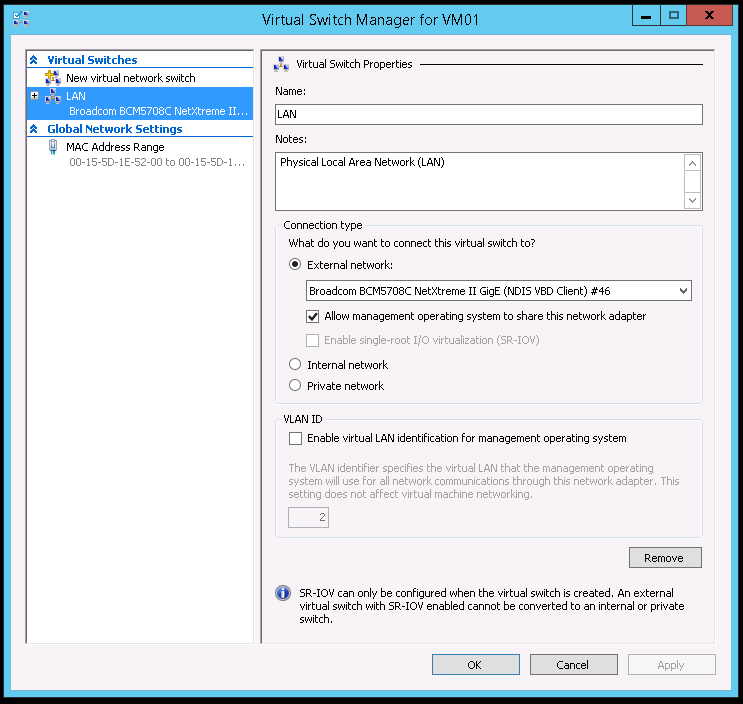
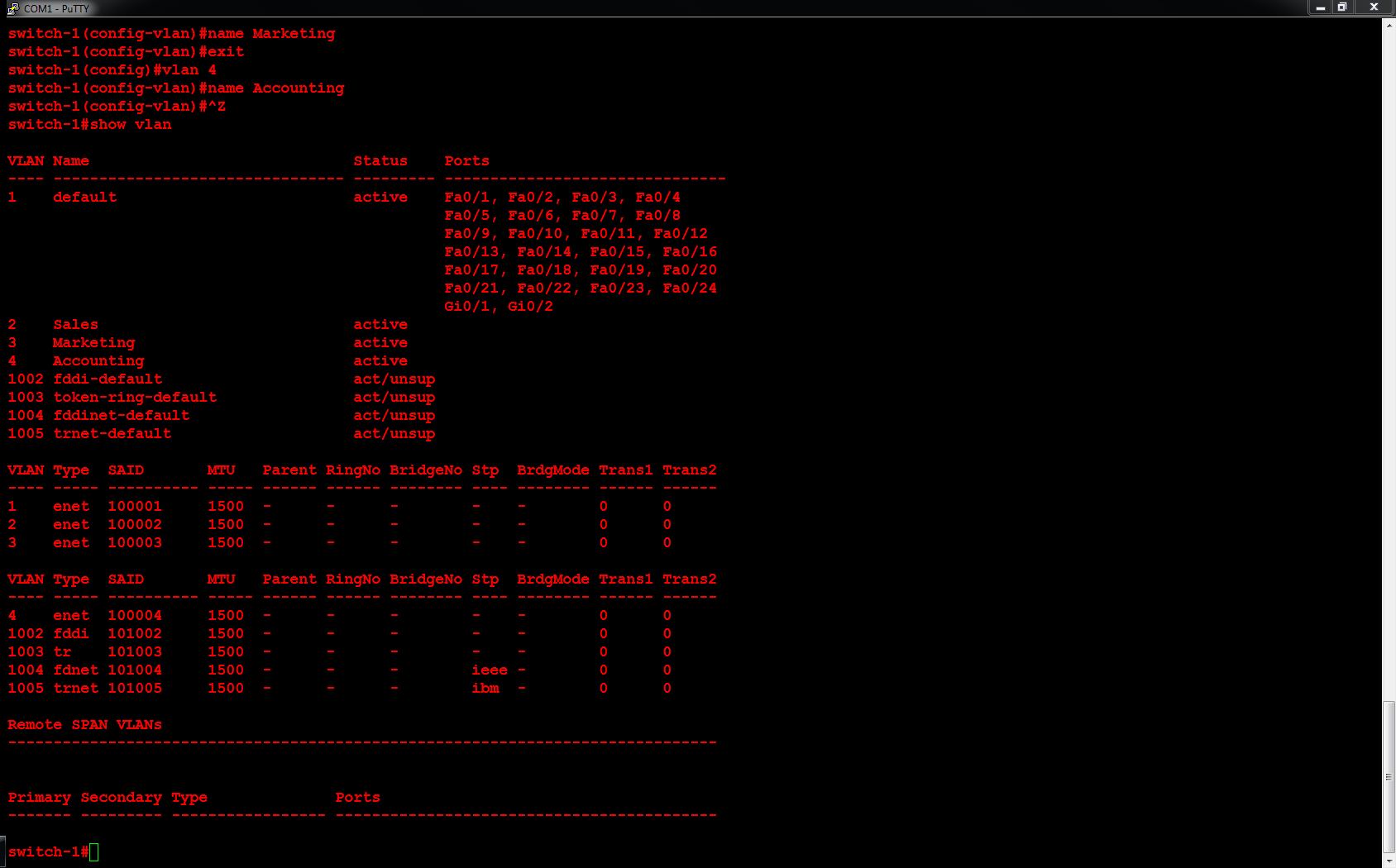
4. Lastly, verify the creation of the virtual switch using the Hyper-V Manager > Virtual Switch Manager.

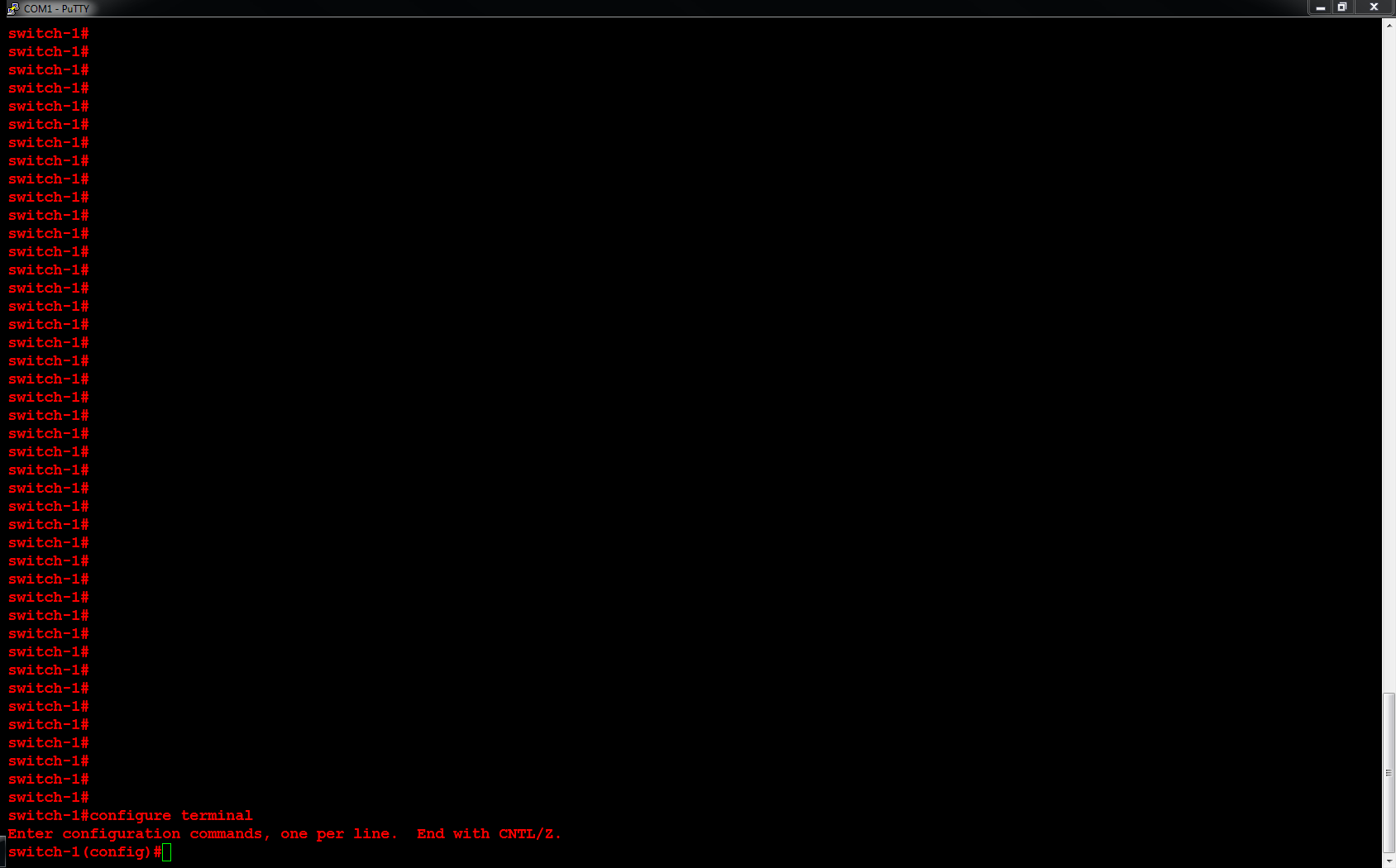
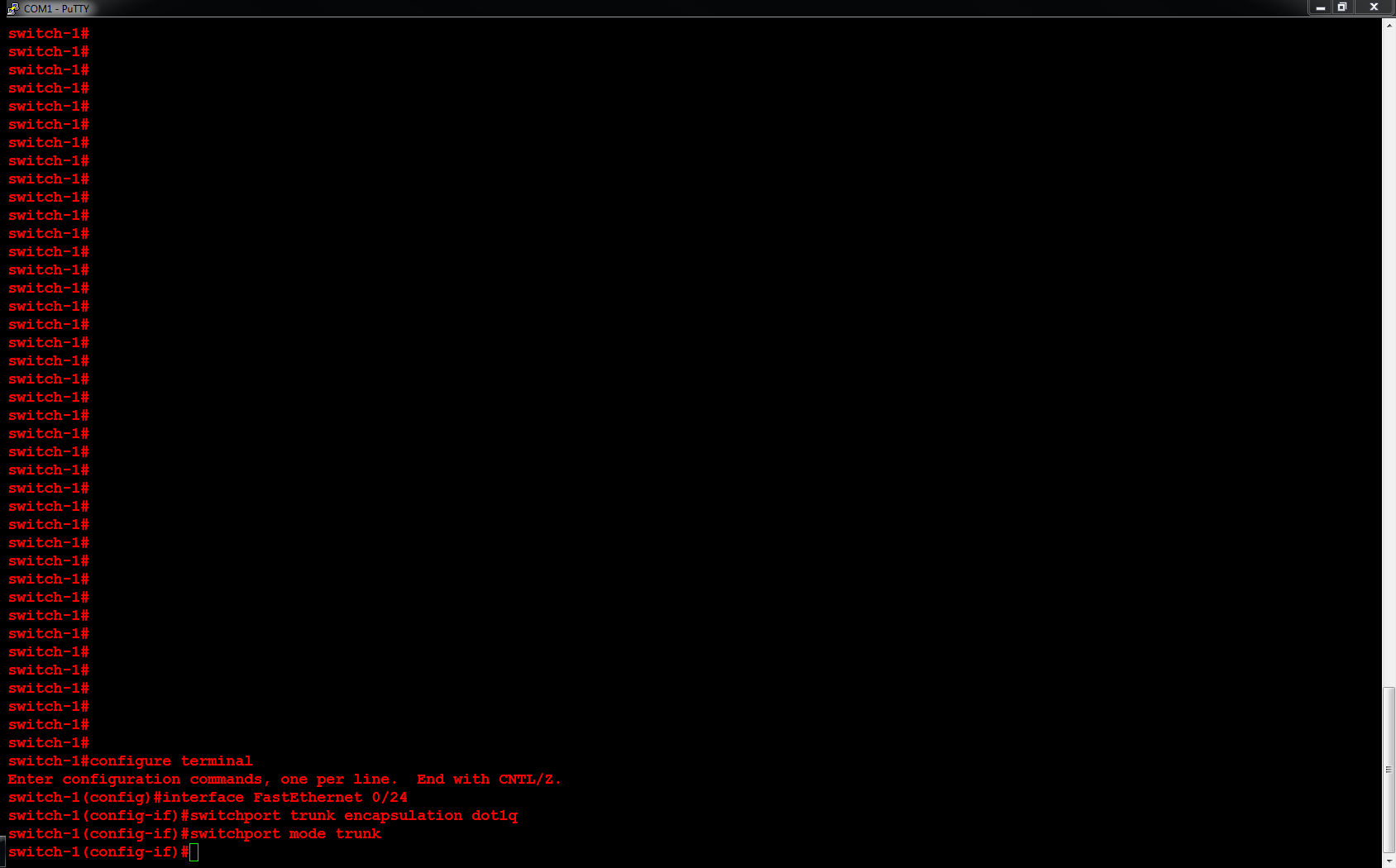
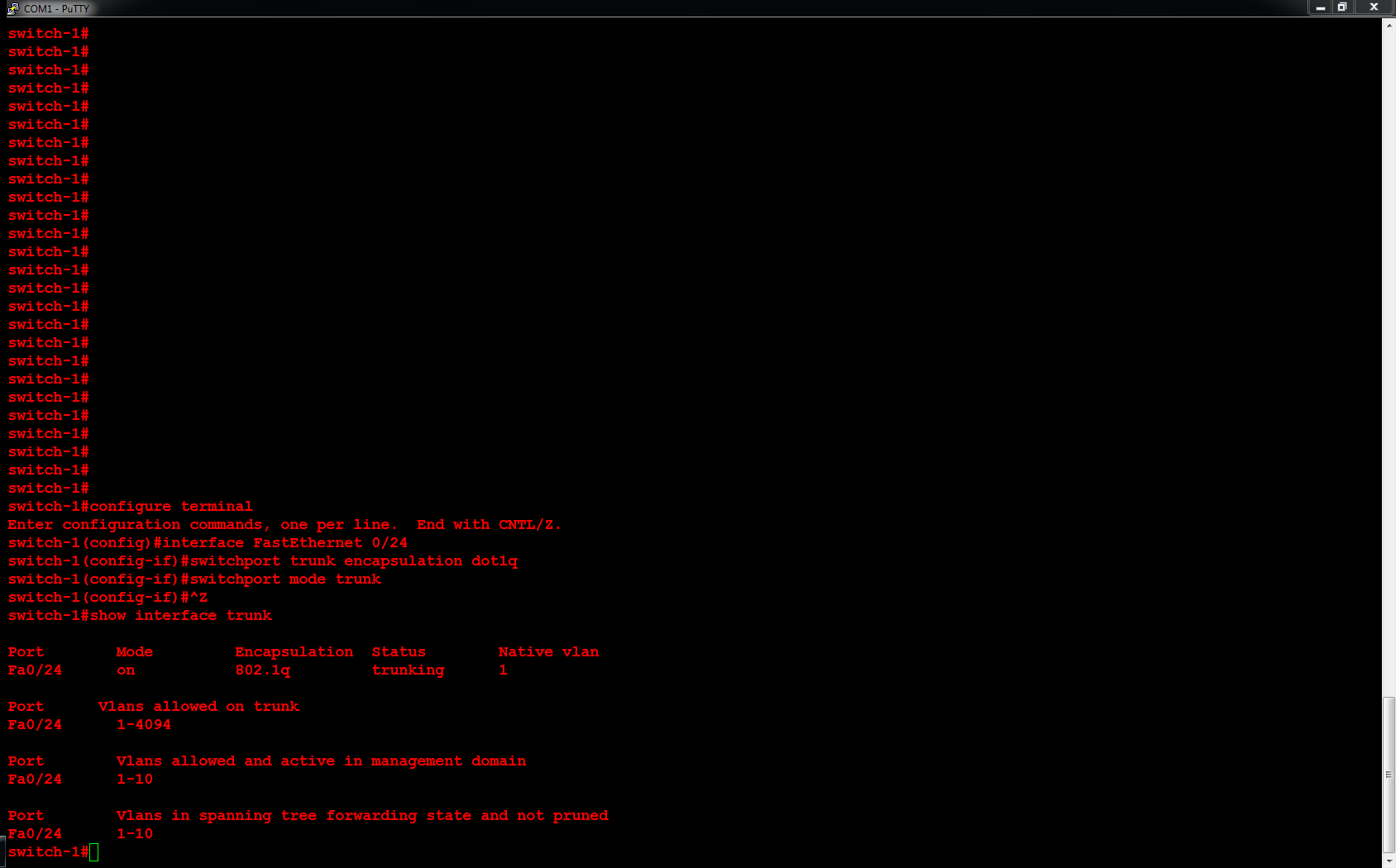


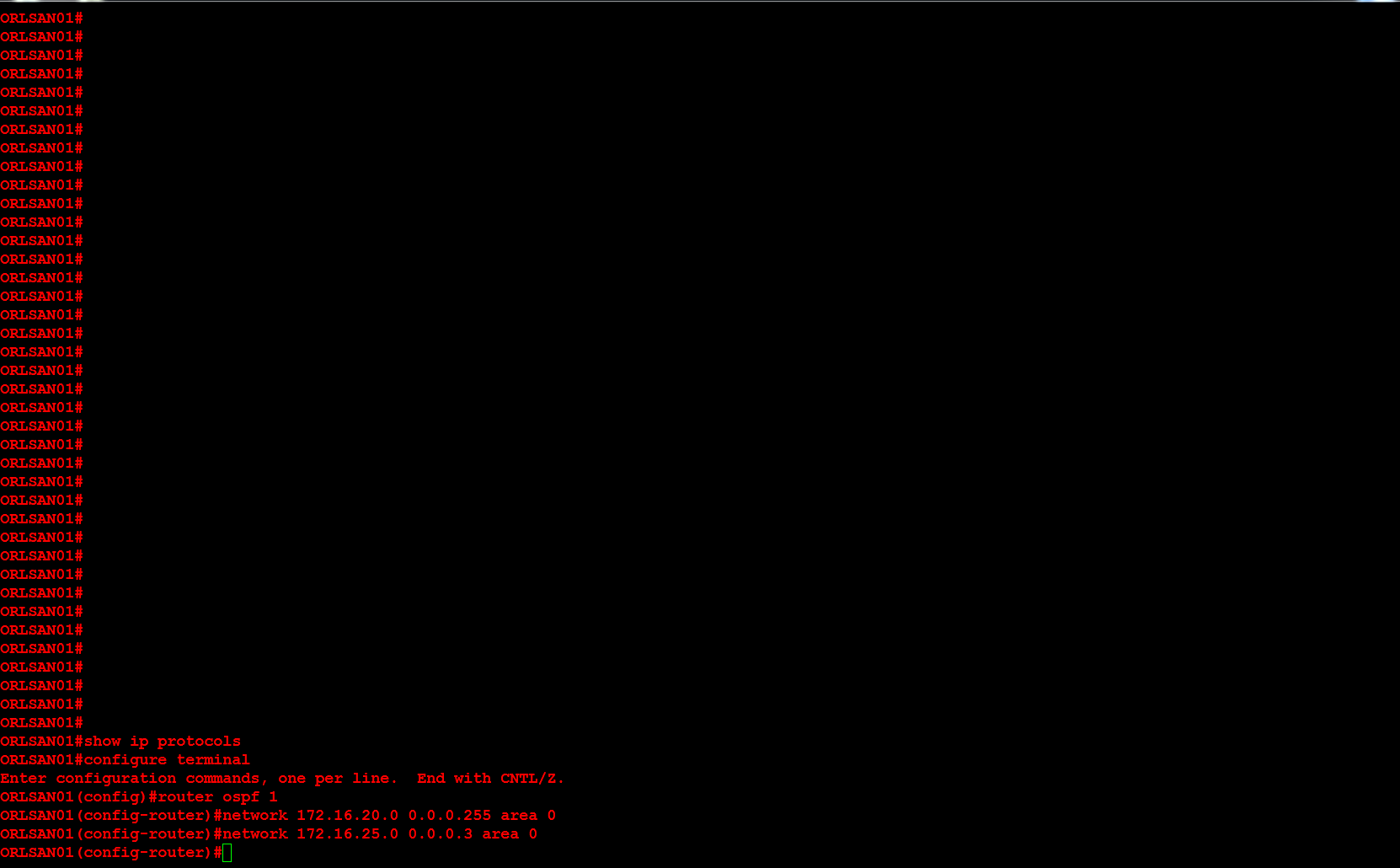

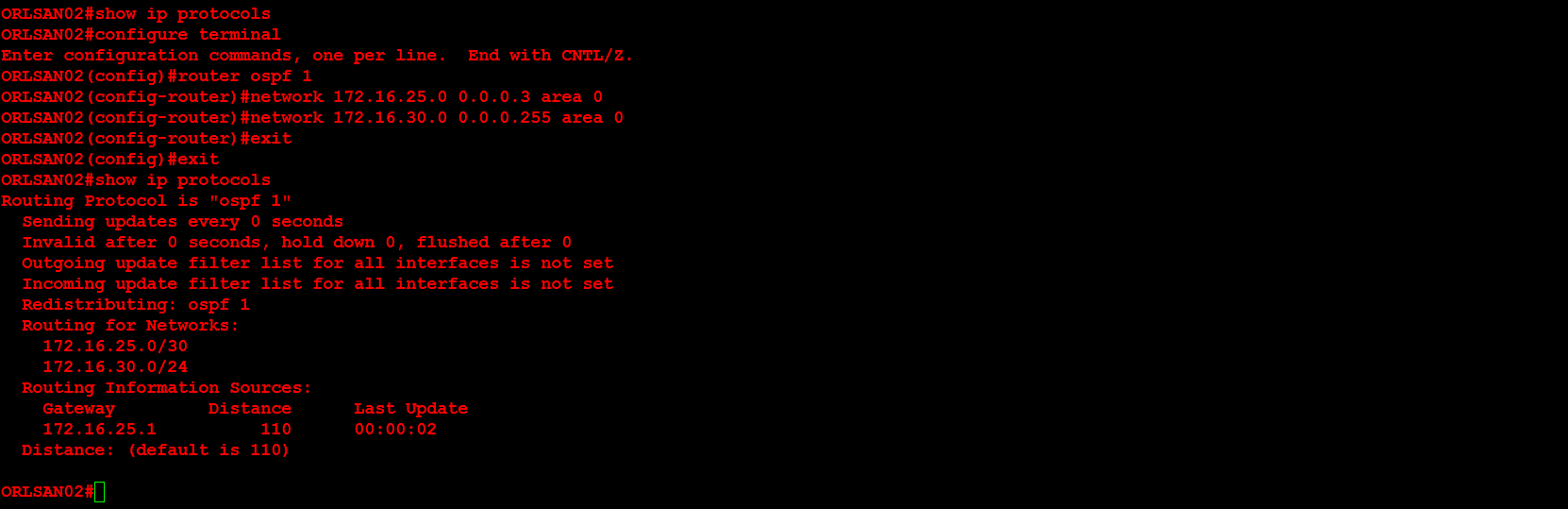
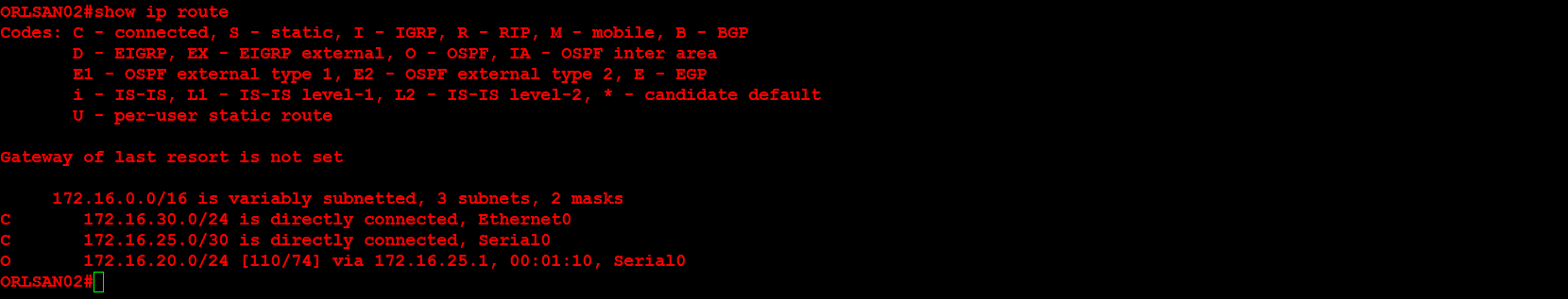

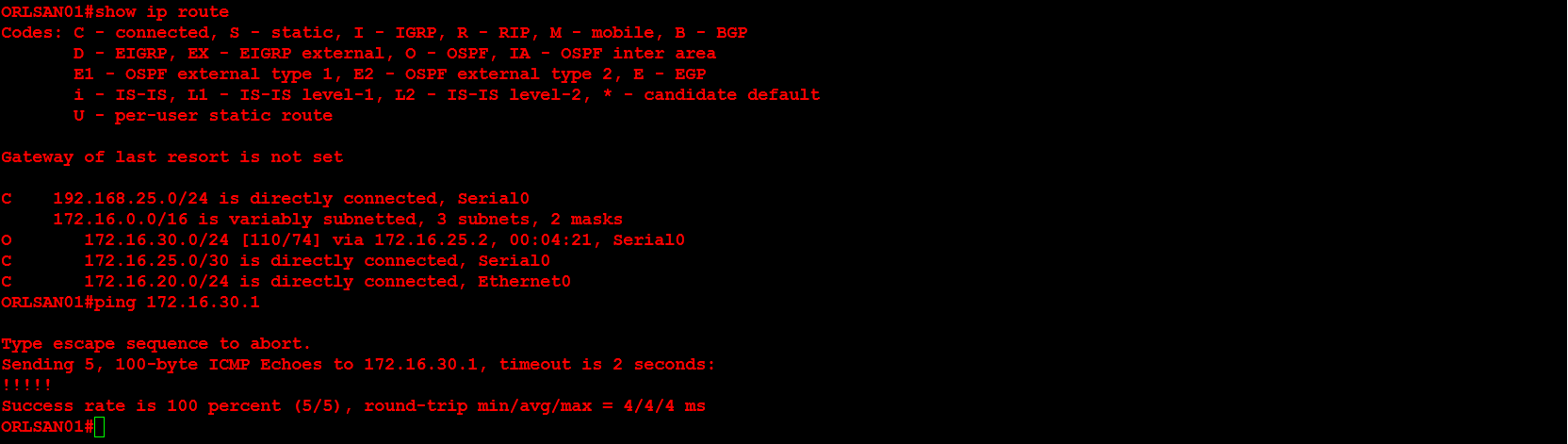



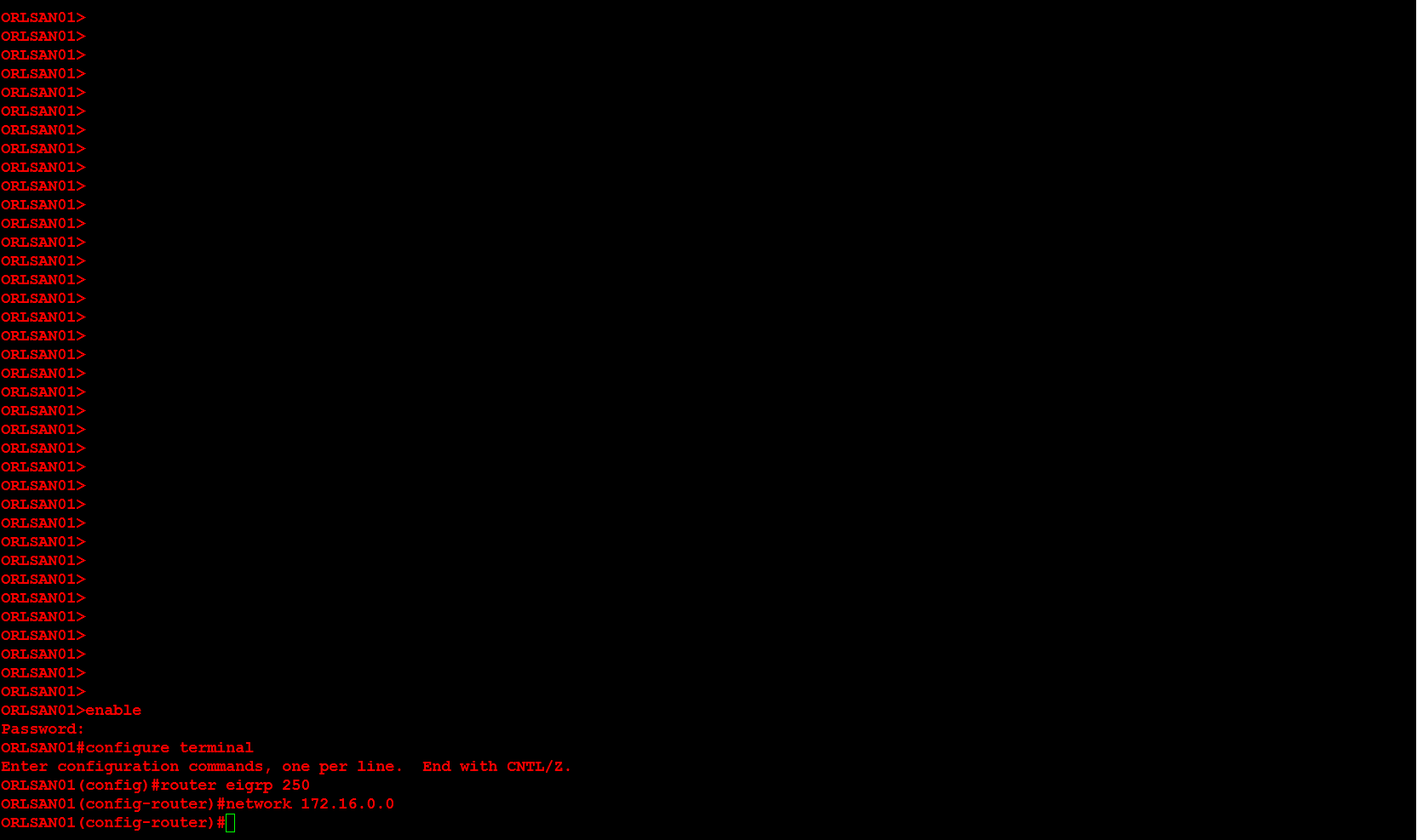
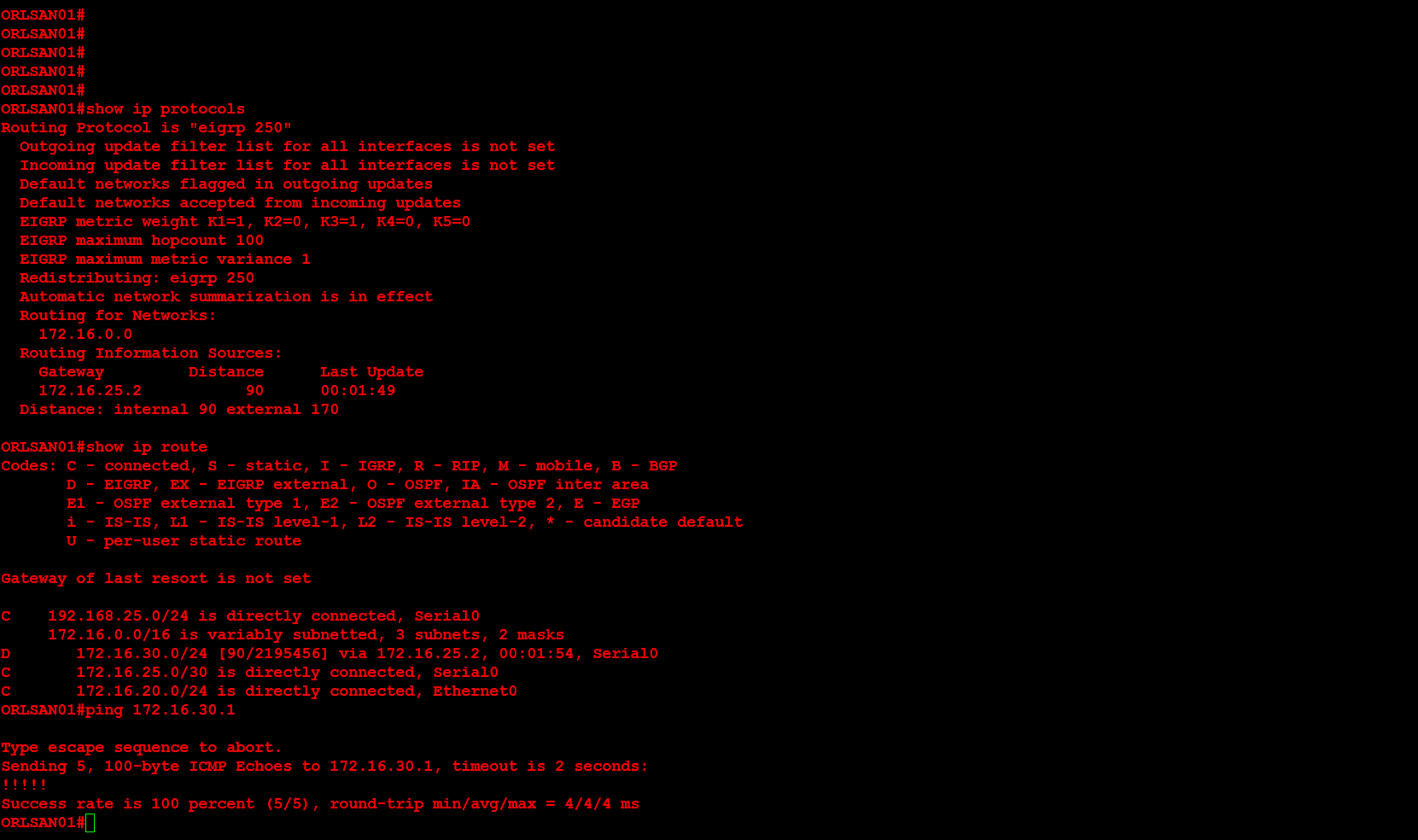





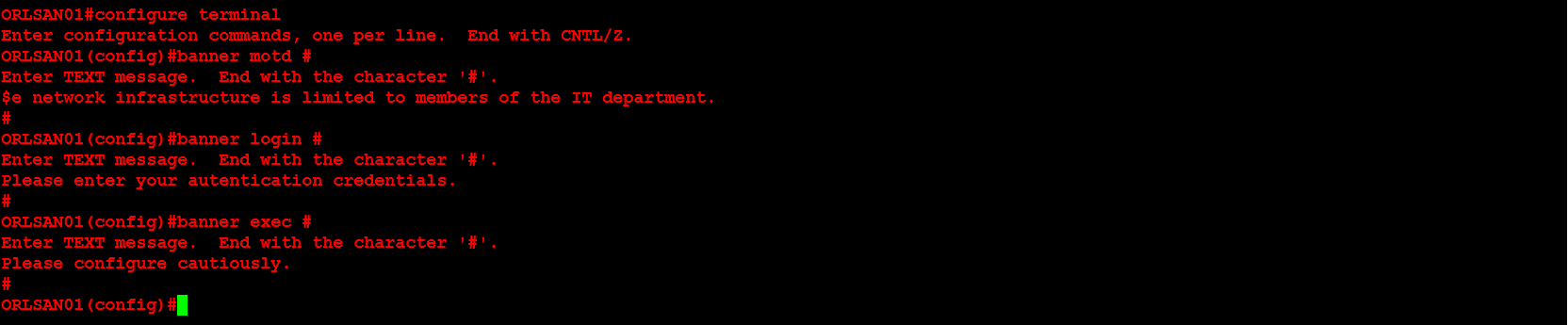
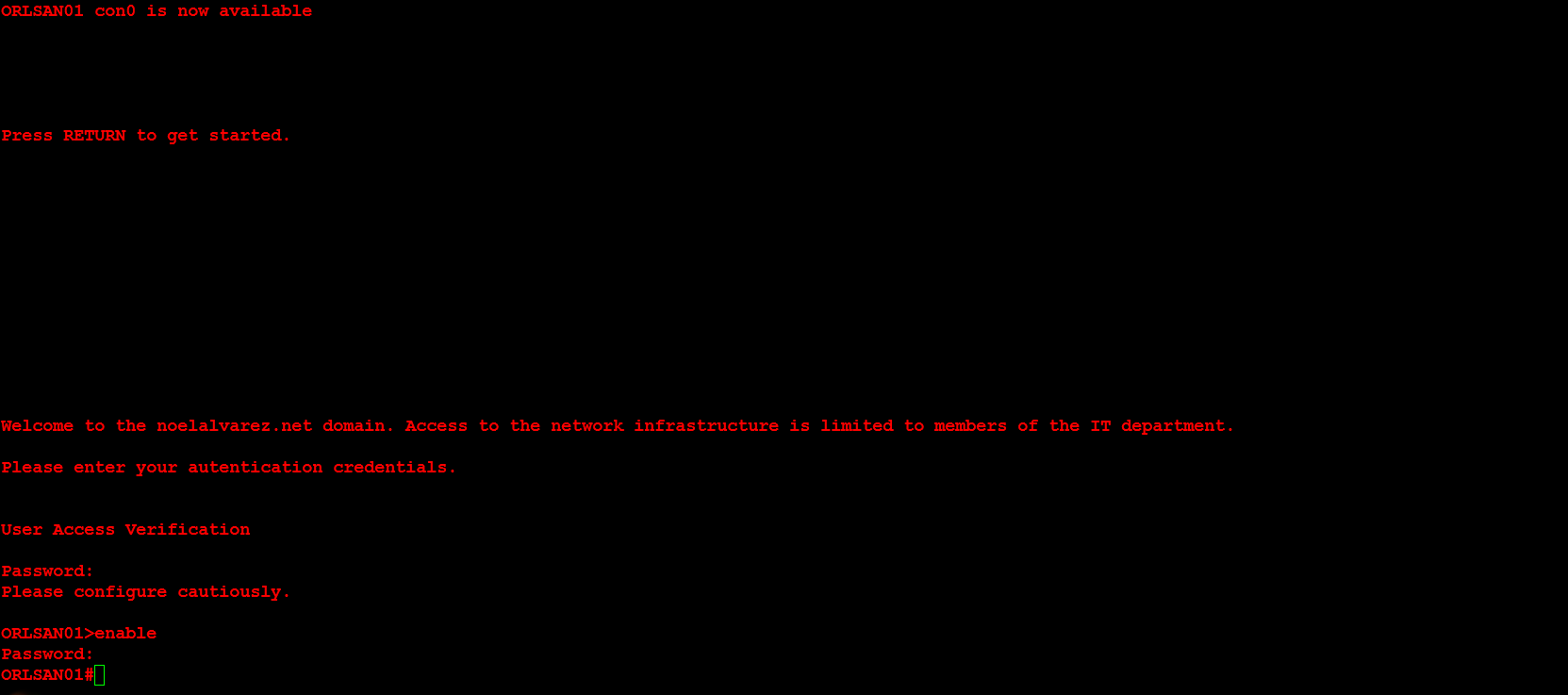
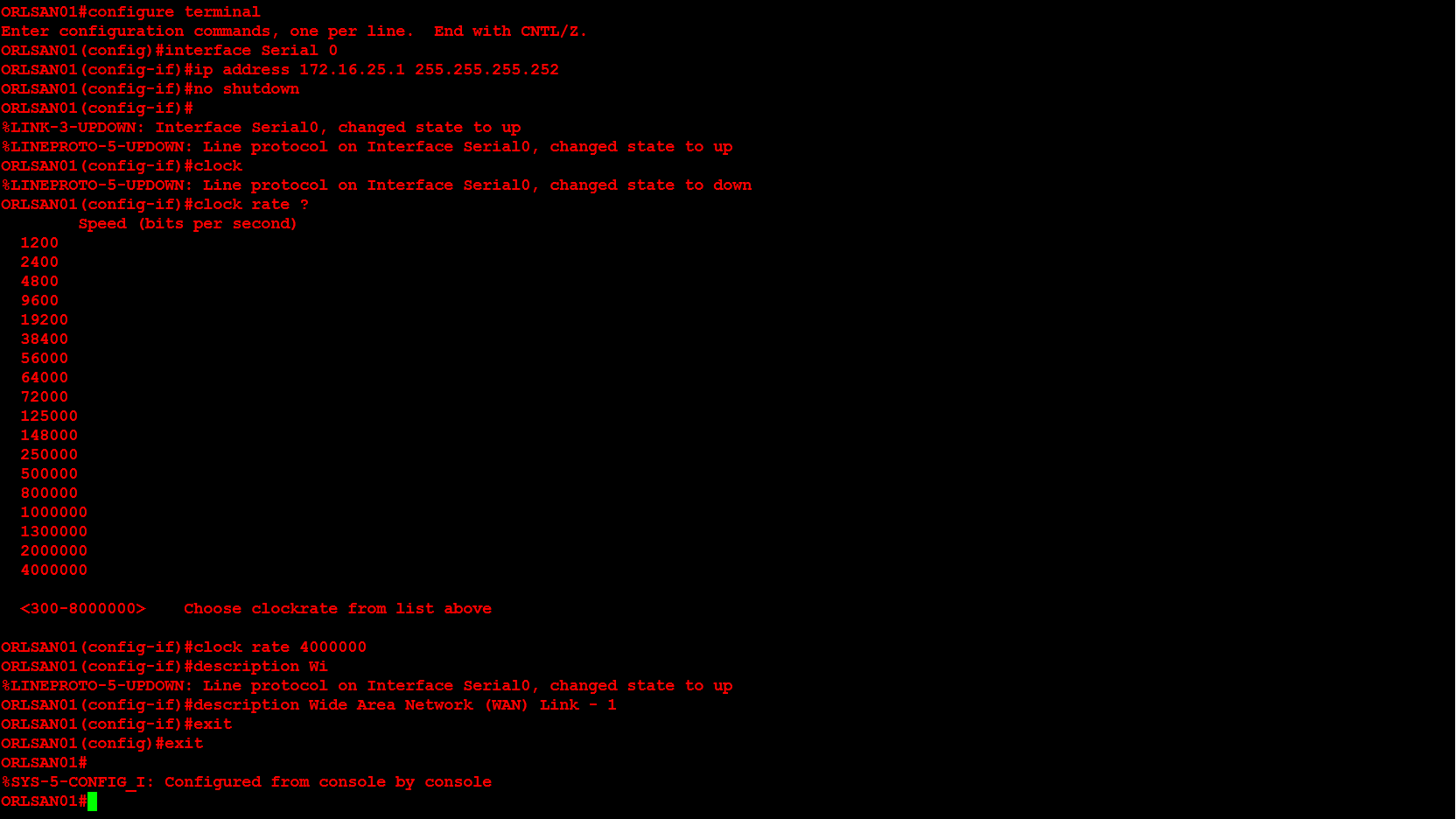
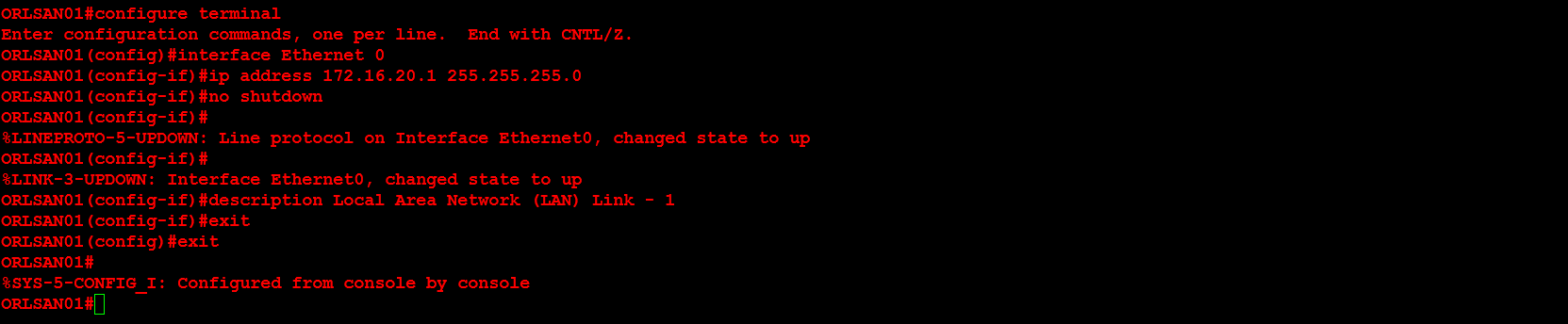
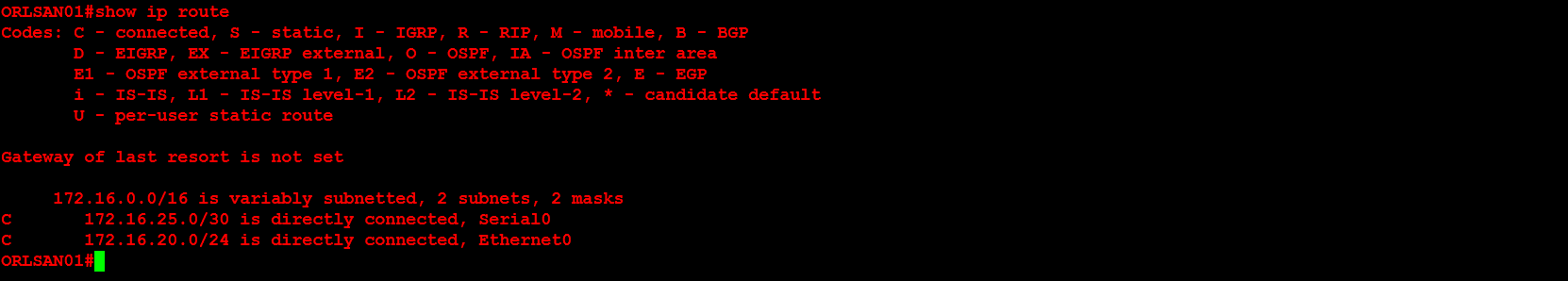


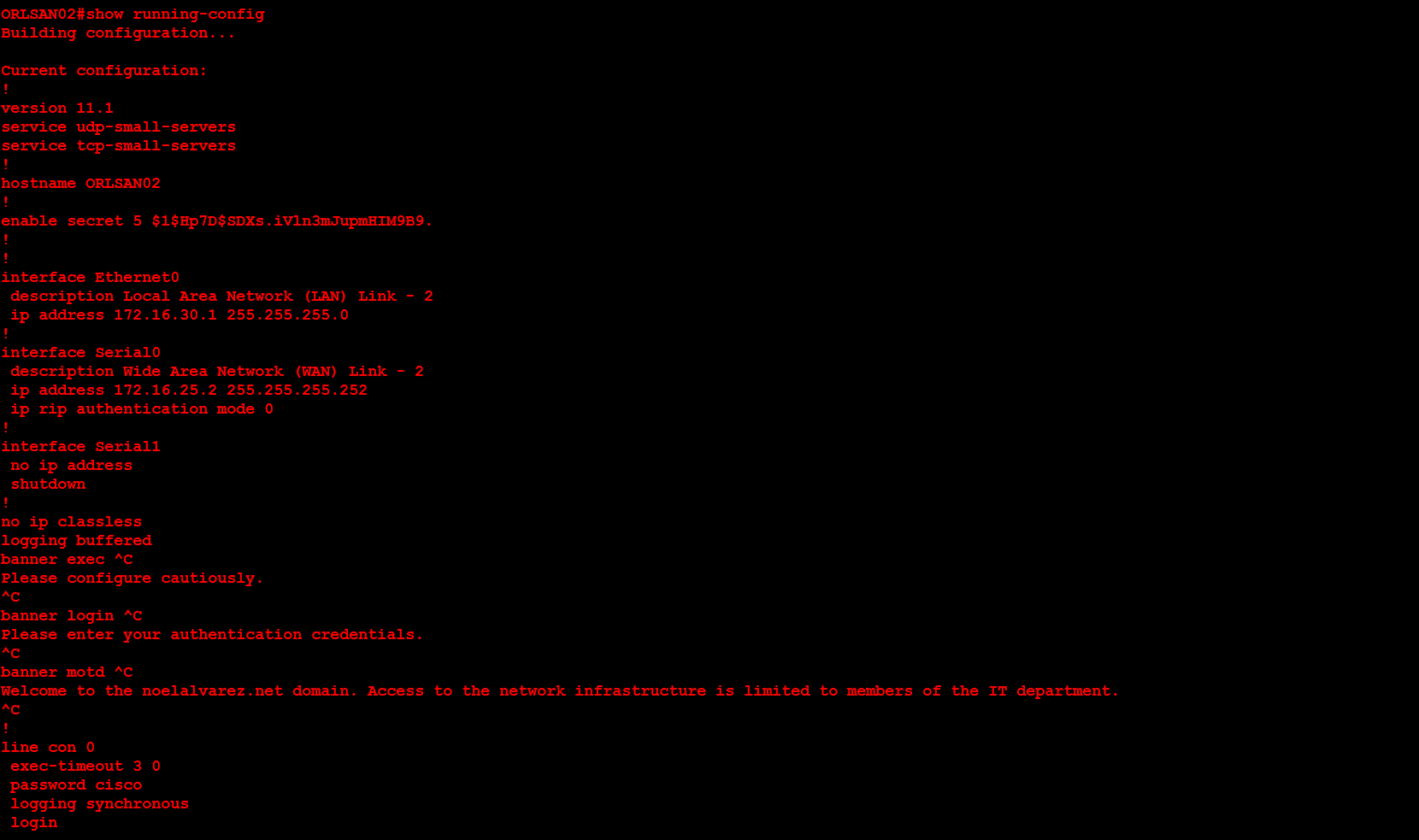



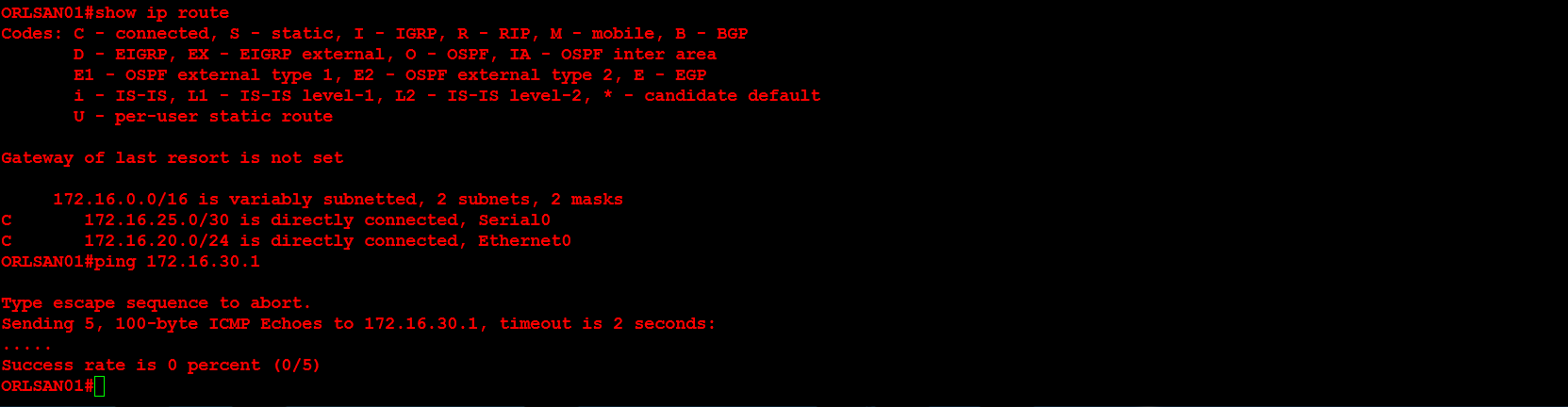
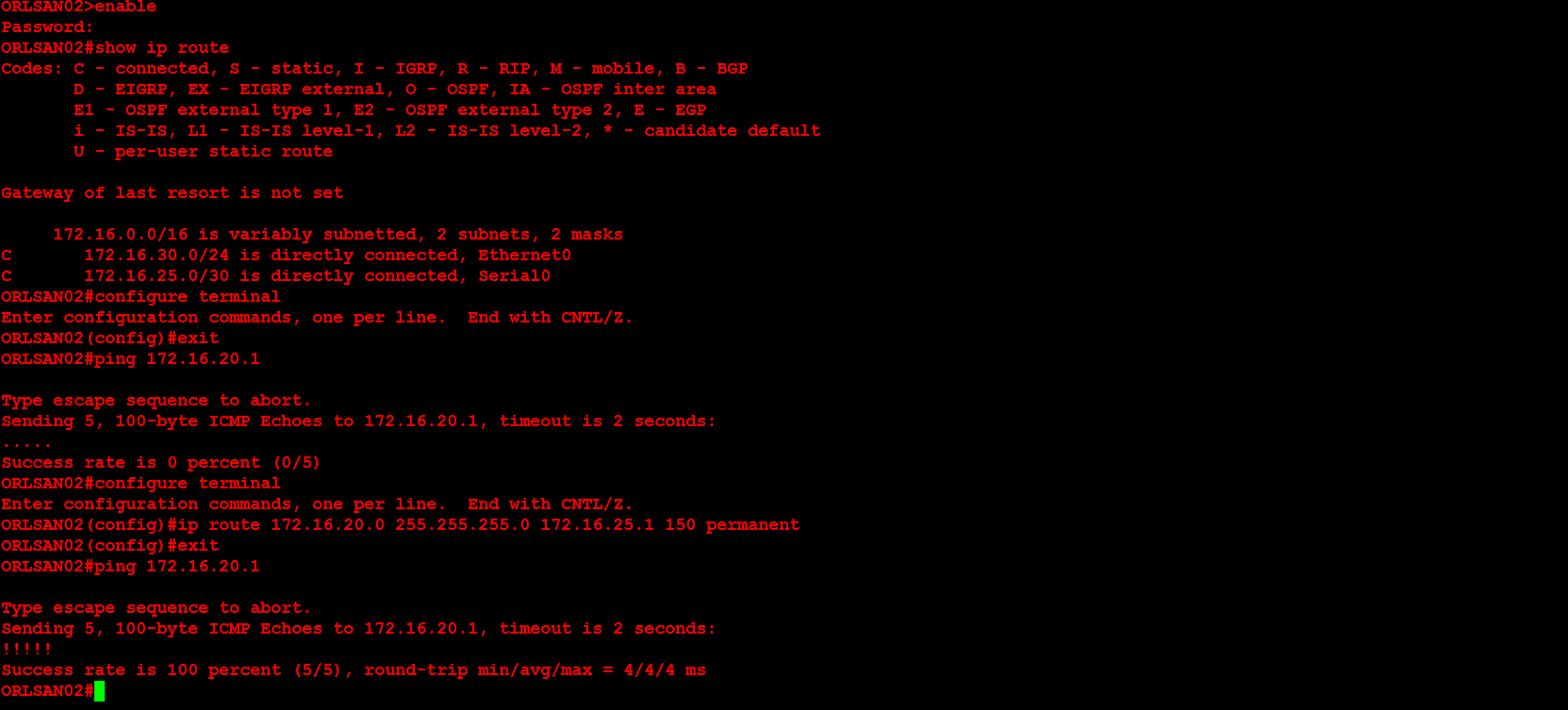
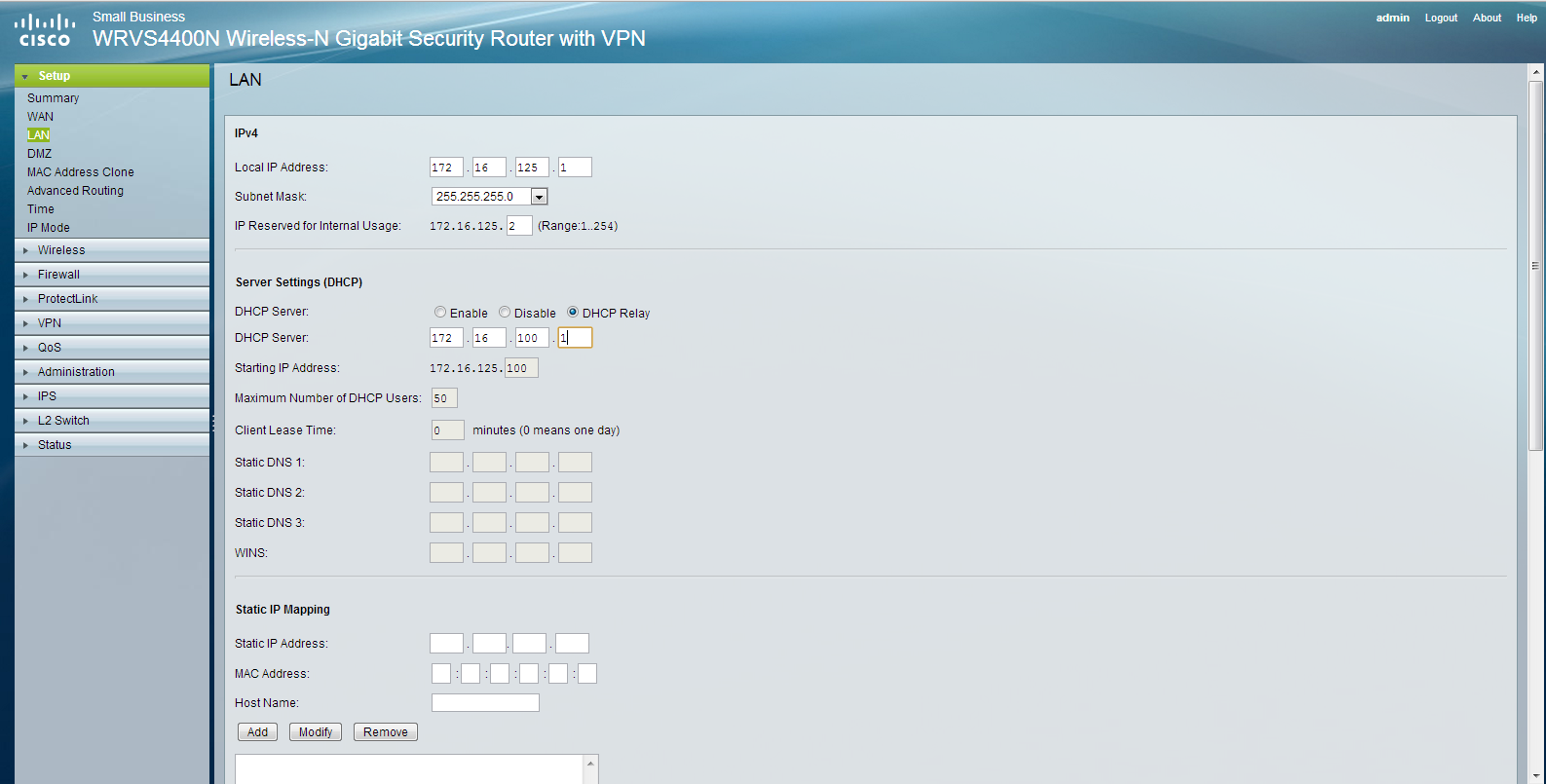
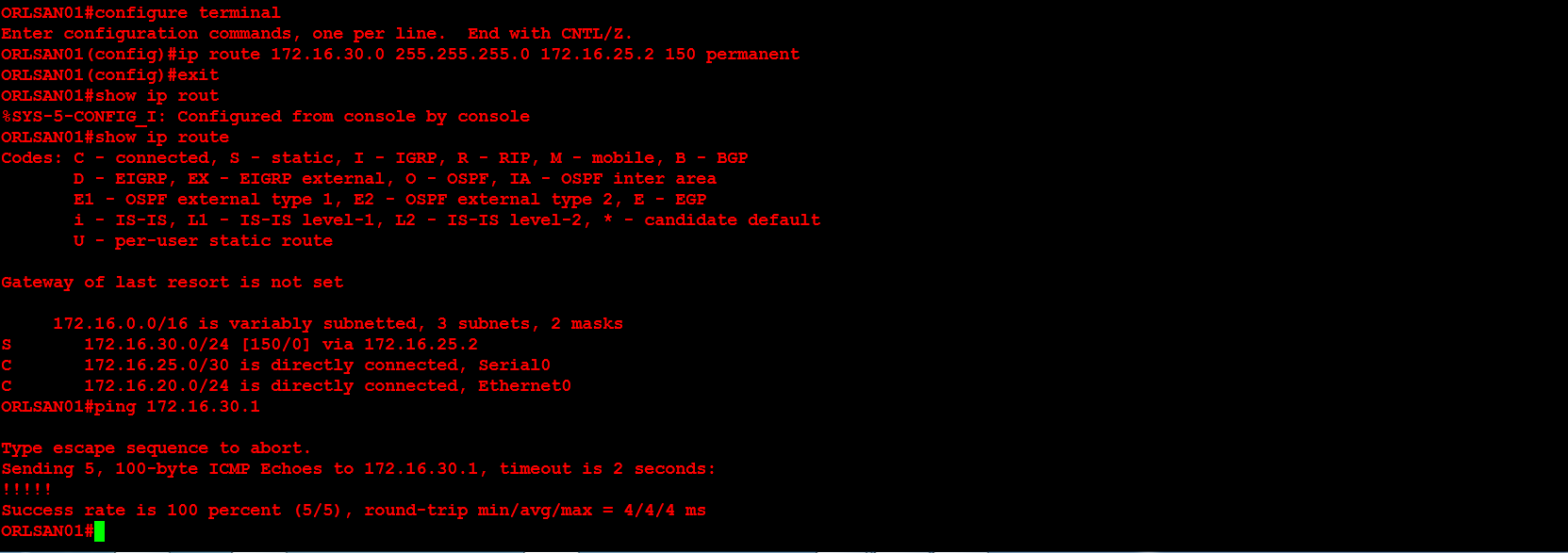 Next, I will configure ORLSAN02 with a static route to the 172.16.20.0/24 network, verify the route is in the routing table then ping 172.16.20.1.
Next, I will configure ORLSAN02 with a static route to the 172.16.20.0/24 network, verify the route is in the routing table then ping 172.16.20.1.