At my existing employer, it was brought to my attention that a number of VMware virtual machines running the Microsoft Windows 10 operating system were randomly dropping off the network, upon reboot. Viewing the properties of the network adapter confirmed that they were assigned static IP addresses. However, running ipconfig from the command prompt showed that they were assigned 169.254.x.x IP addresses.
Upon reviewing the logs I found the following error message: “The system detected an address conflict for IP address 0.0.0.0 with the system having network hardware address XX-XX-XX-XX-XX-XX. Network operations on this system may be disrupted as a result.” The XX-XX-XX-XX-XX-XX is the MAC address of a Cisco switch.
In summary, the root cause of this is Windows 10 performing an ARP probe at the time as the Cisco switch performing an ARP probe in order to maintain the IP device-tracking cache during IP device tracking. The Windows 10 host believes another node on the network is probing the address it’s assigned and must treat it as an IP address conflict.
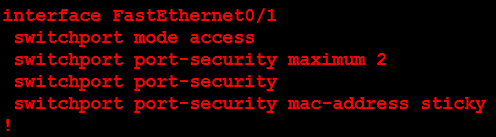
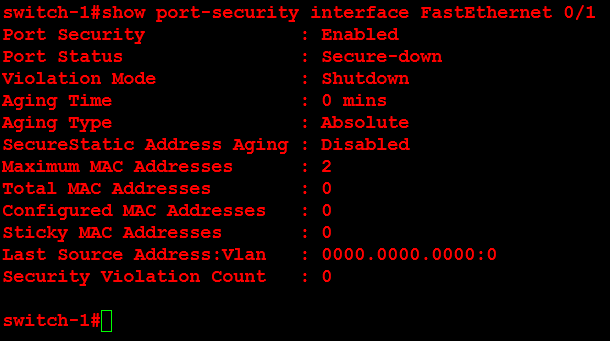
The solution is to disable gratuitous ARPs on the switch or in the Windows 10 operating system. We chose to disable the gratuitous ARP in the Windows 10 operating system.
Additionally, more information may be found using the links below.

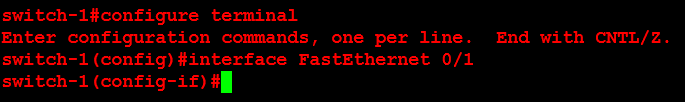
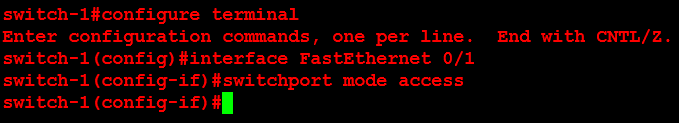
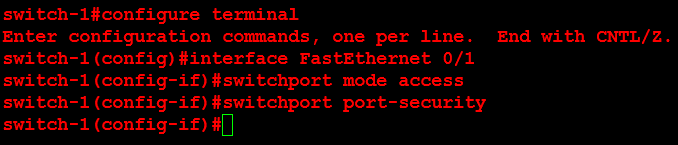
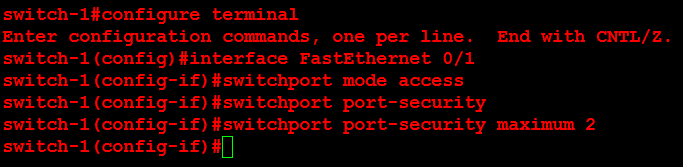
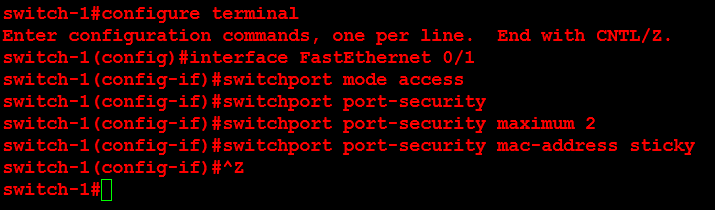
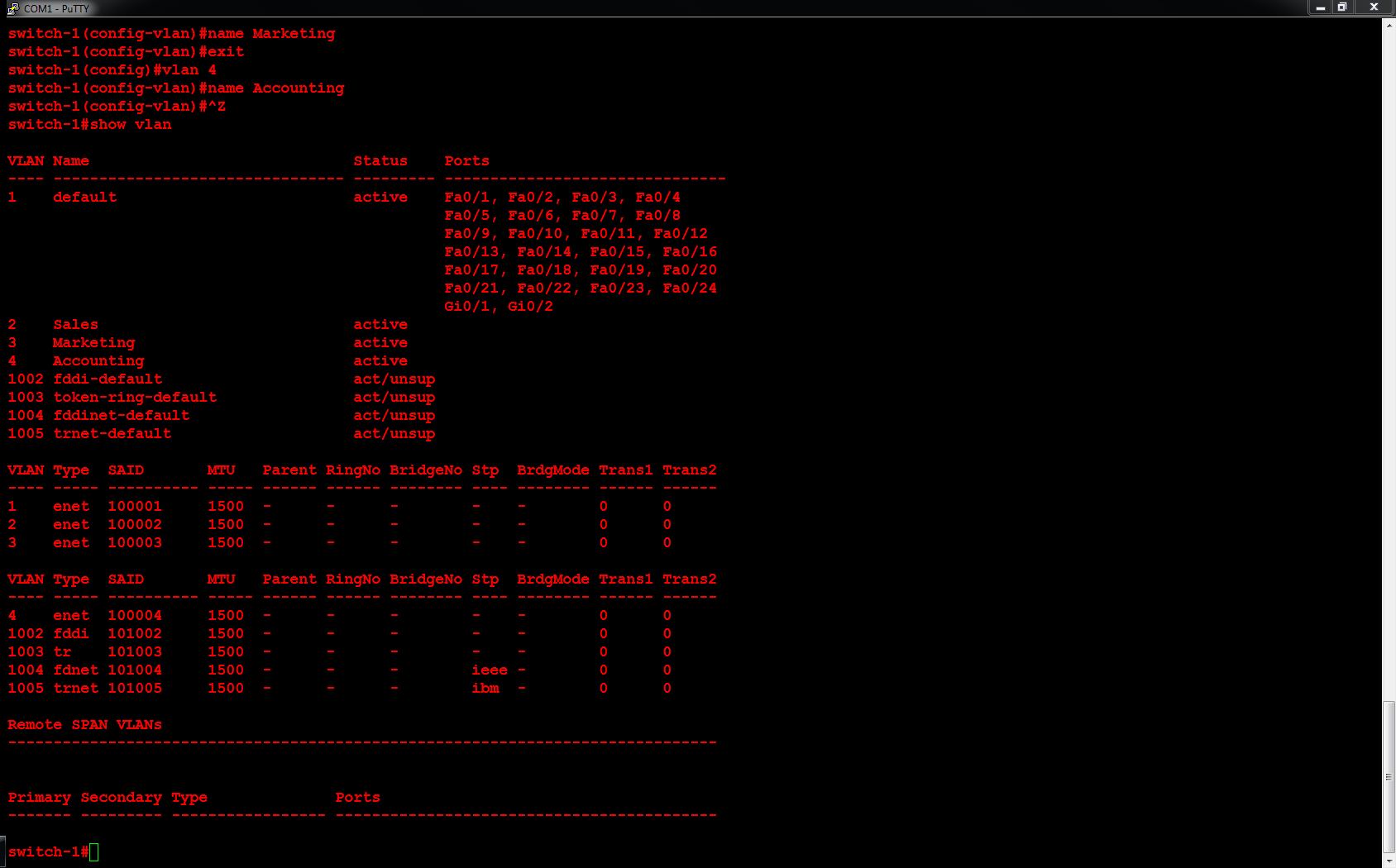
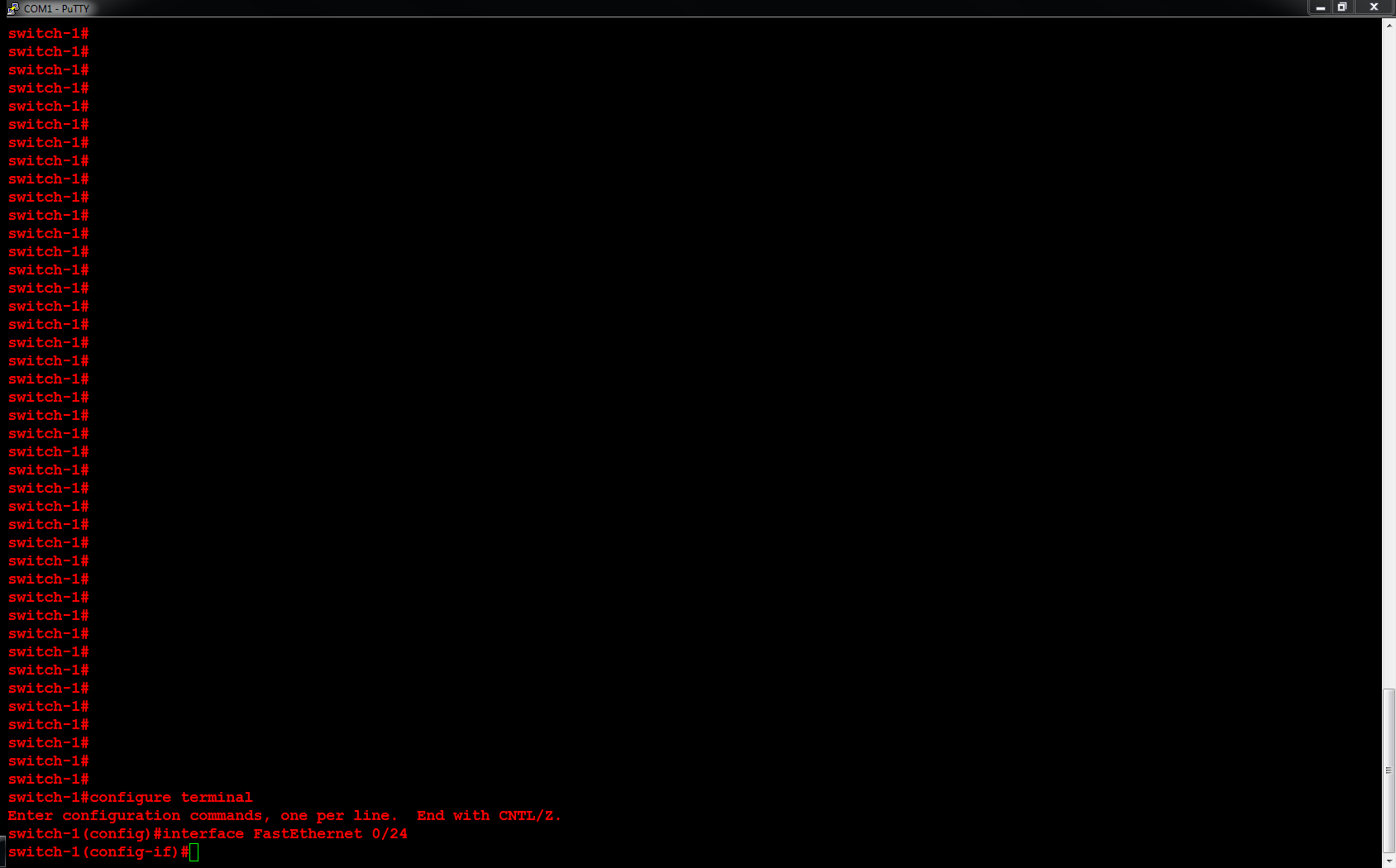
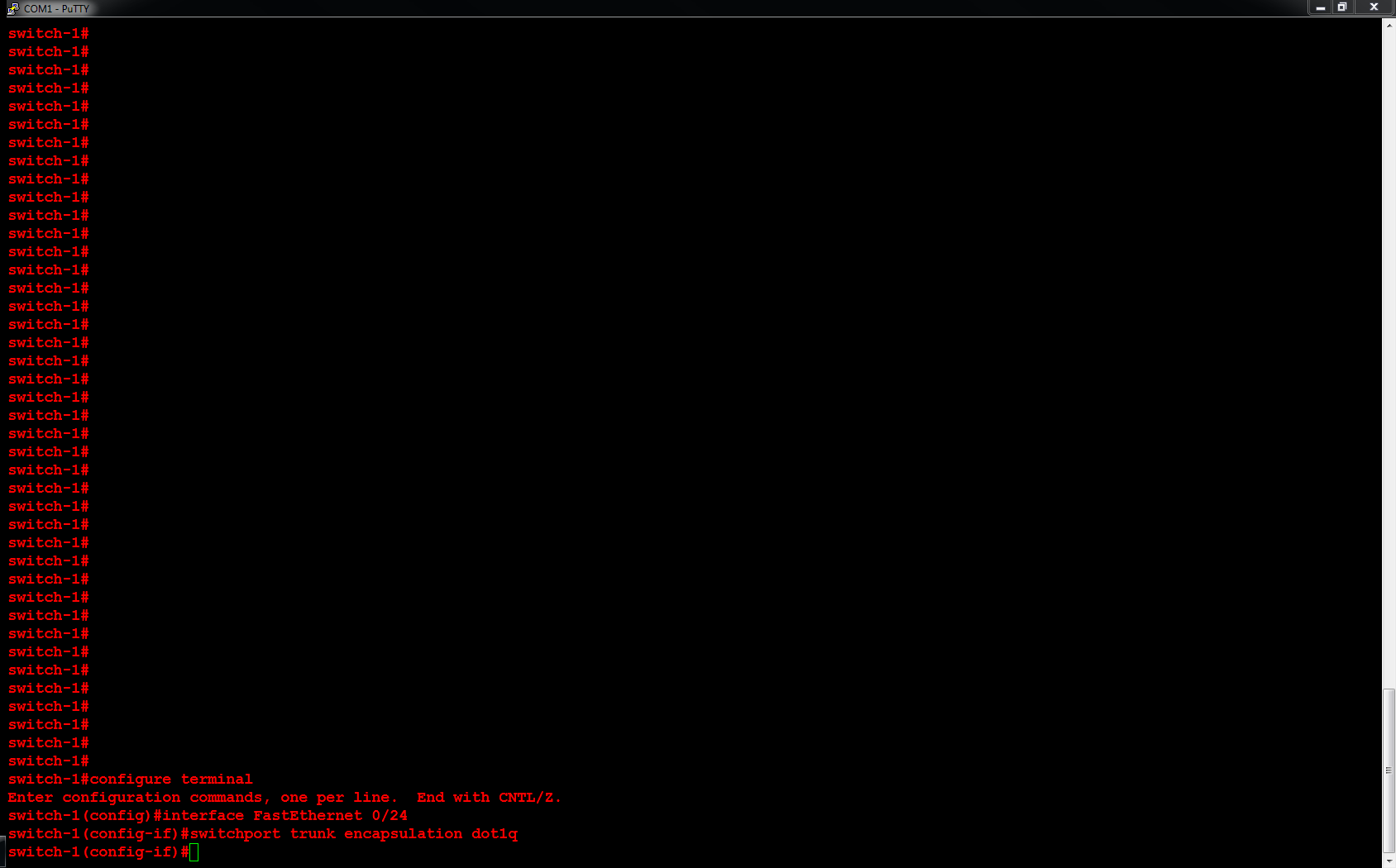
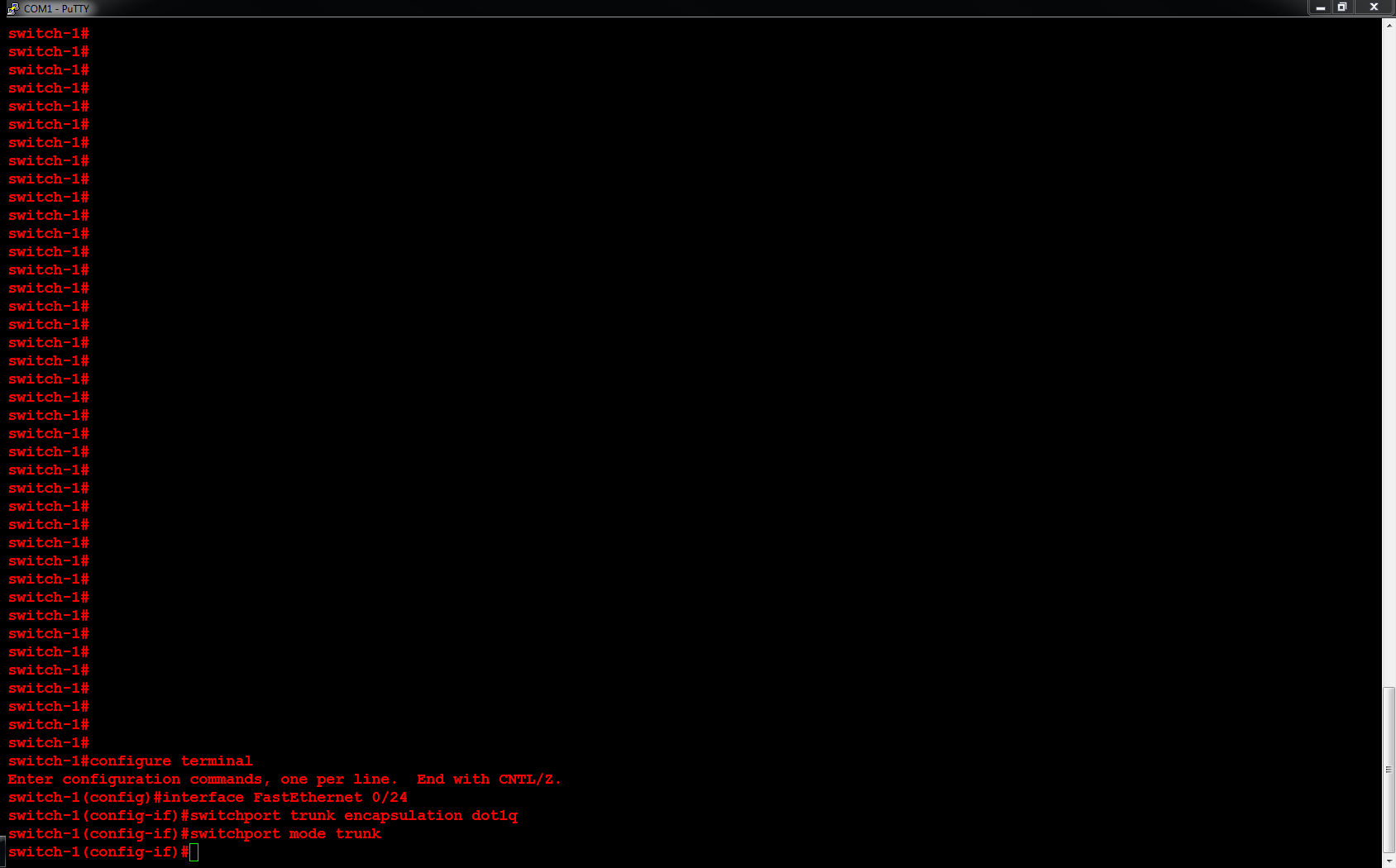


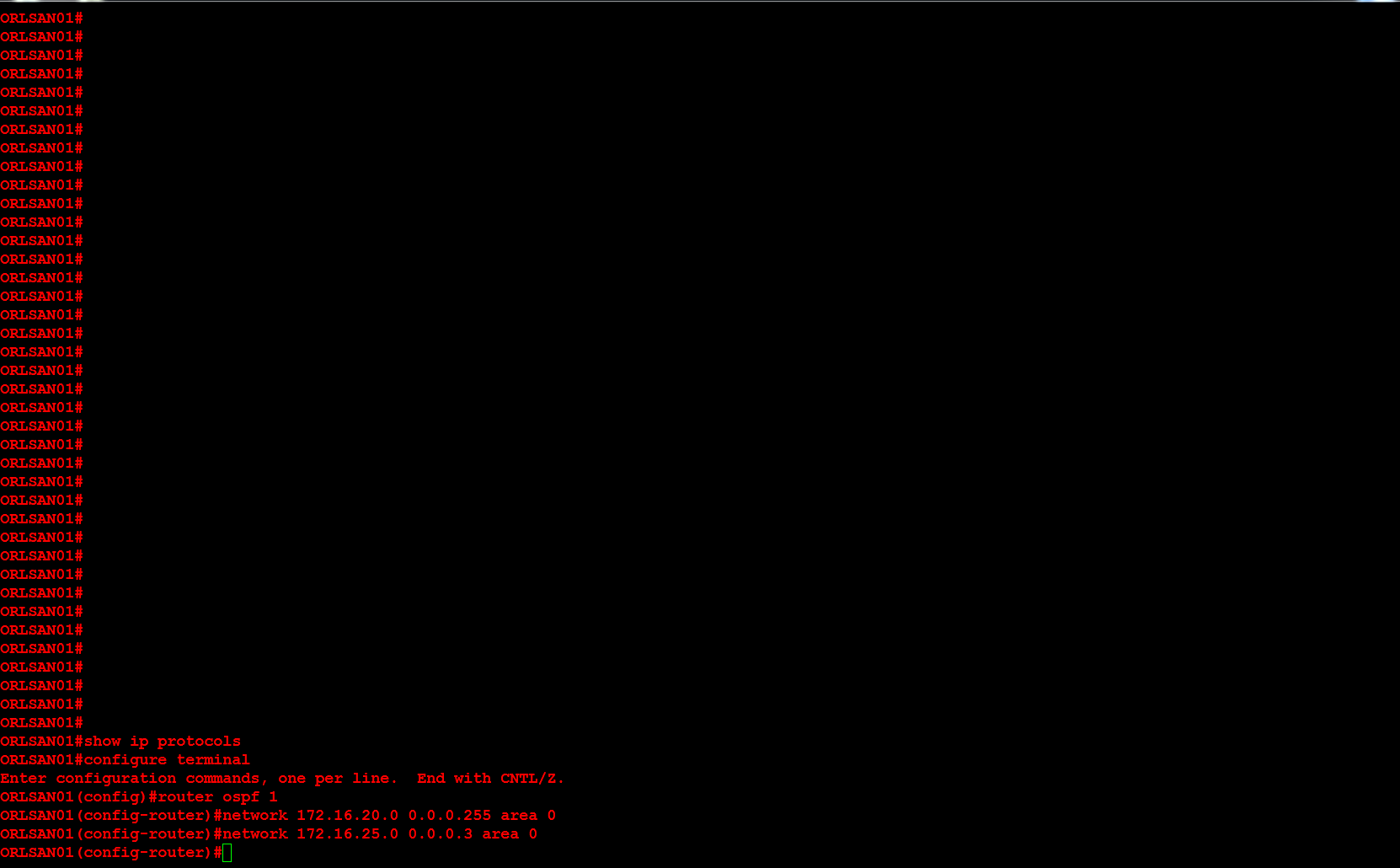

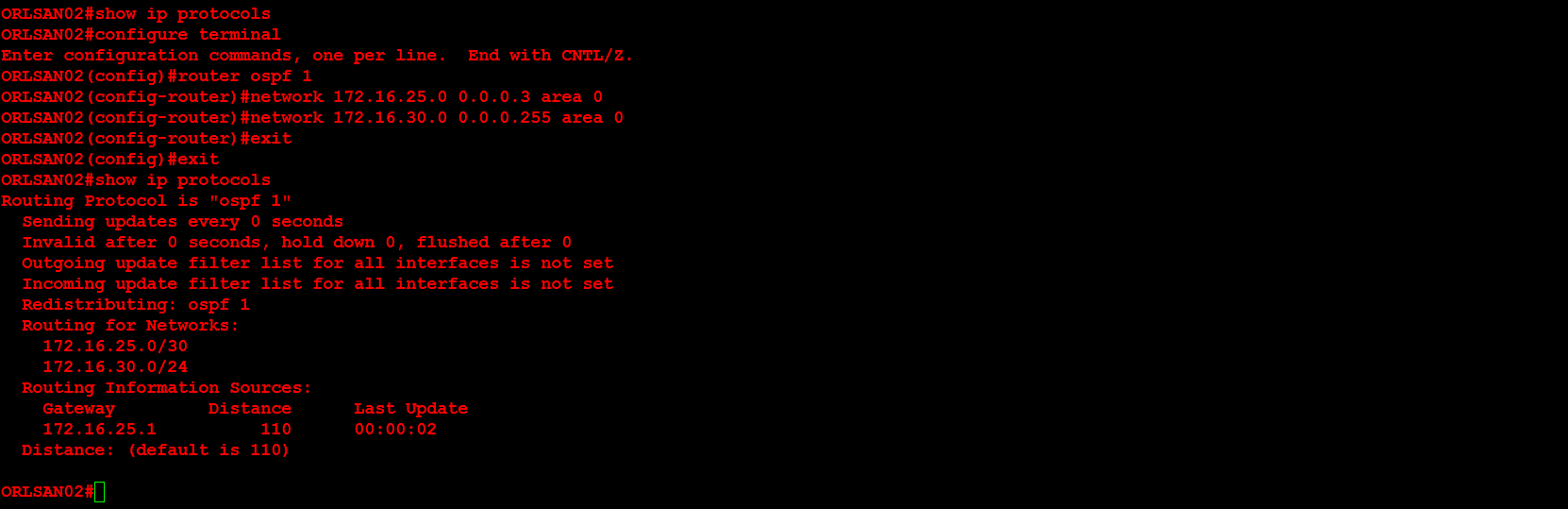
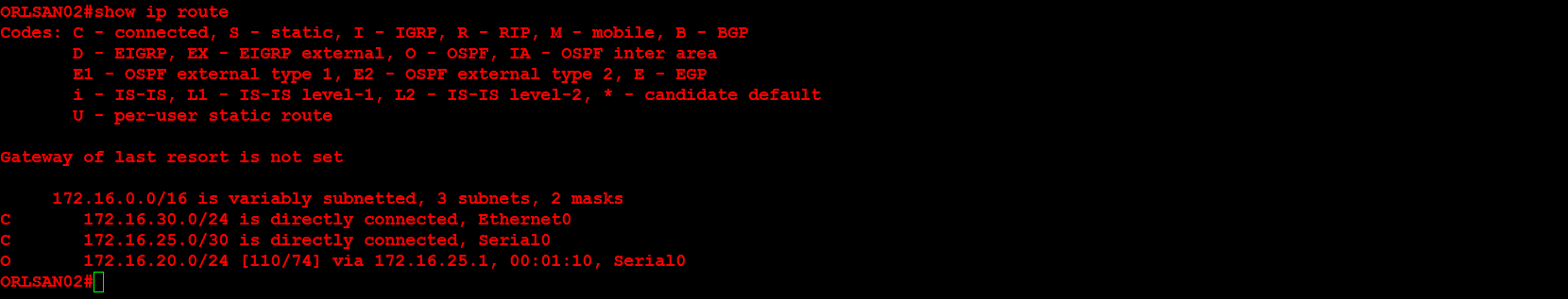

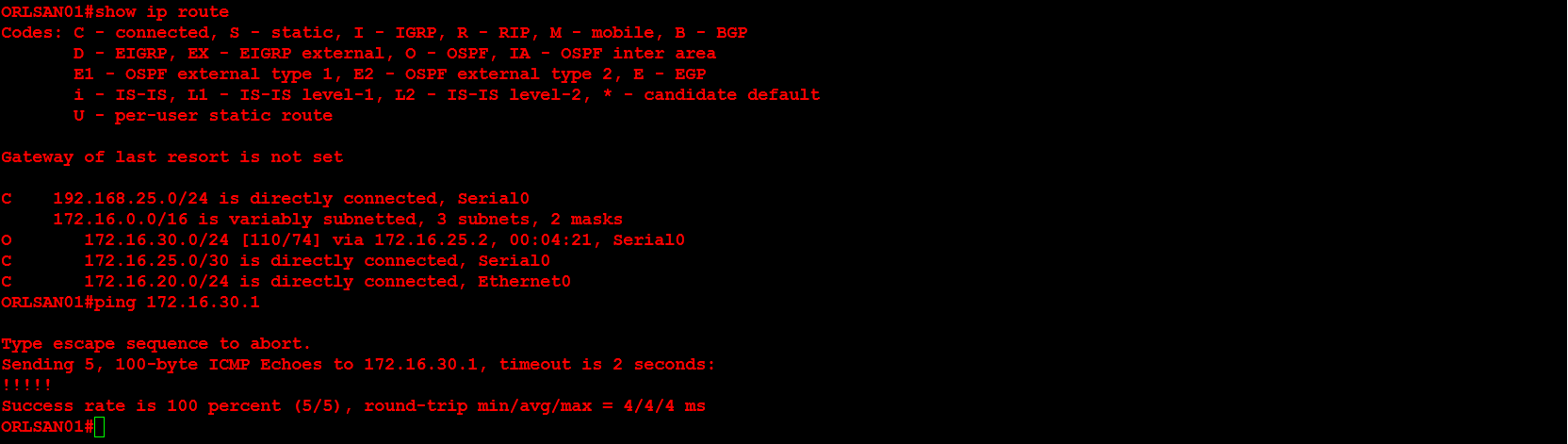



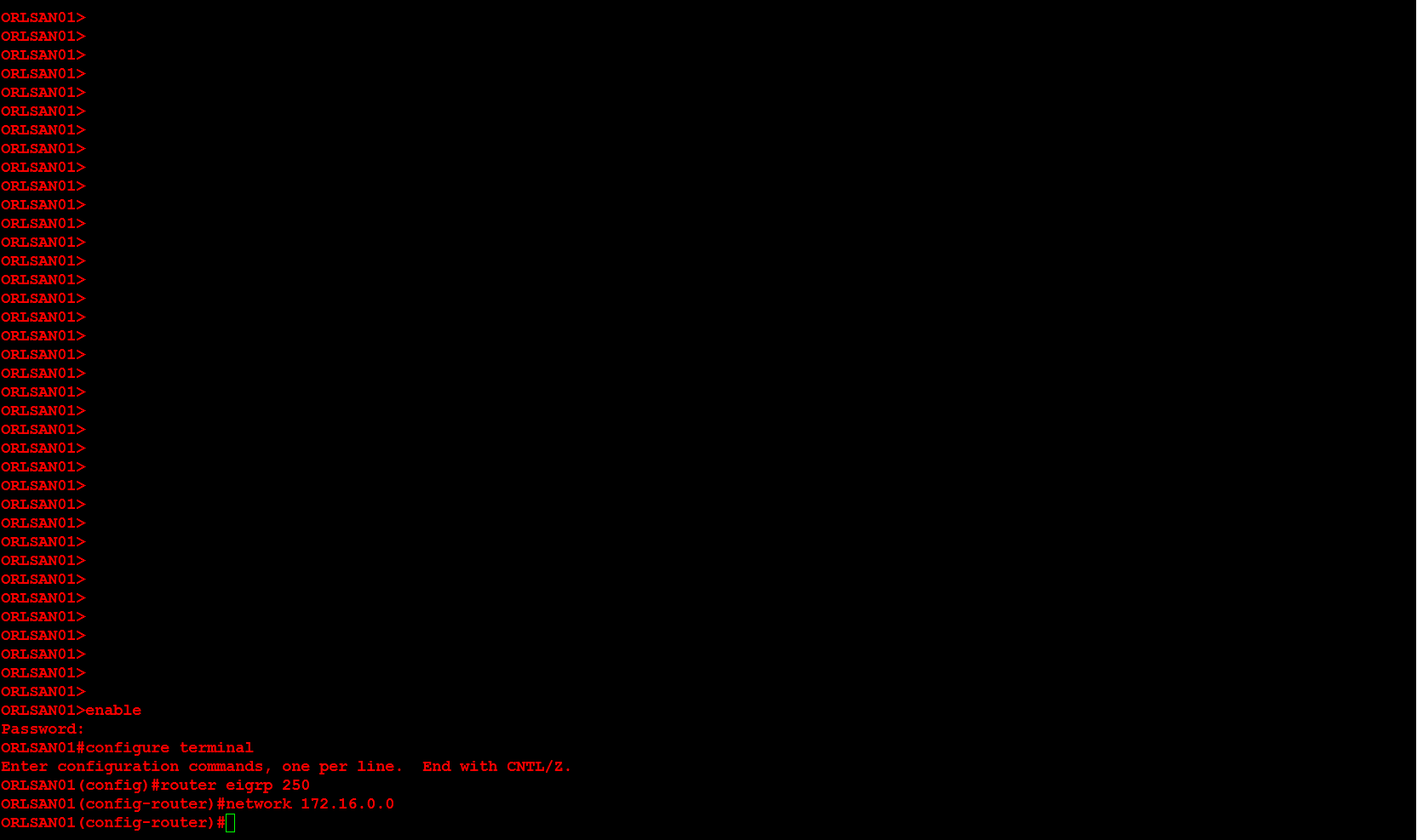
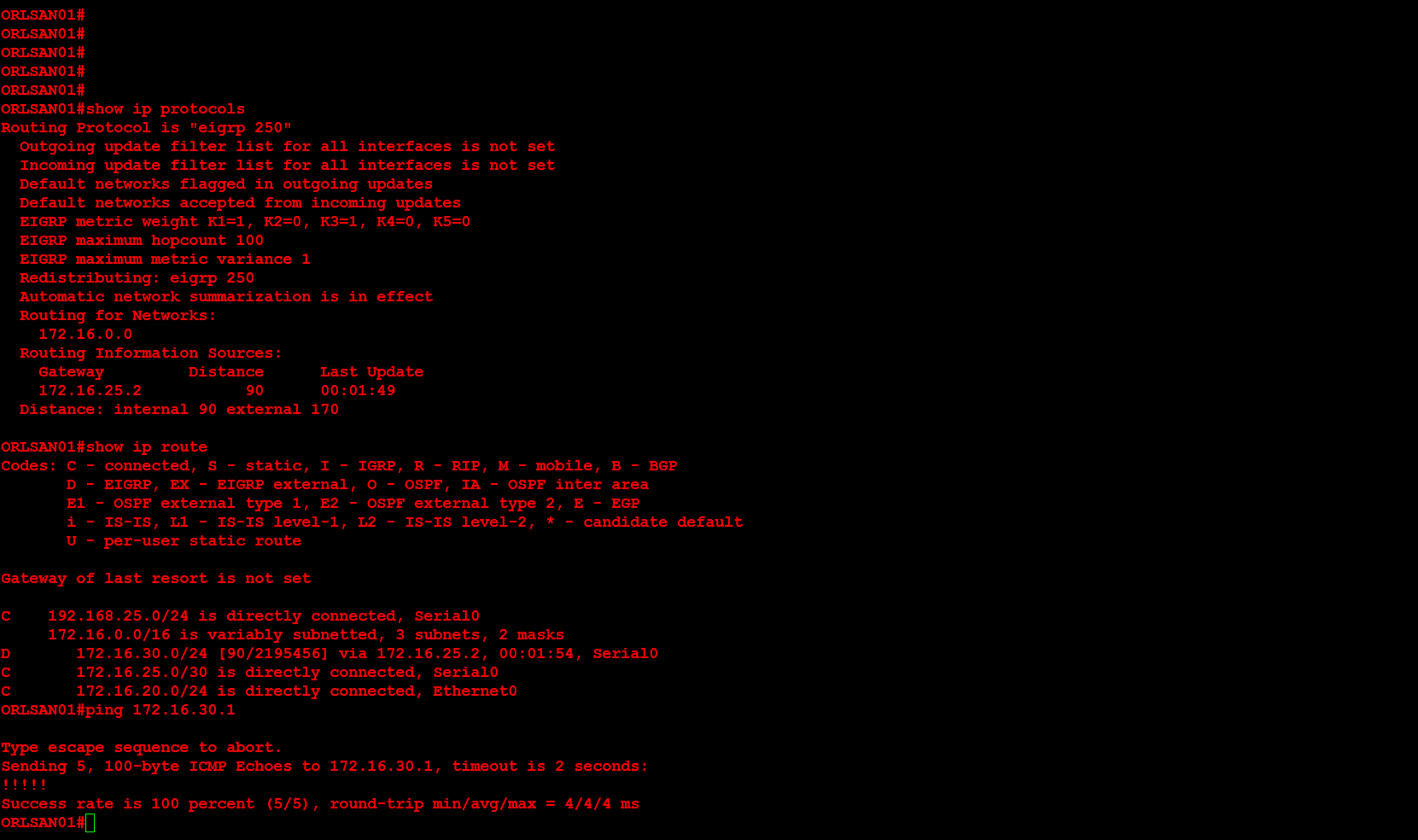





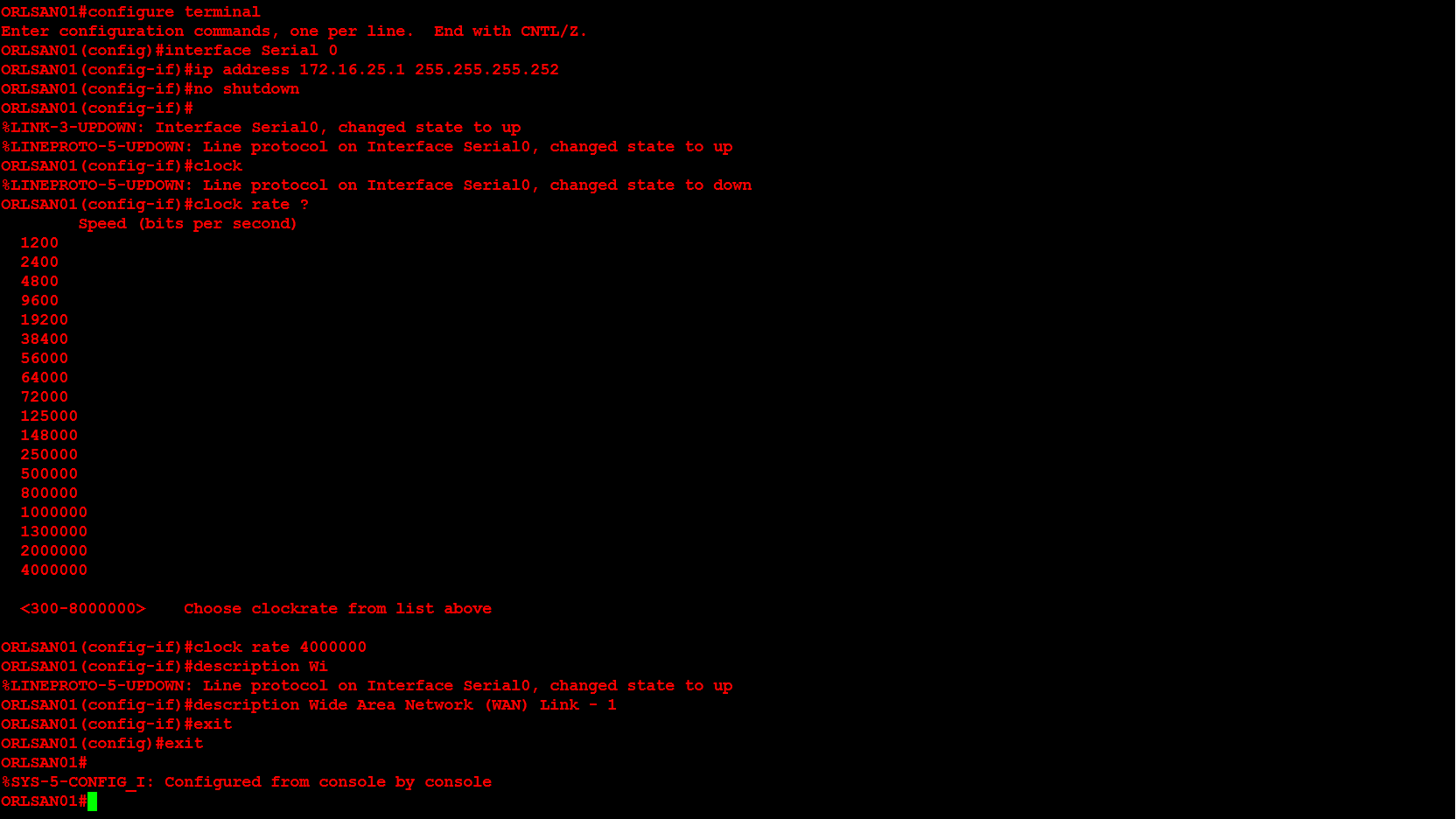
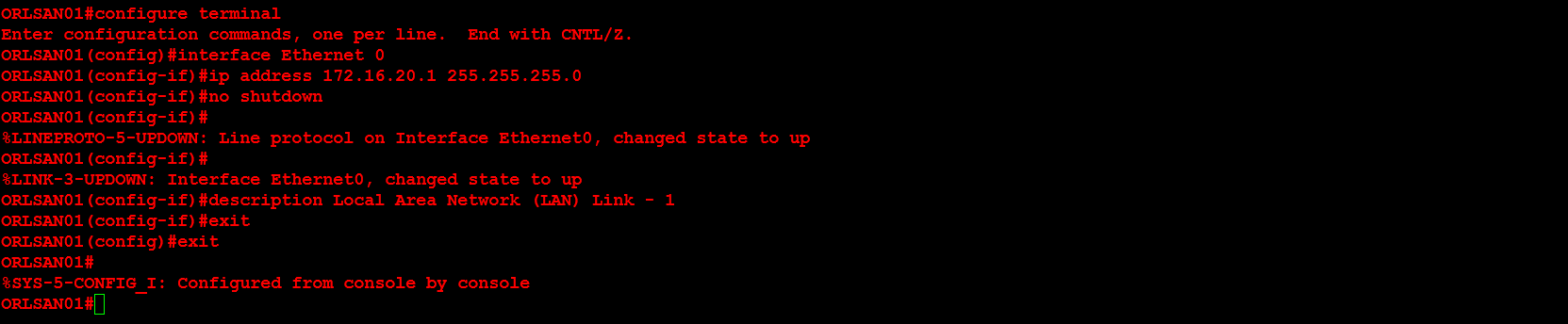
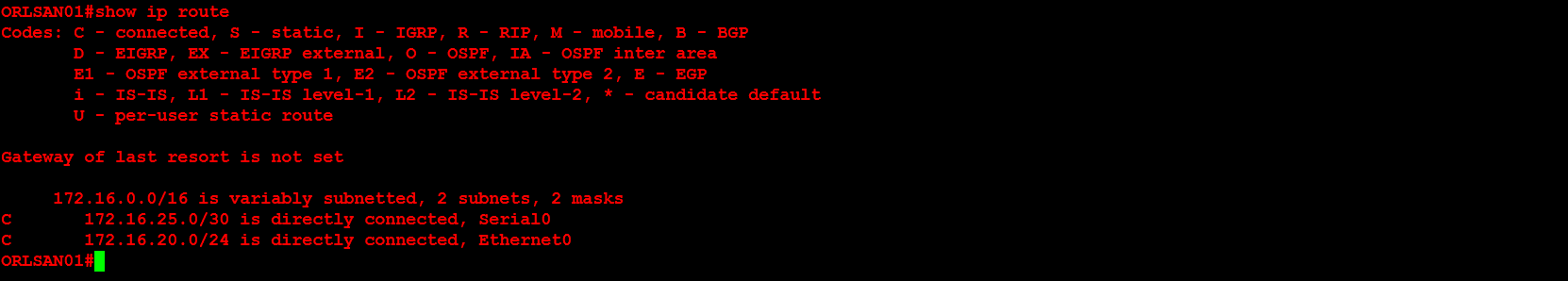


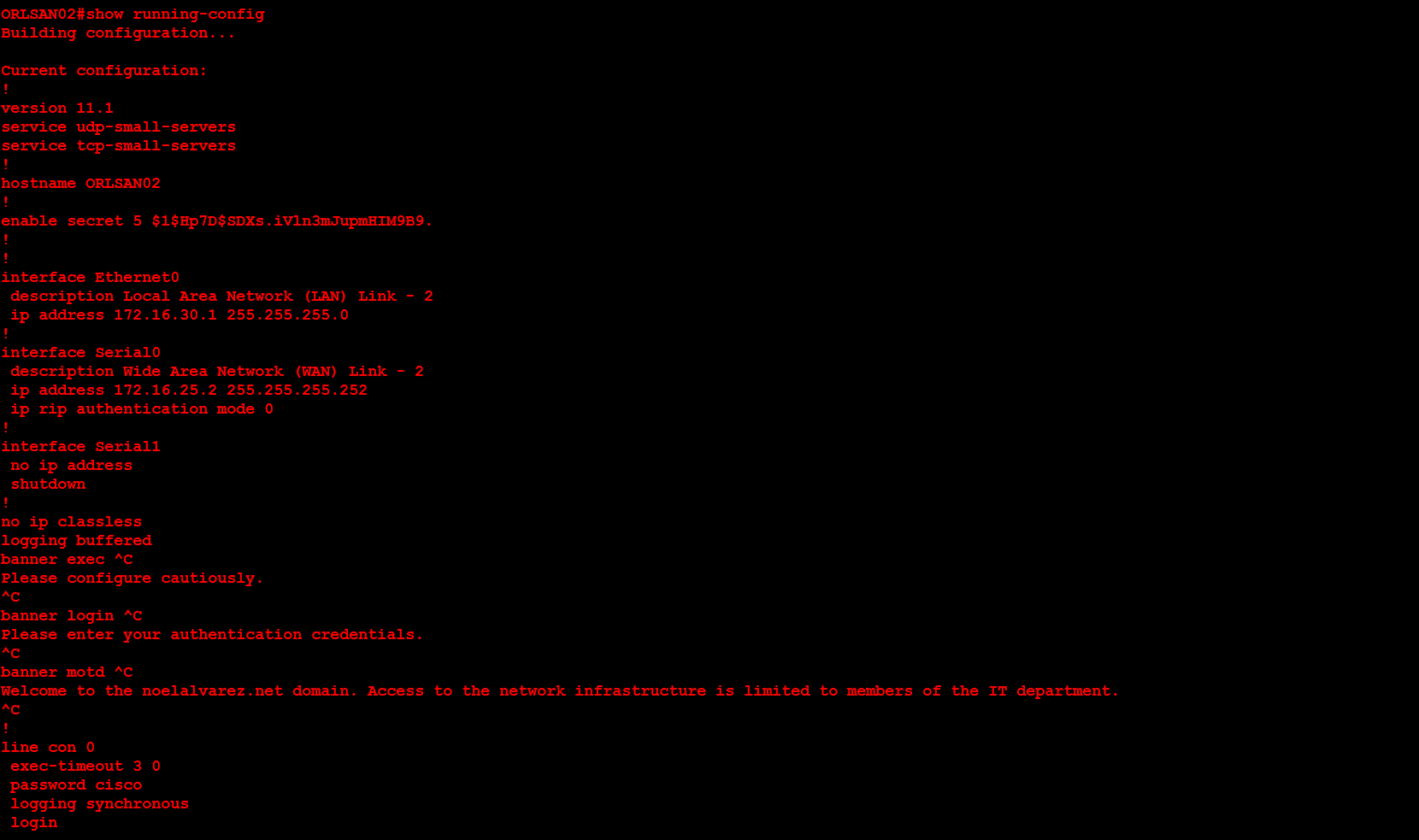



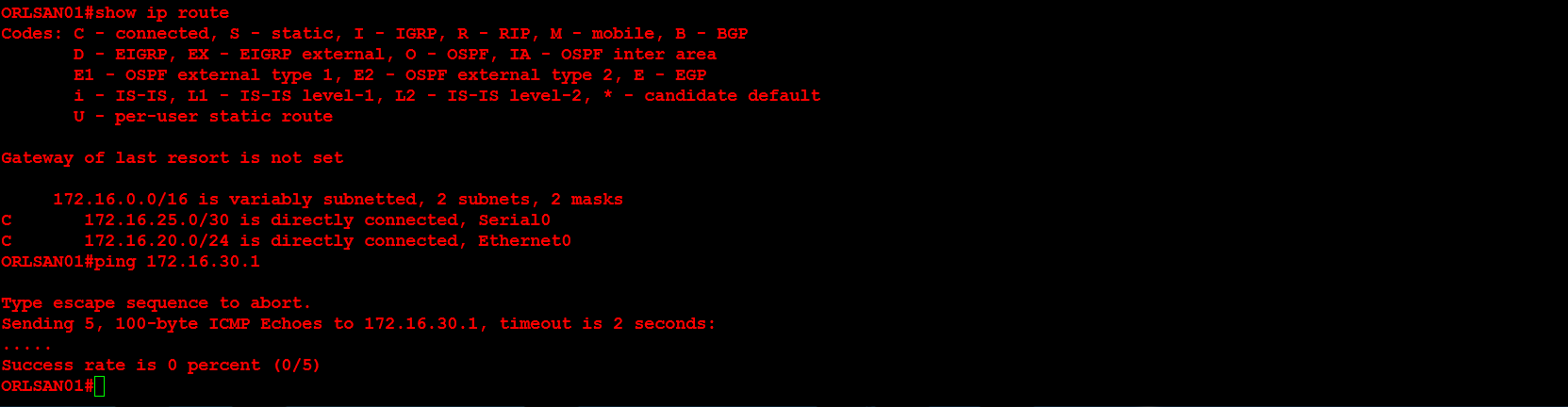
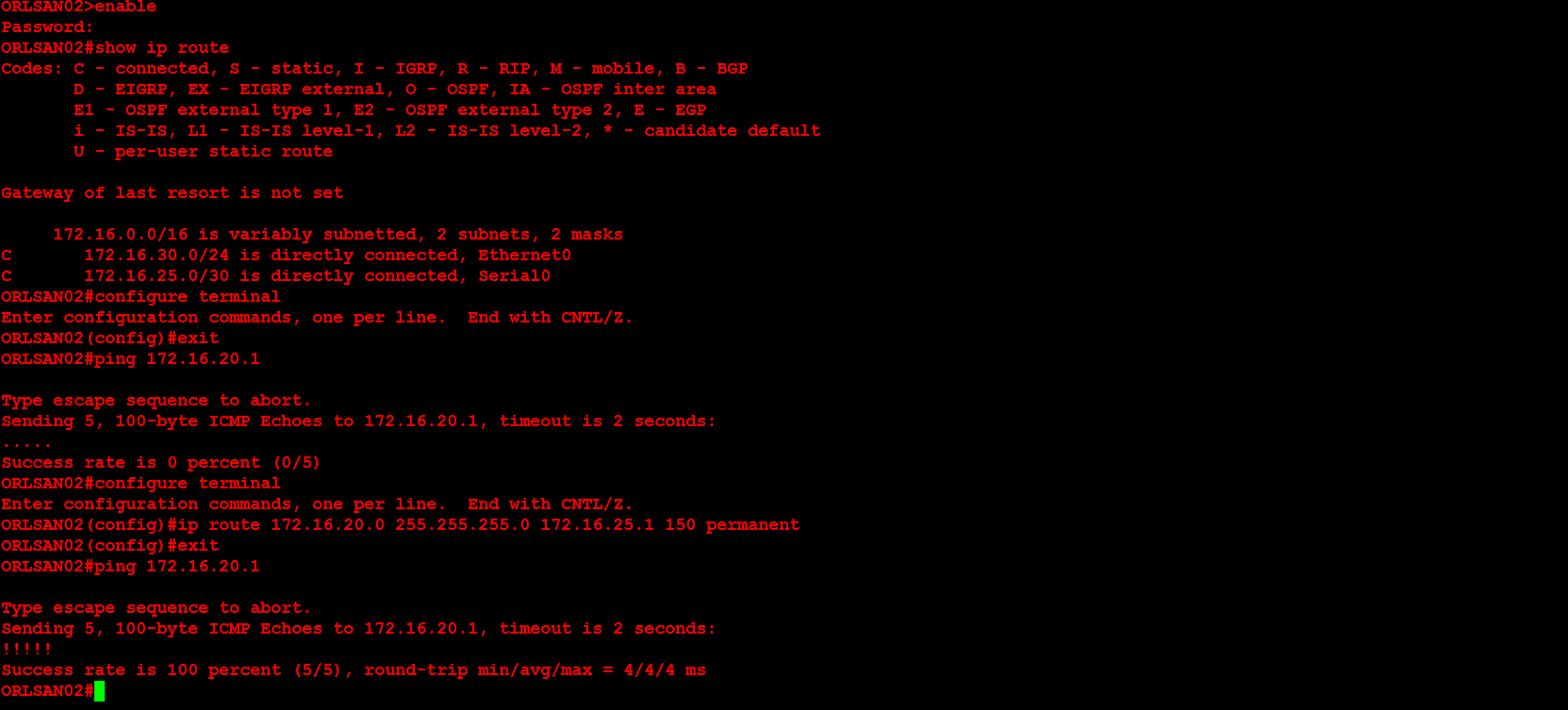
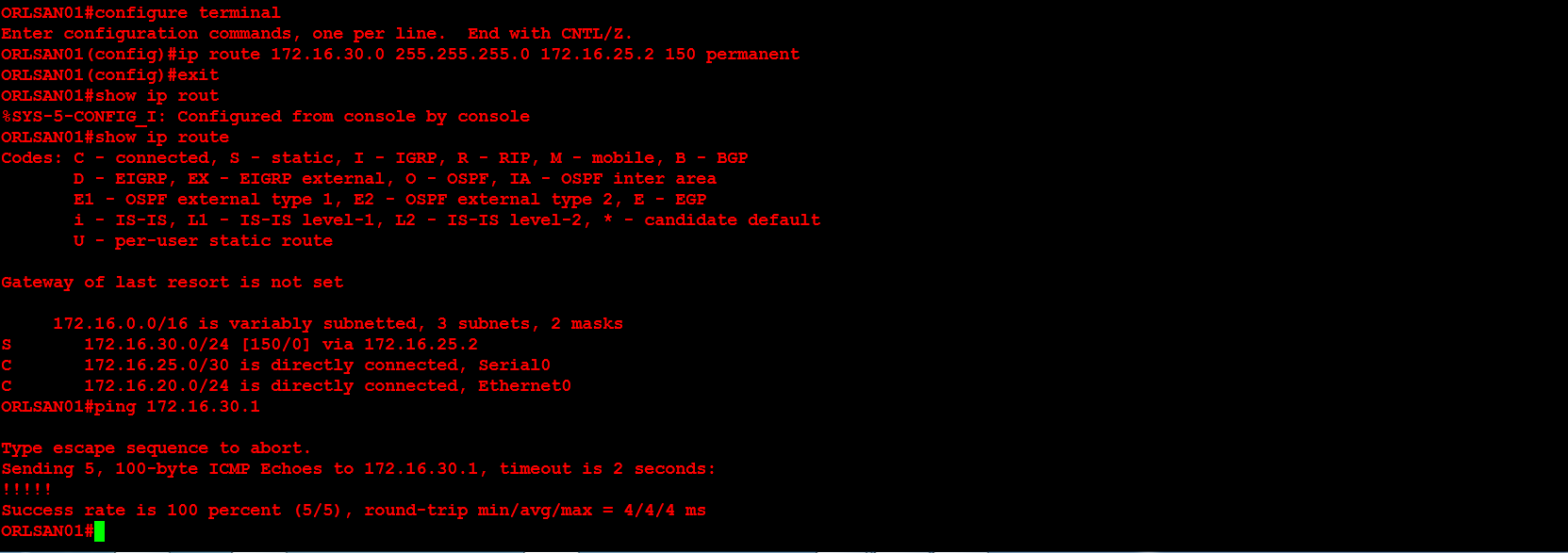 Next, I will configure ORLSAN02 with a static route to the 172.16.20.0/24 network, verify the route is in the routing table then ping 172.16.20.1.
Next, I will configure ORLSAN02 with a static route to the 172.16.20.0/24 network, verify the route is in the routing table then ping 172.16.20.1.