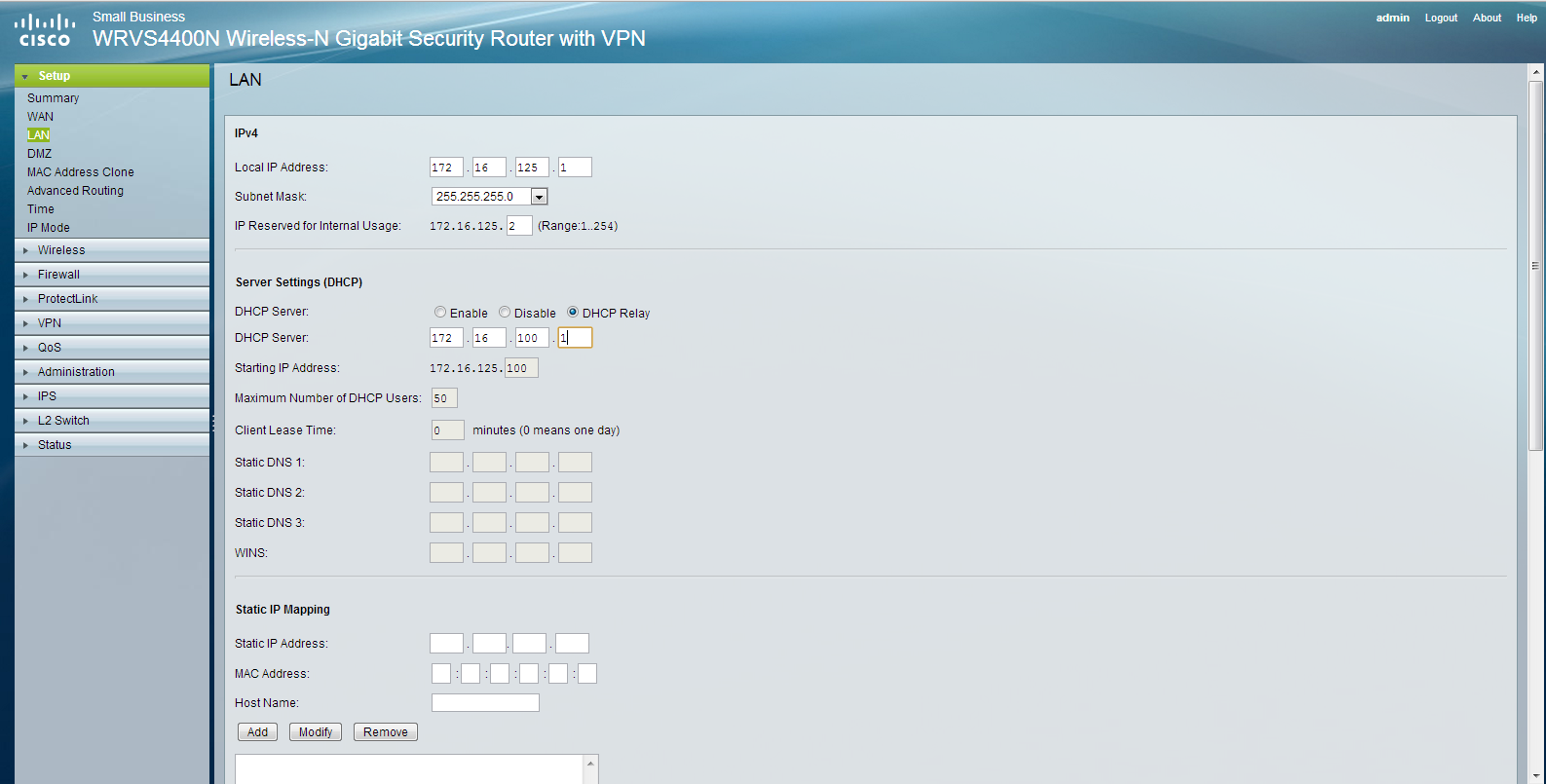
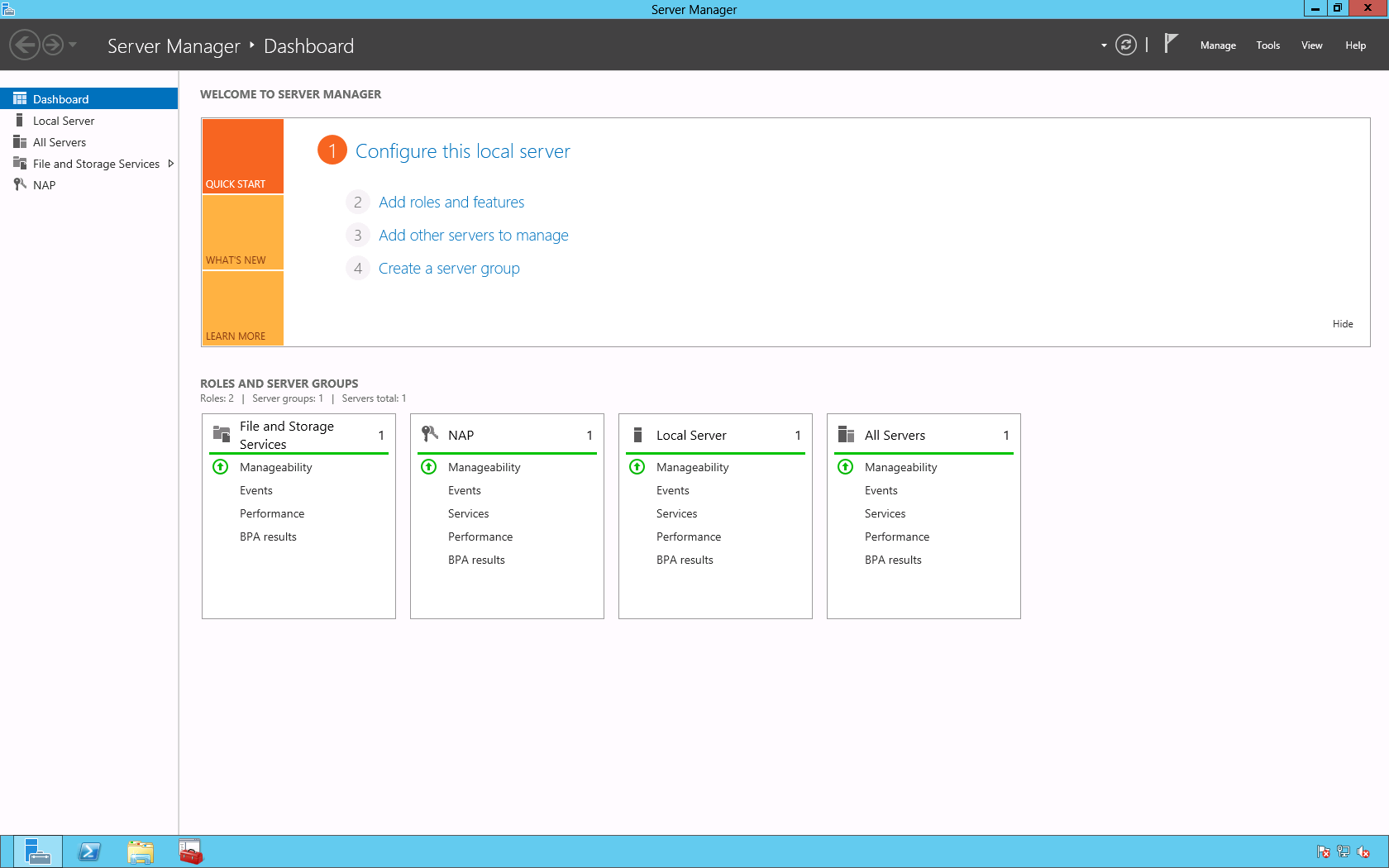
You may use the following method to install the File Server role on a server that is running the Windows Server 2012 operating system.
On the default menu of the Server Manager GUI click the Add roles and features option.
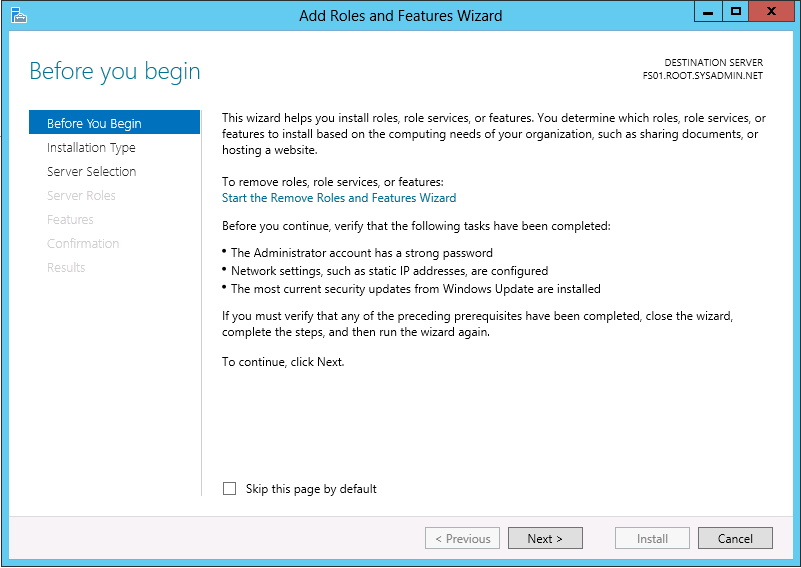
When the Add Roles and Features Wizard dialog box opens click Next > on the Before You Begin page.
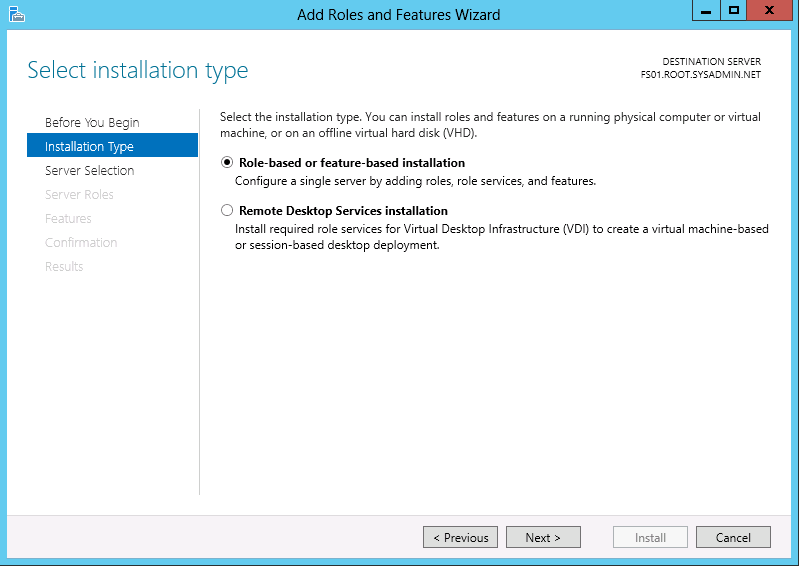
On the Installation Type page select Role-based or feature-based installation.
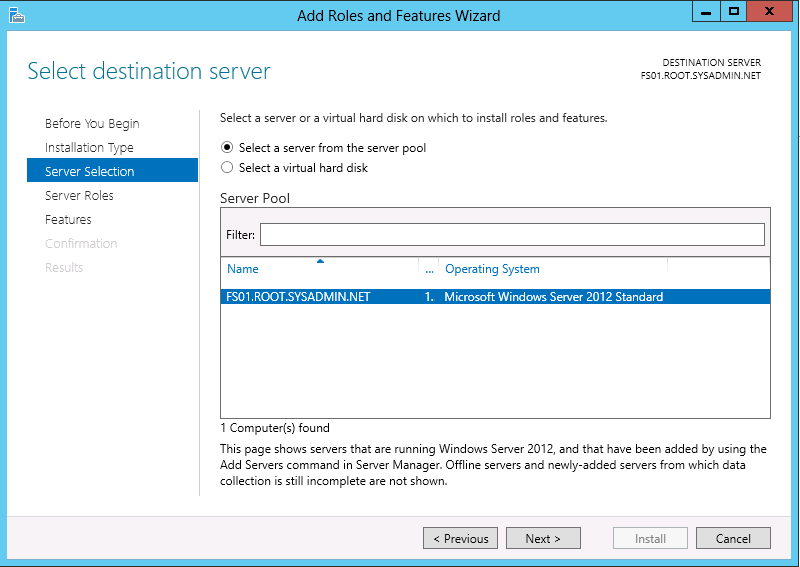
On the Server Selection page use the Select a server from the server pool radio button and choose the correct server and click Next >.
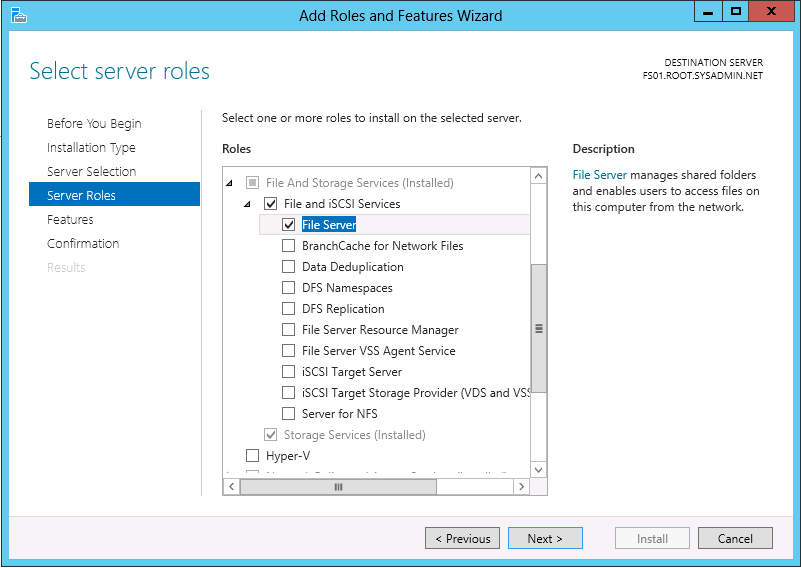
On the Server Roles page navigate to File And Storage Services > File and iSCSI Services and check the box to select File Server then click Next >.
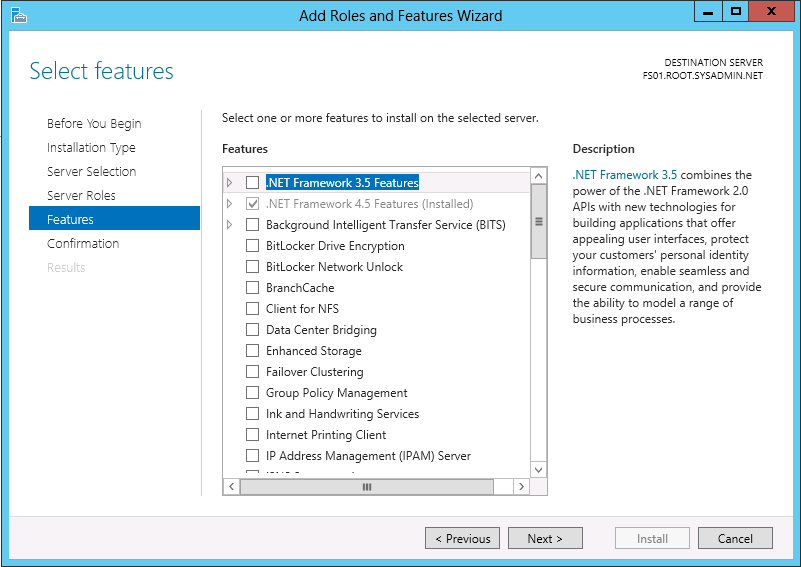
On the Features page click Next >.
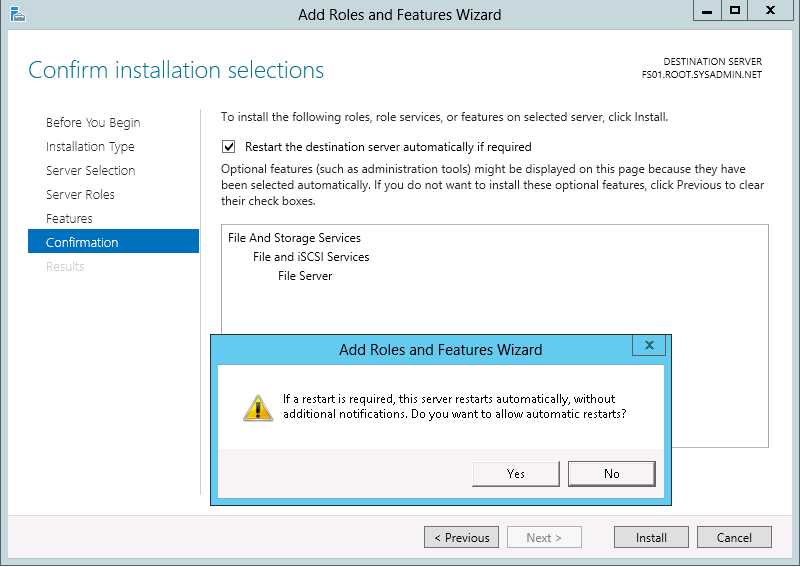
On the Confirmation page select the check box to Restart the destination server automatically if required and click Yes in the Add Roles and Features Wizard prompt then click Install.
On the Results page click Close.
Enjoy!
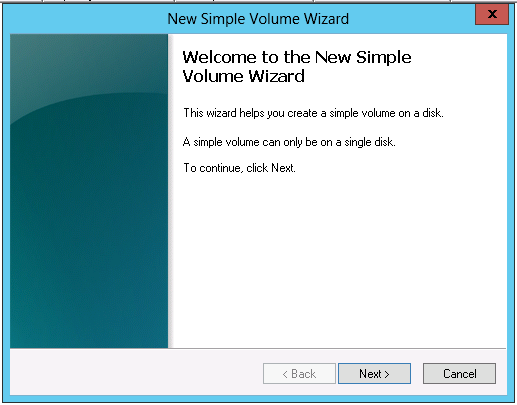
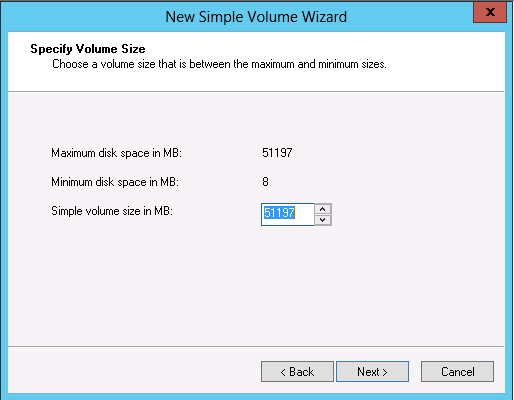
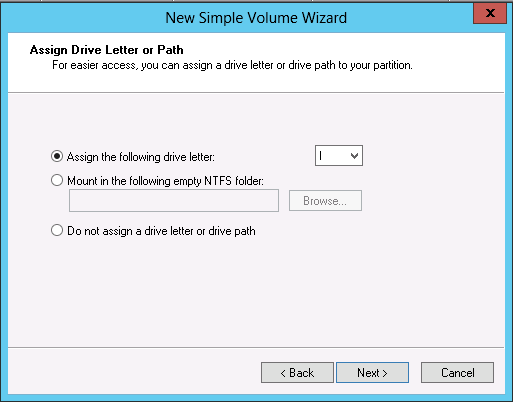
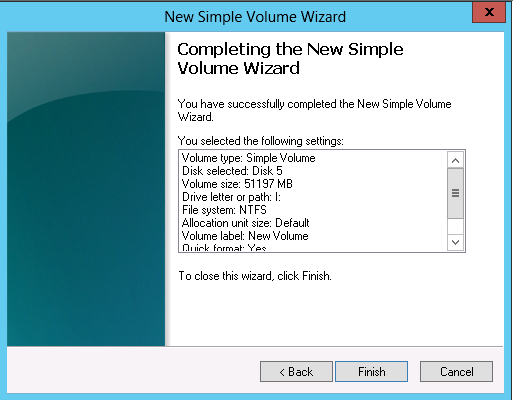
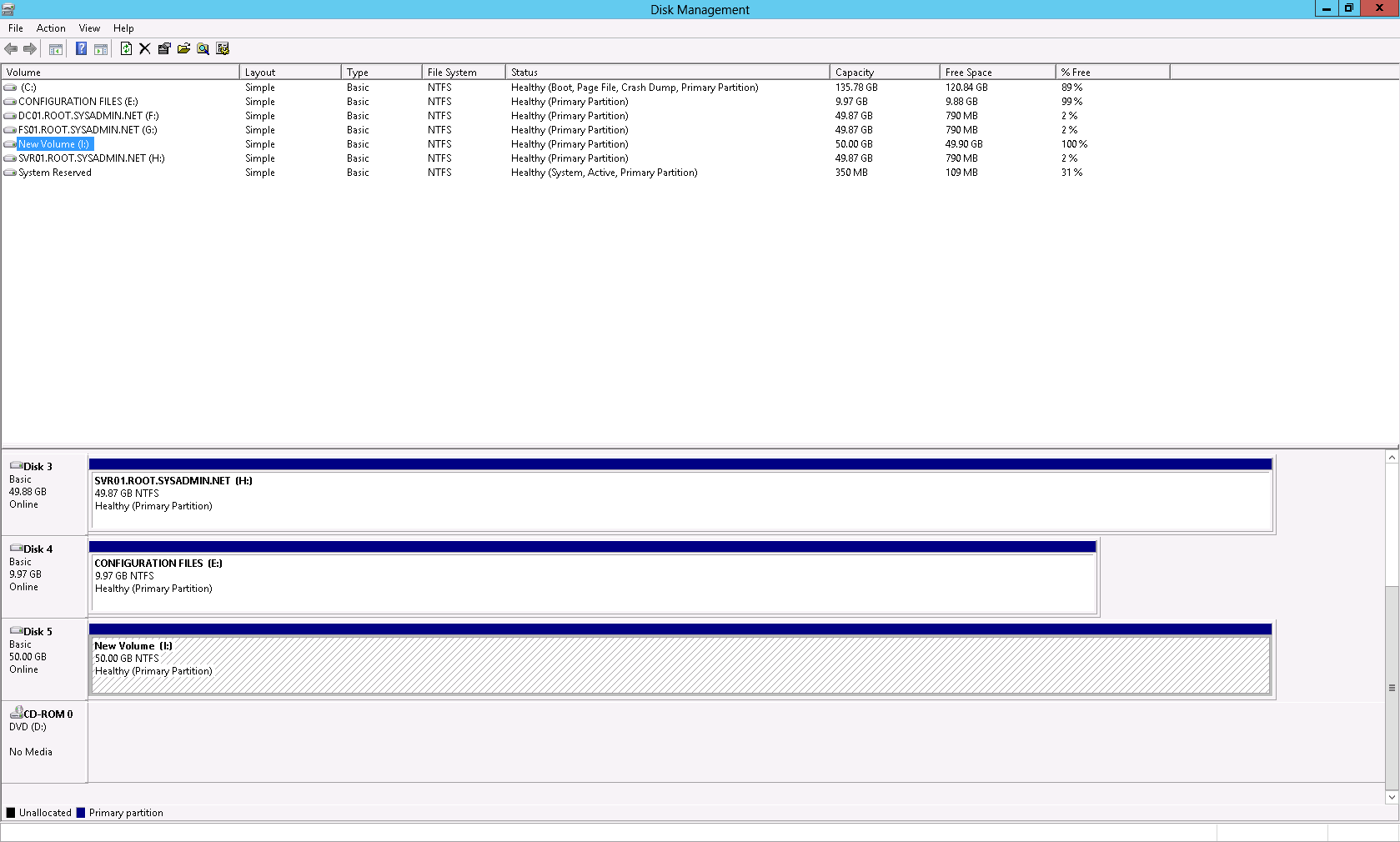 Enjoy!
Enjoy!




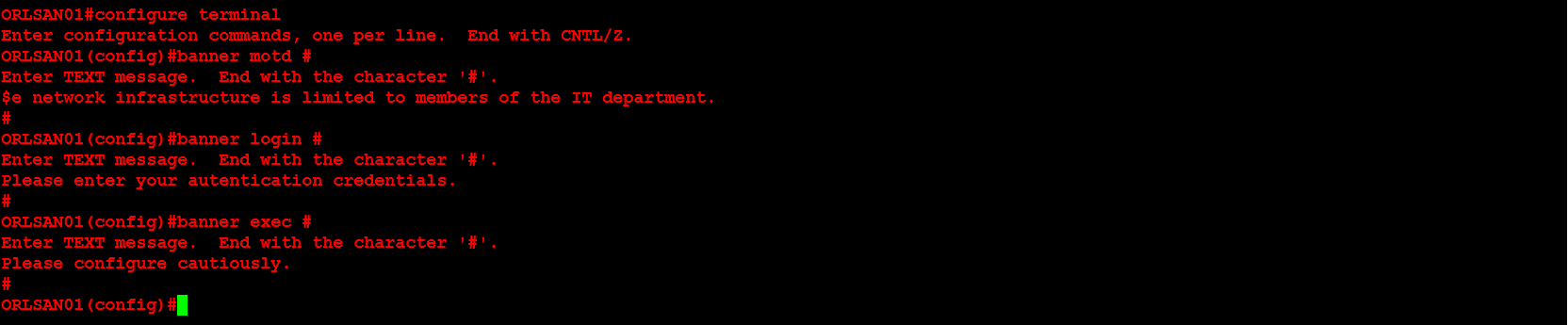
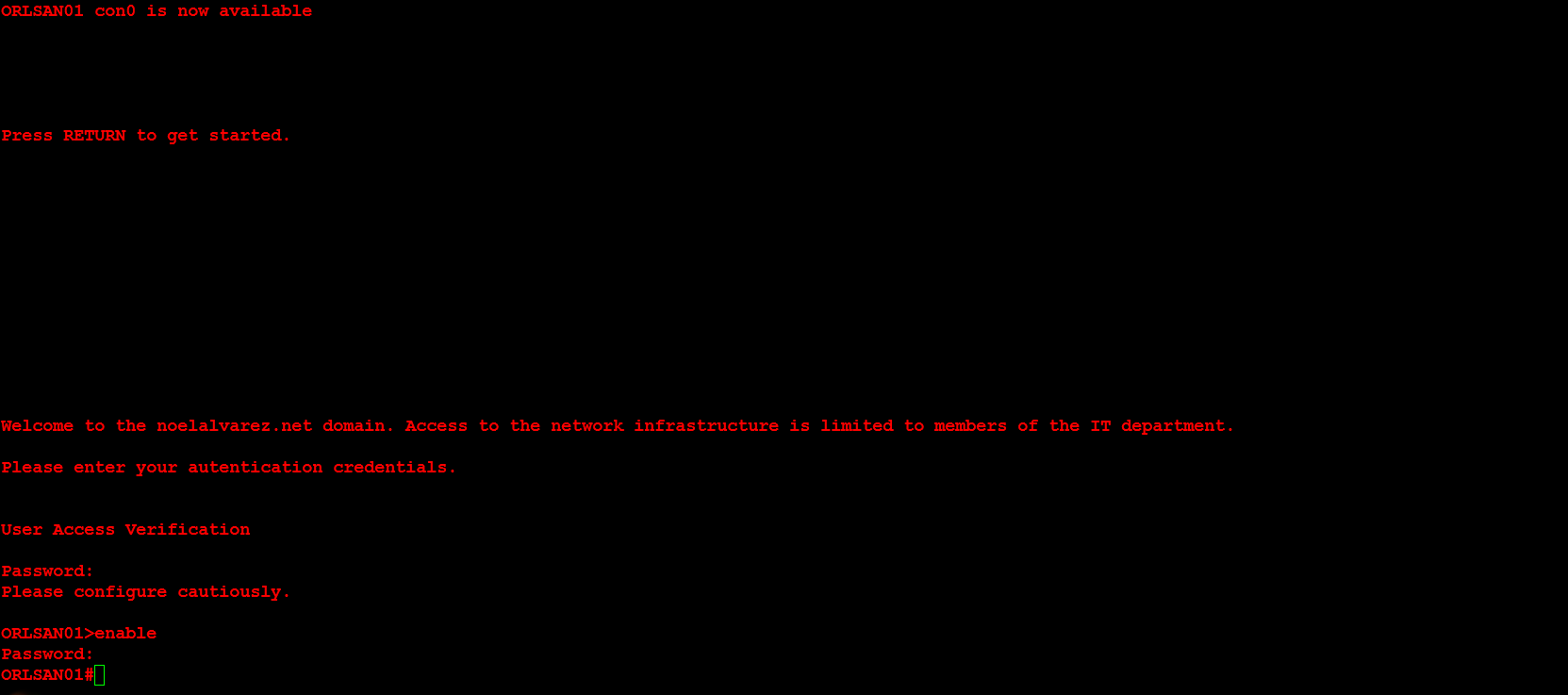
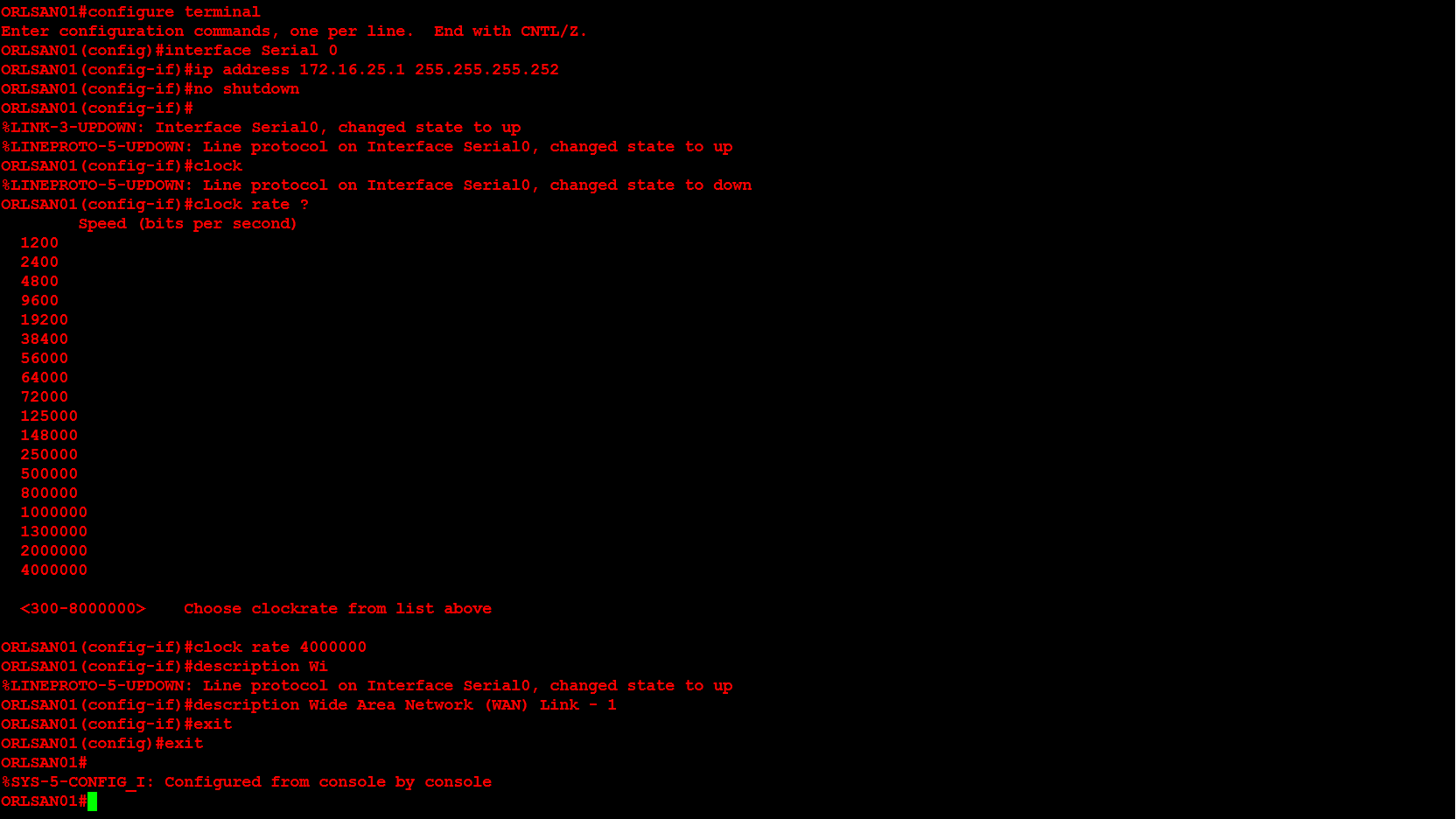
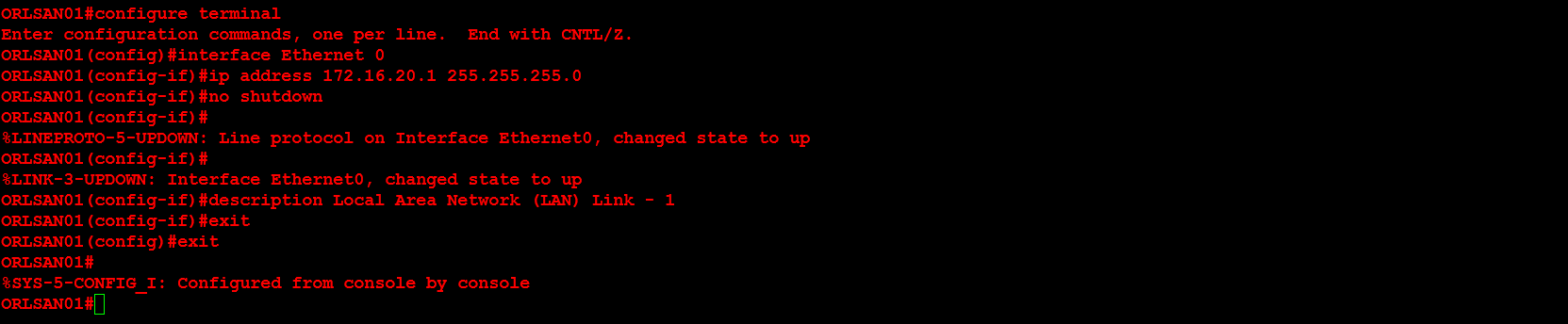
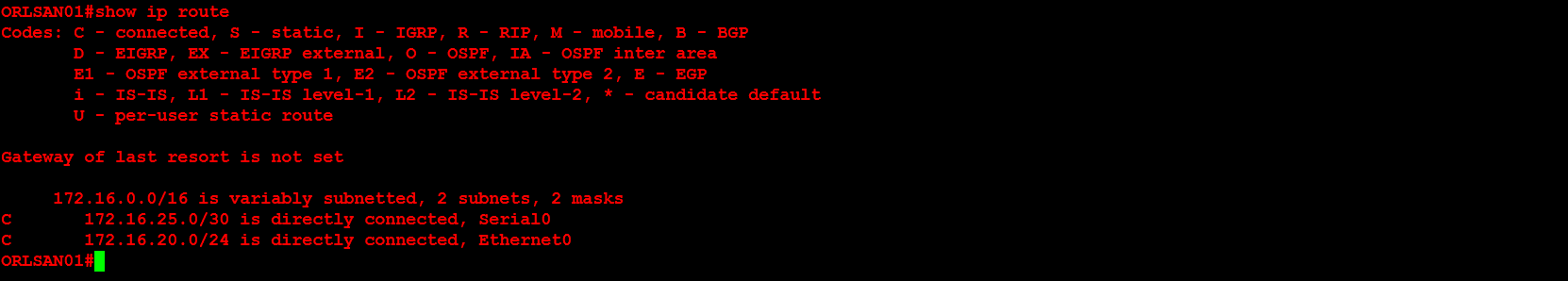


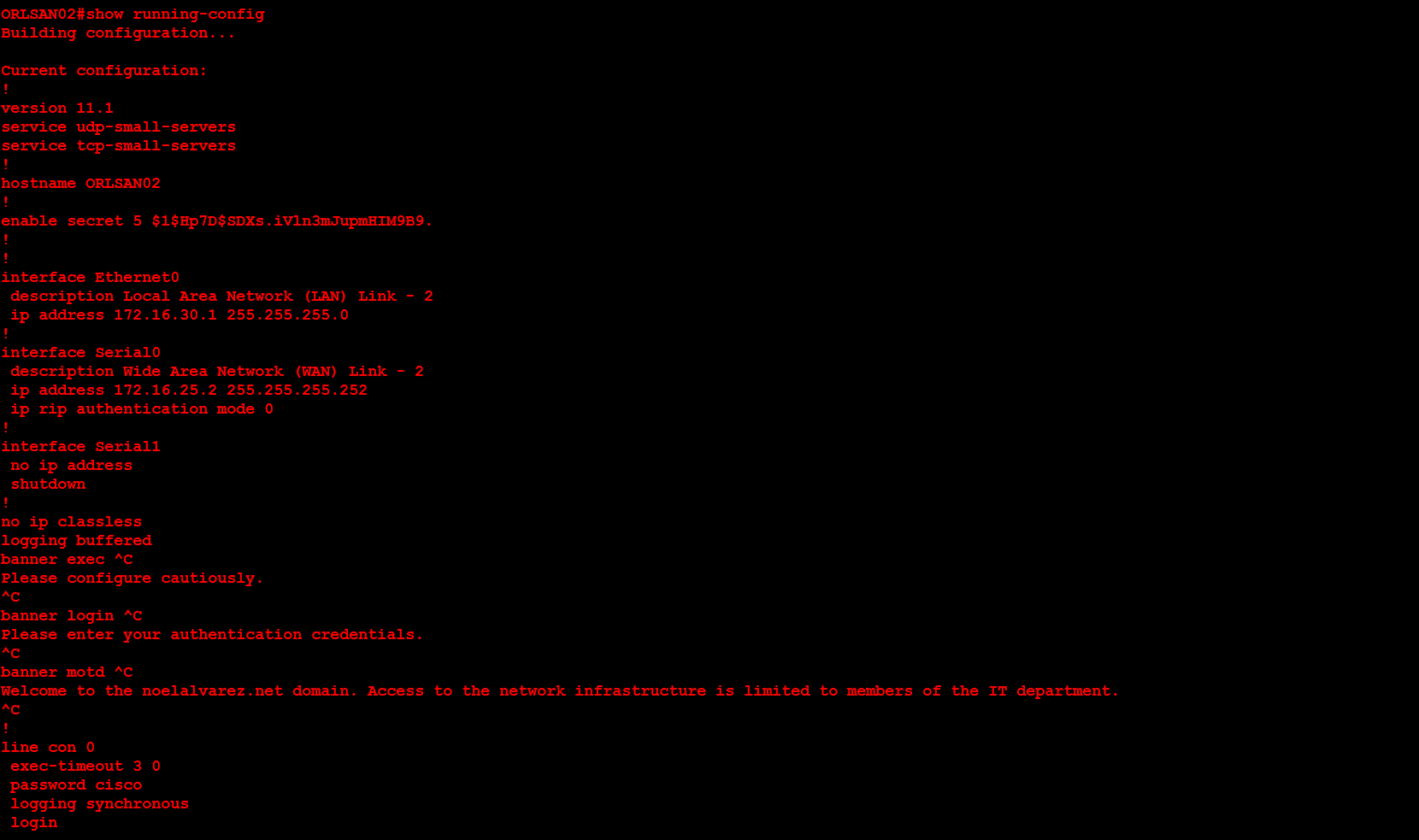



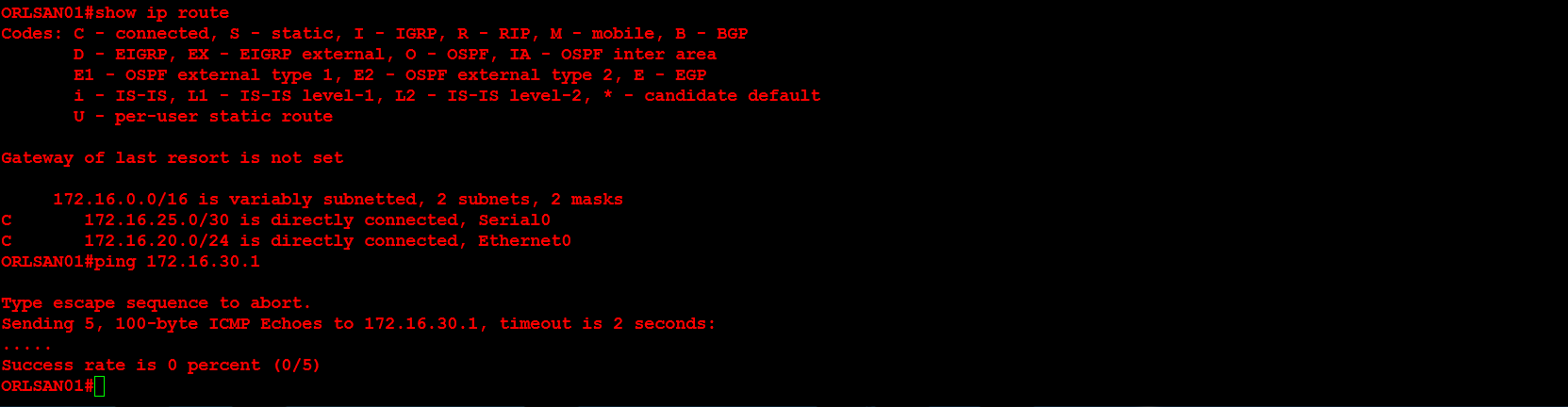
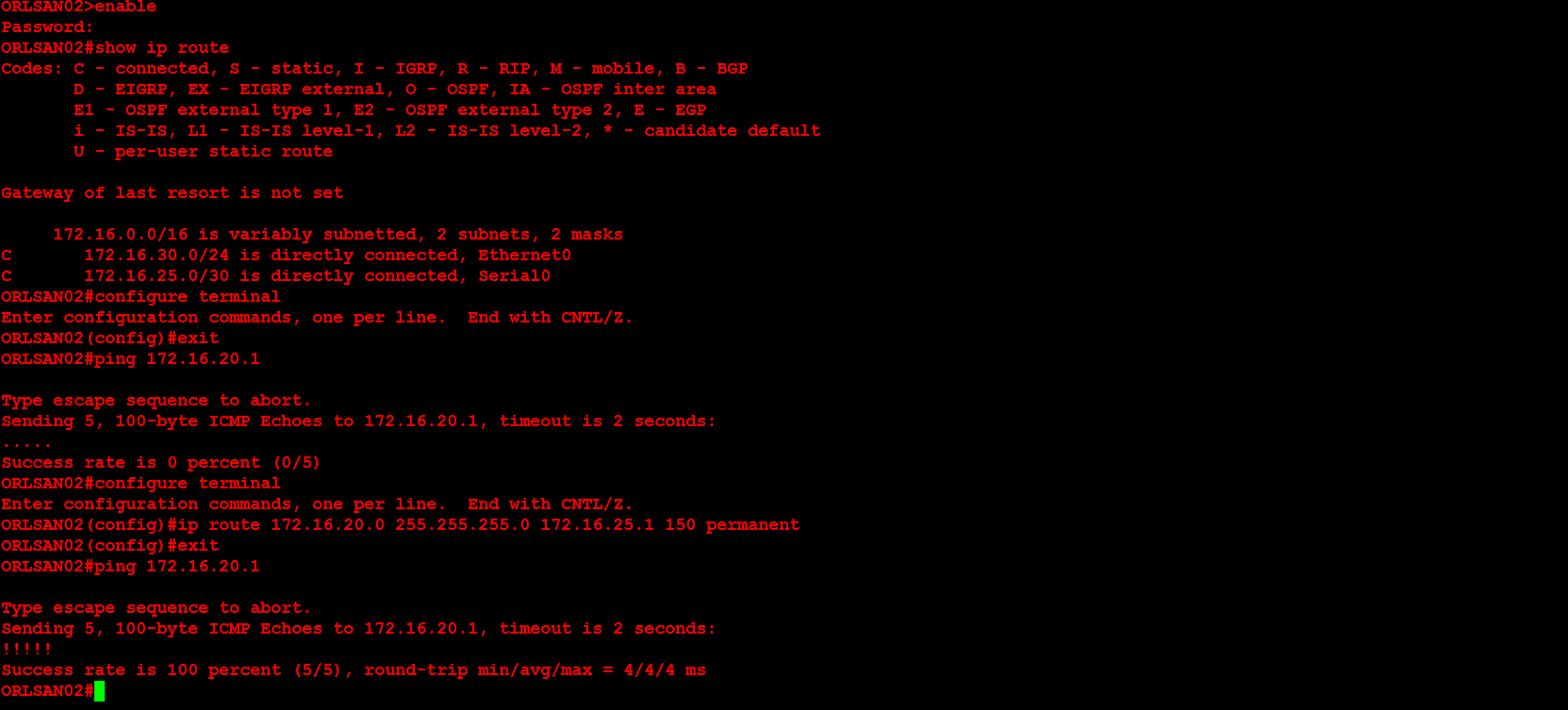
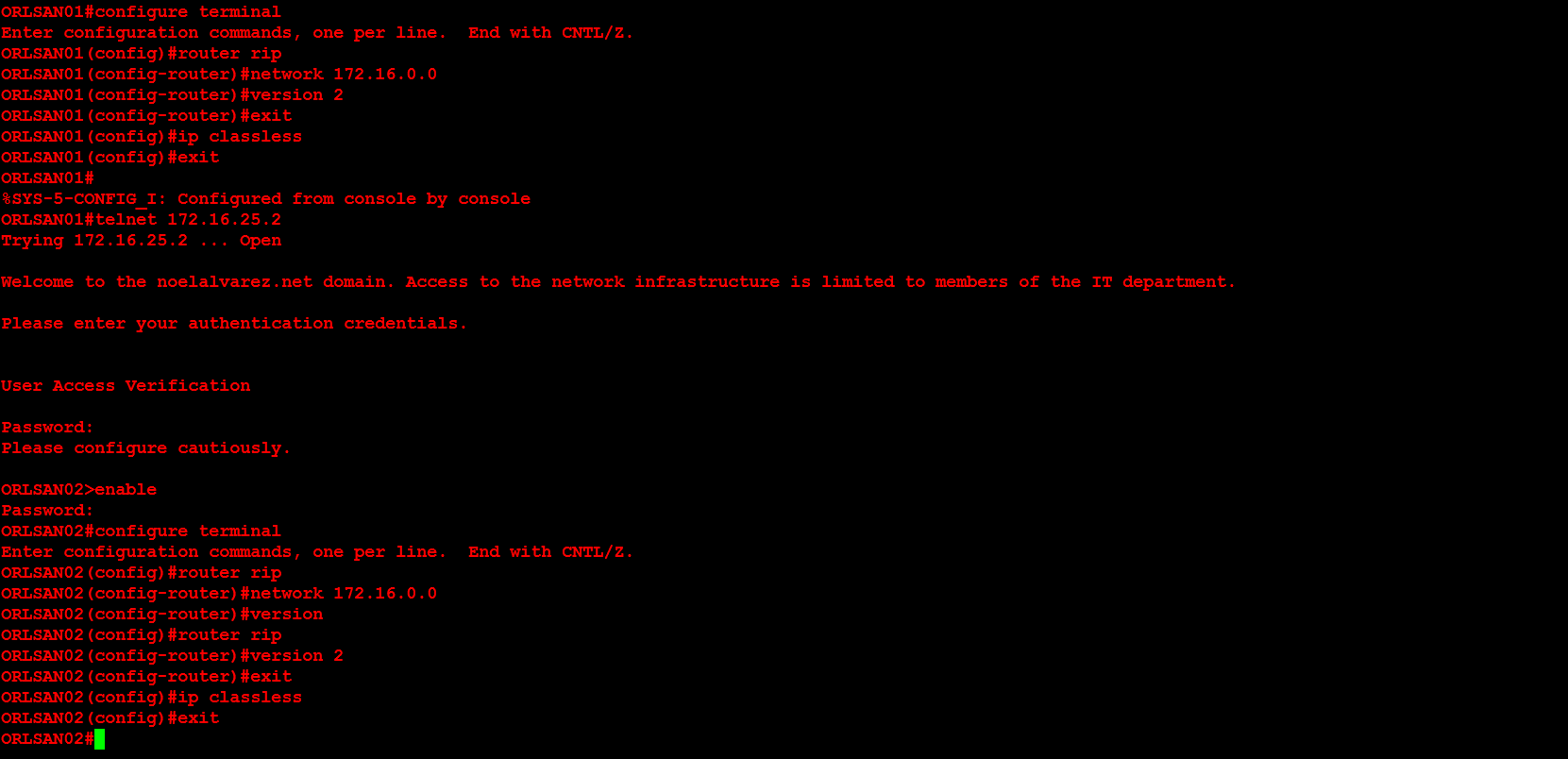
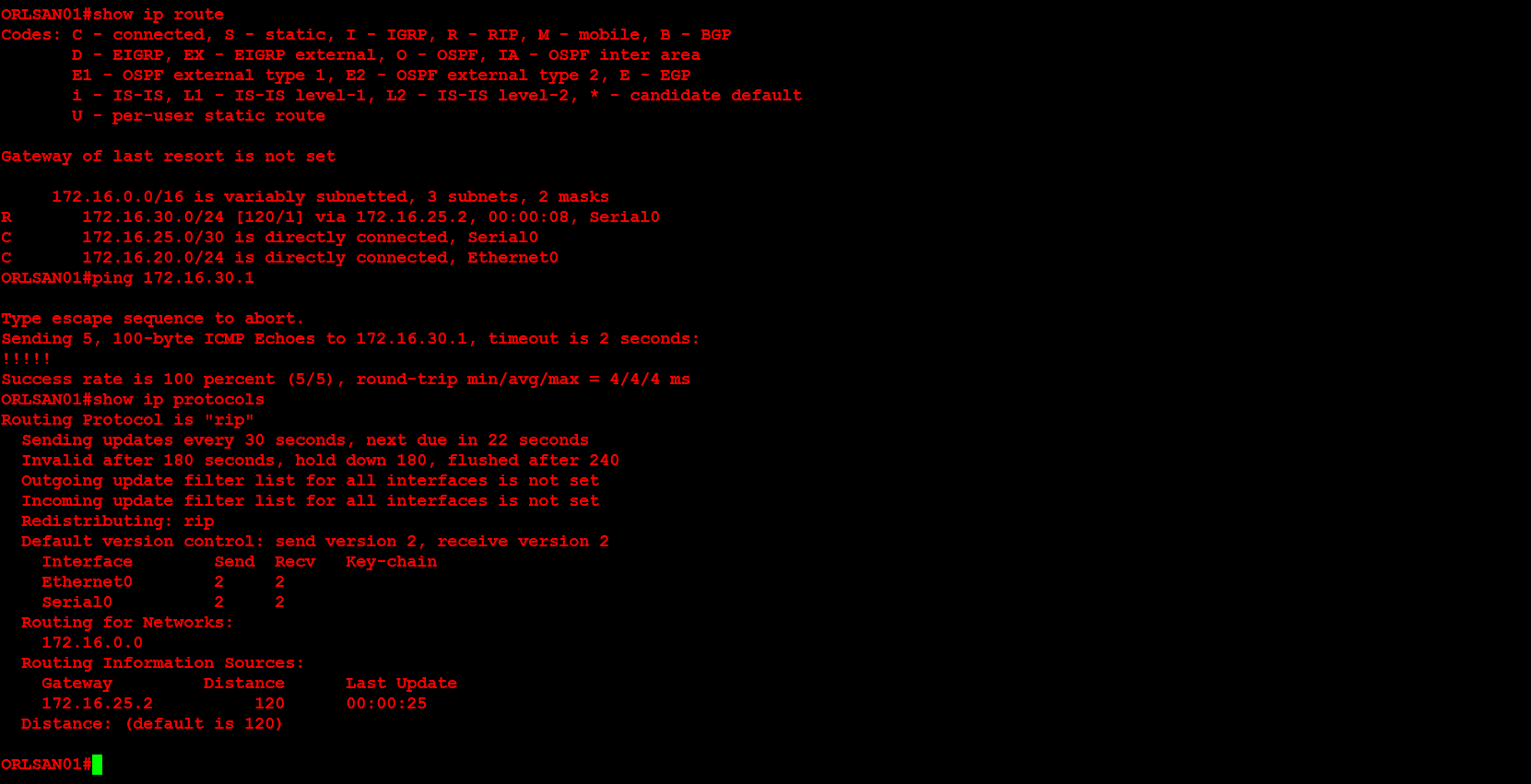
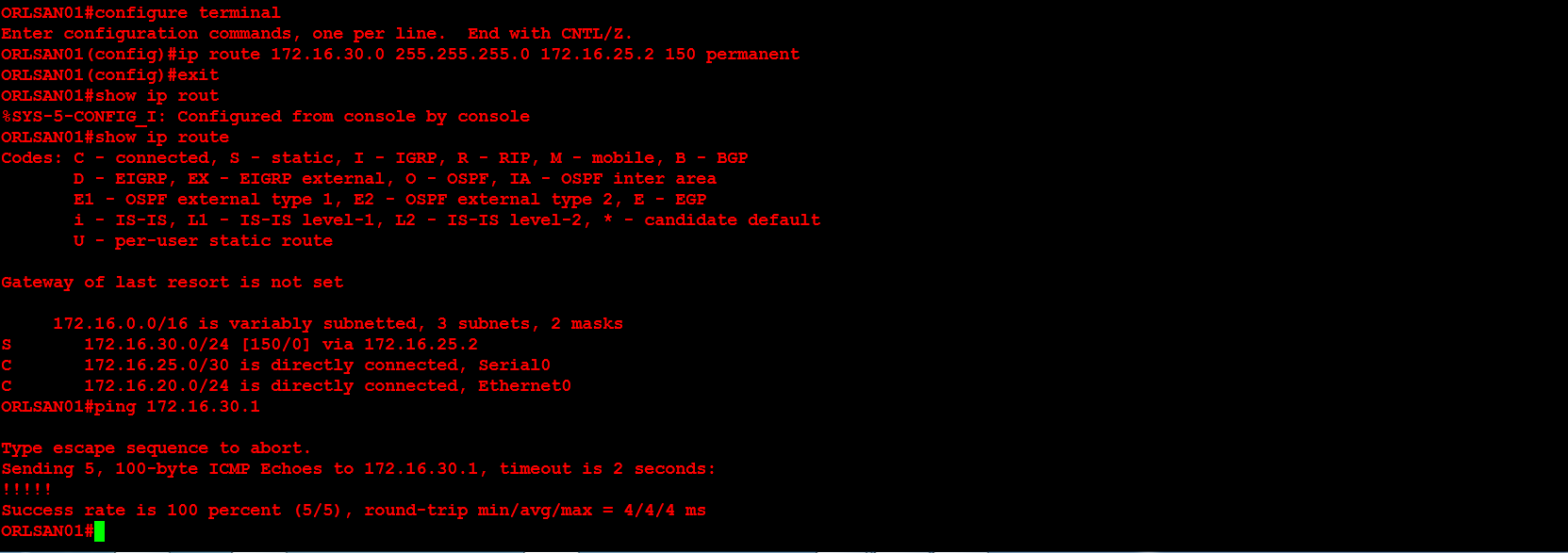 Next, I will configure ORLSAN02 with a static route to the 172.16.20.0/24 network, verify the route is in the routing table then ping 172.16.20.1.
Next, I will configure ORLSAN02 with a static route to the 172.16.20.0/24 network, verify the route is in the routing table then ping 172.16.20.1.