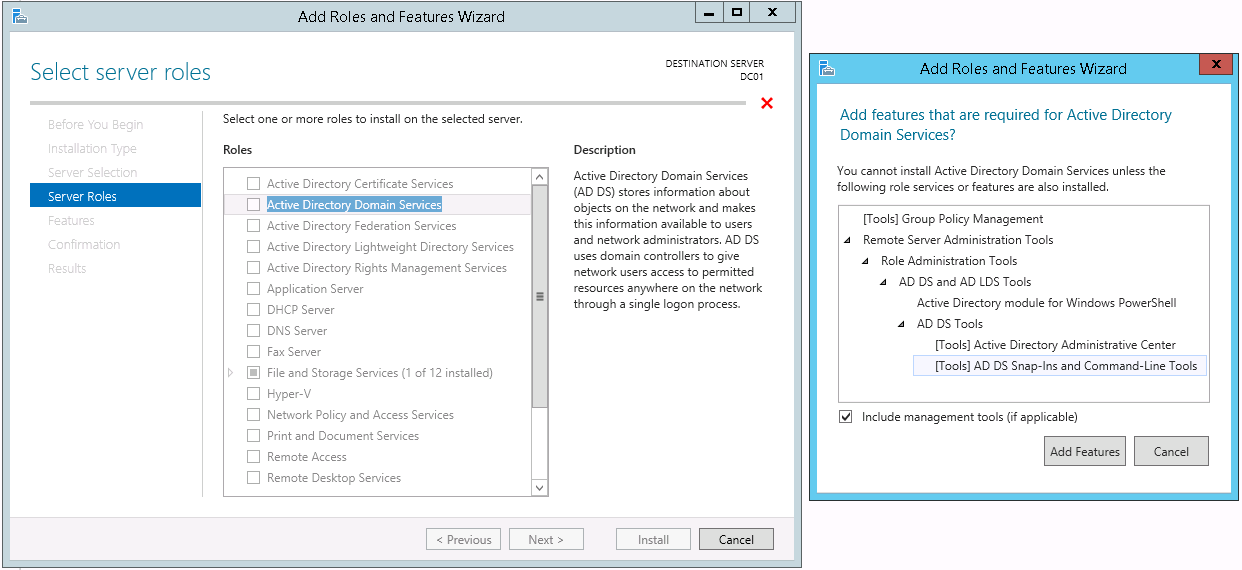
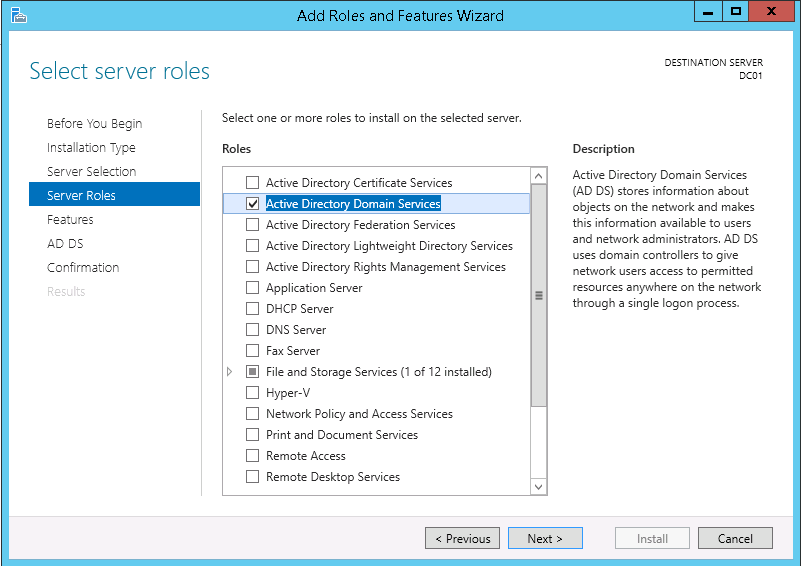
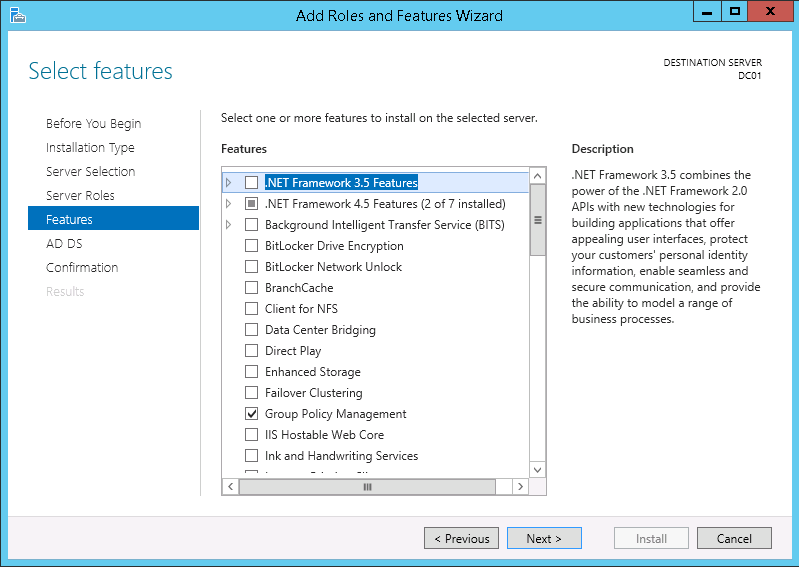
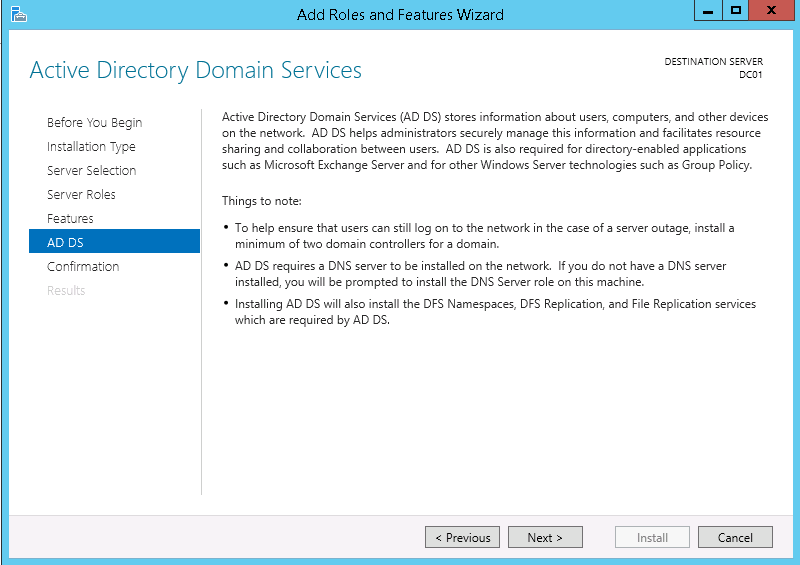
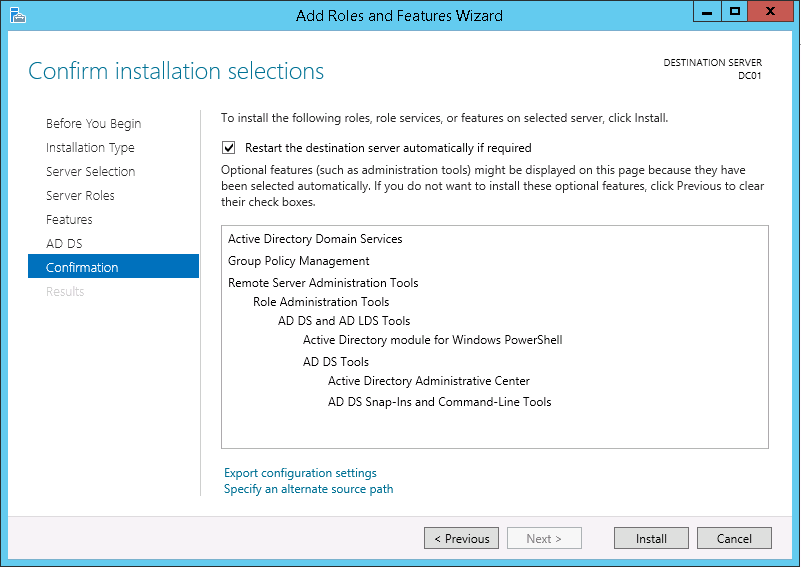
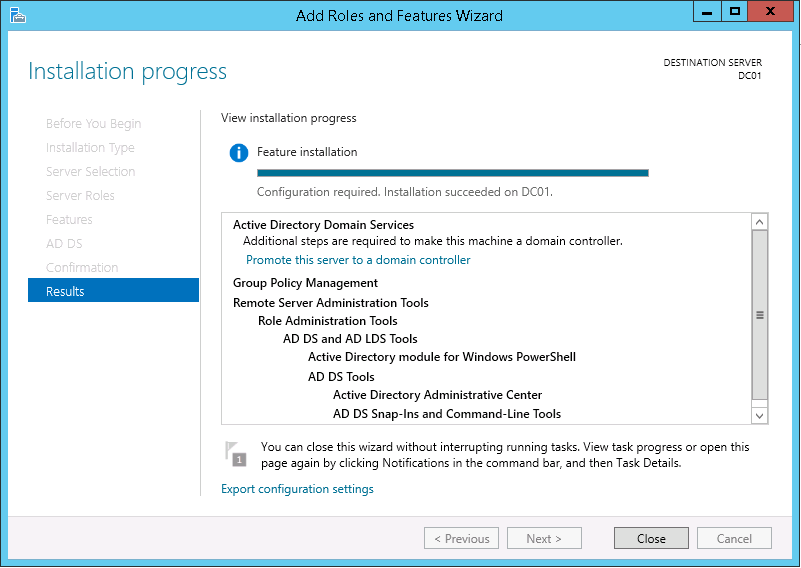
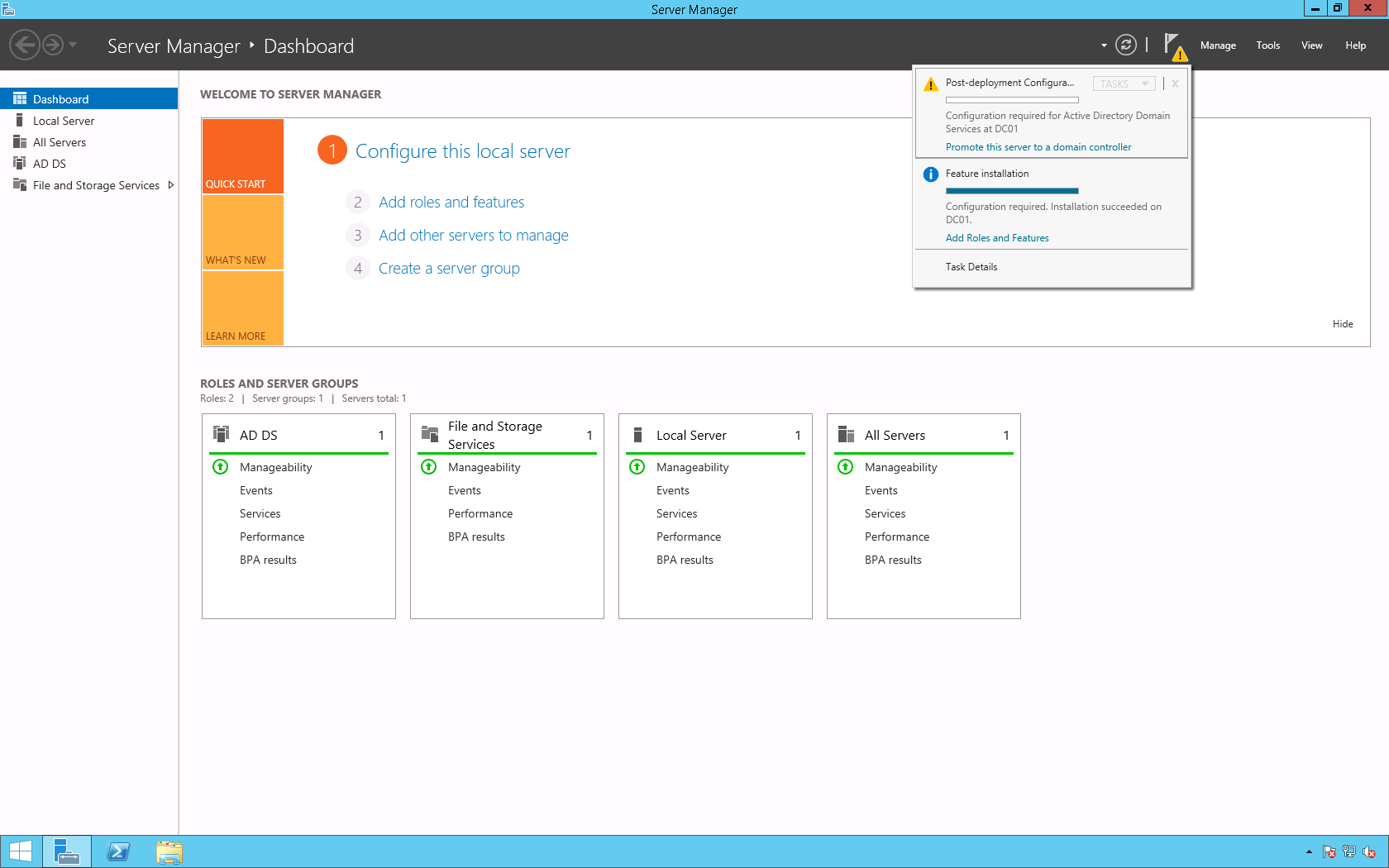
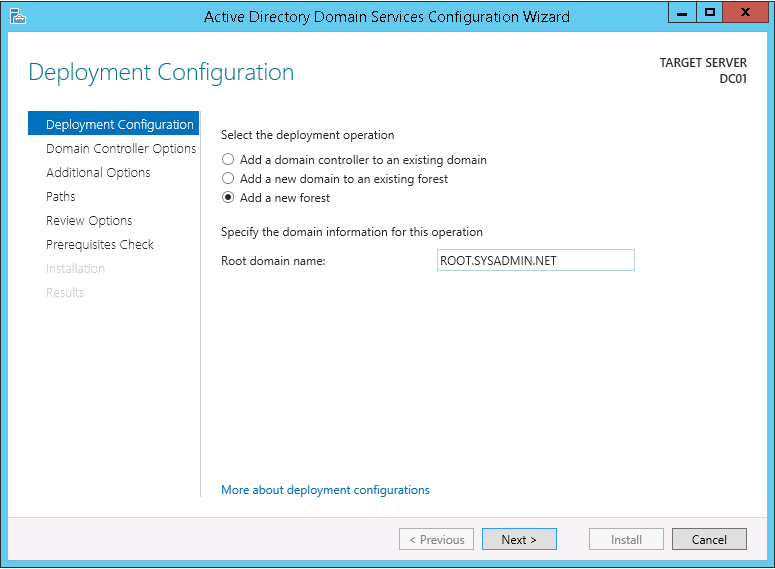
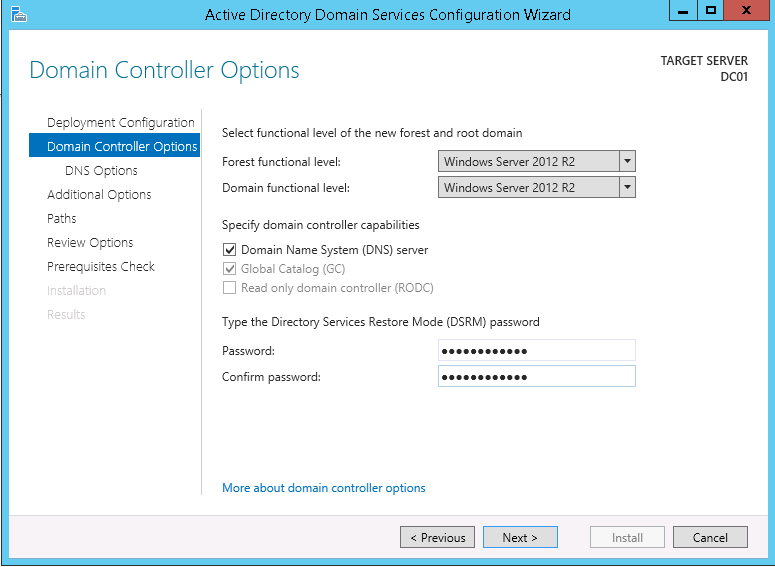
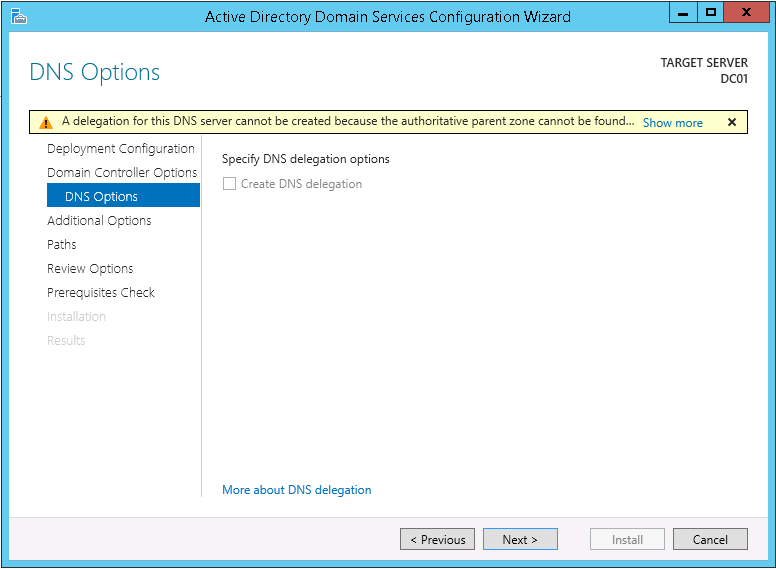
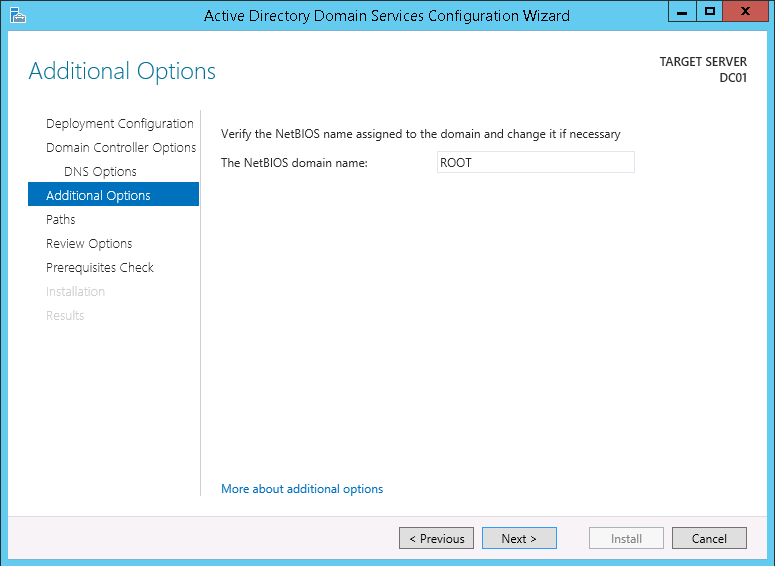
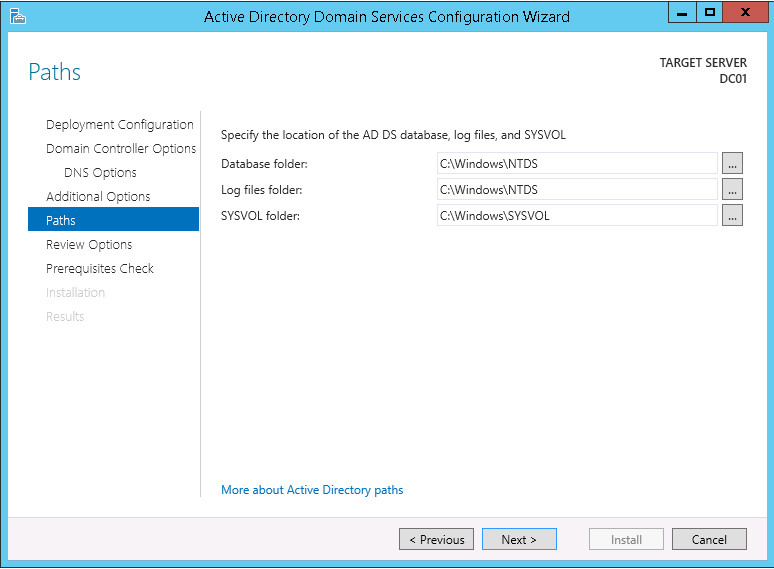
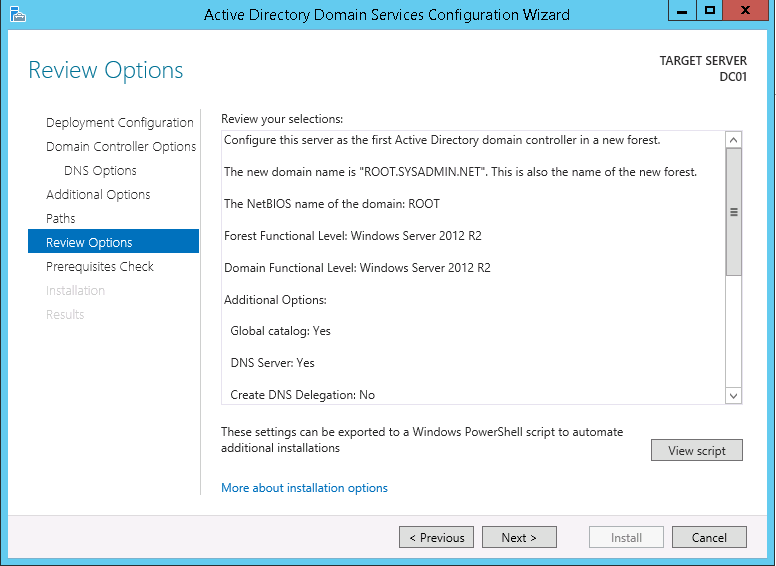
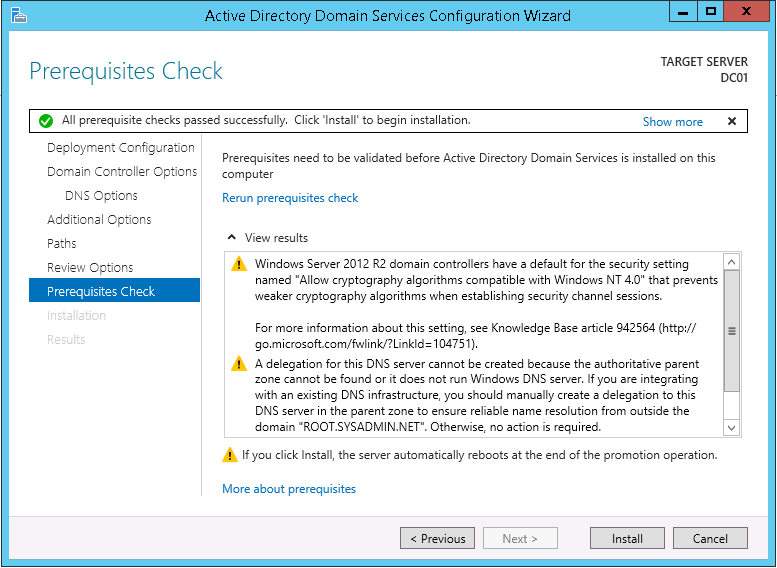
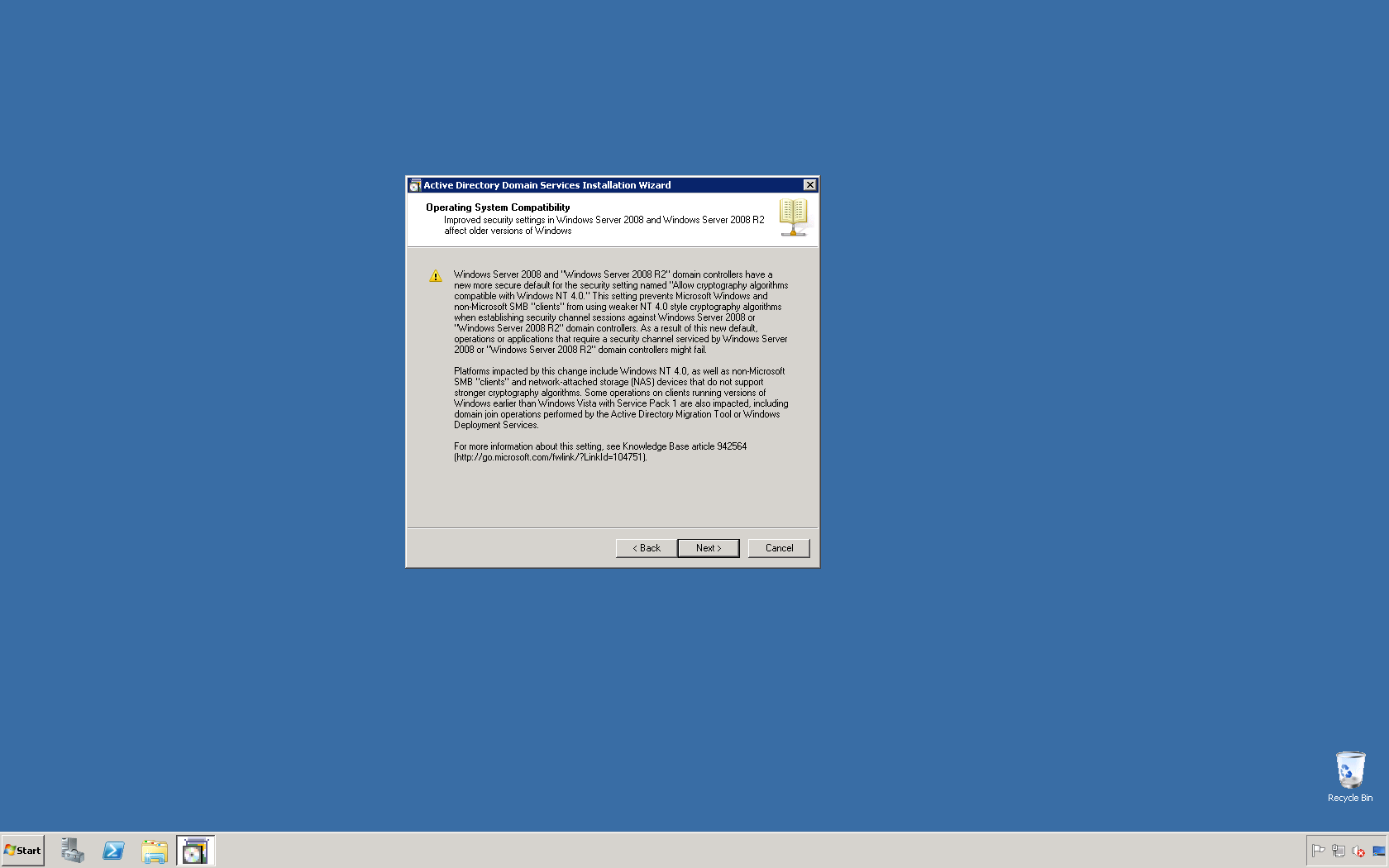
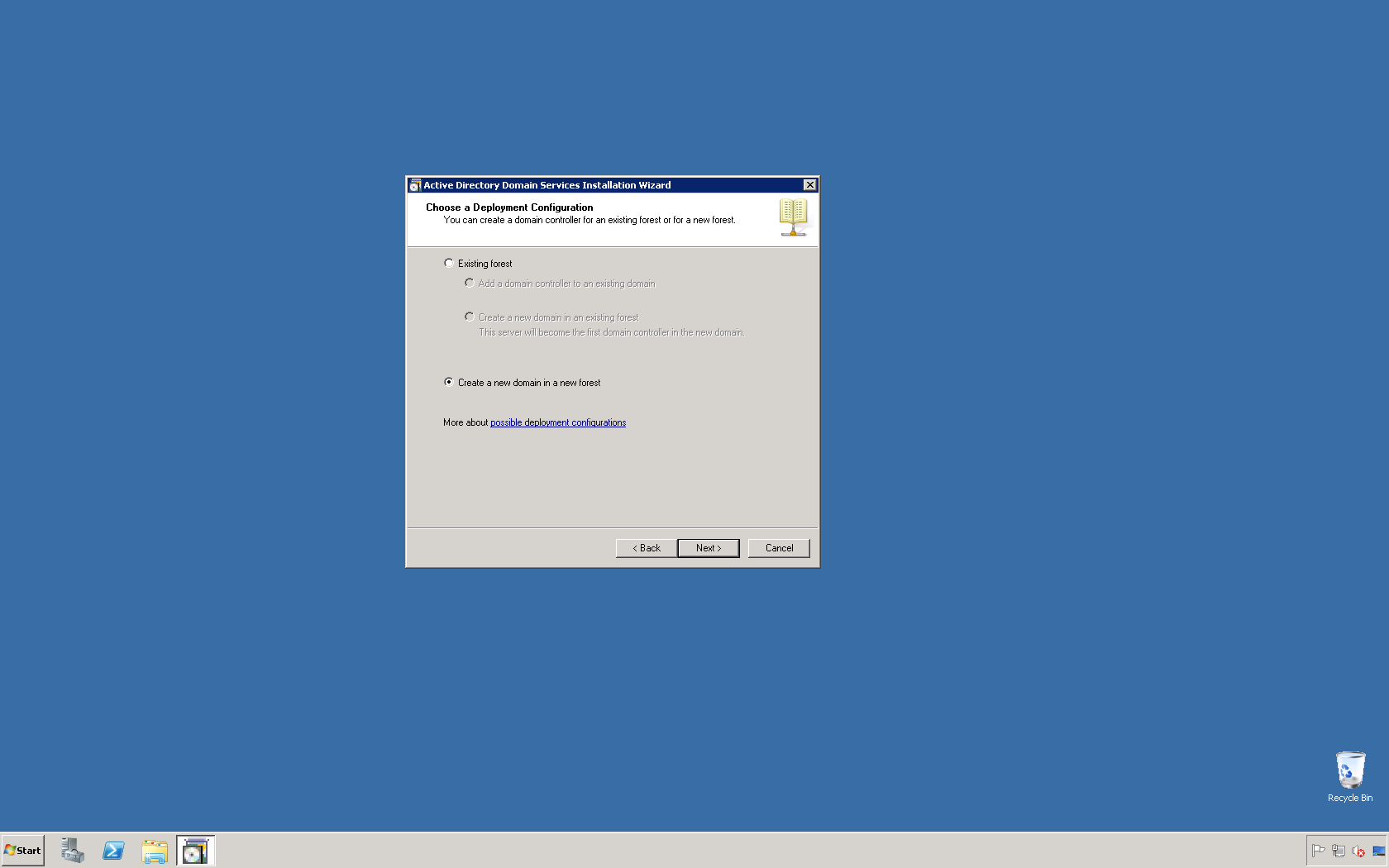
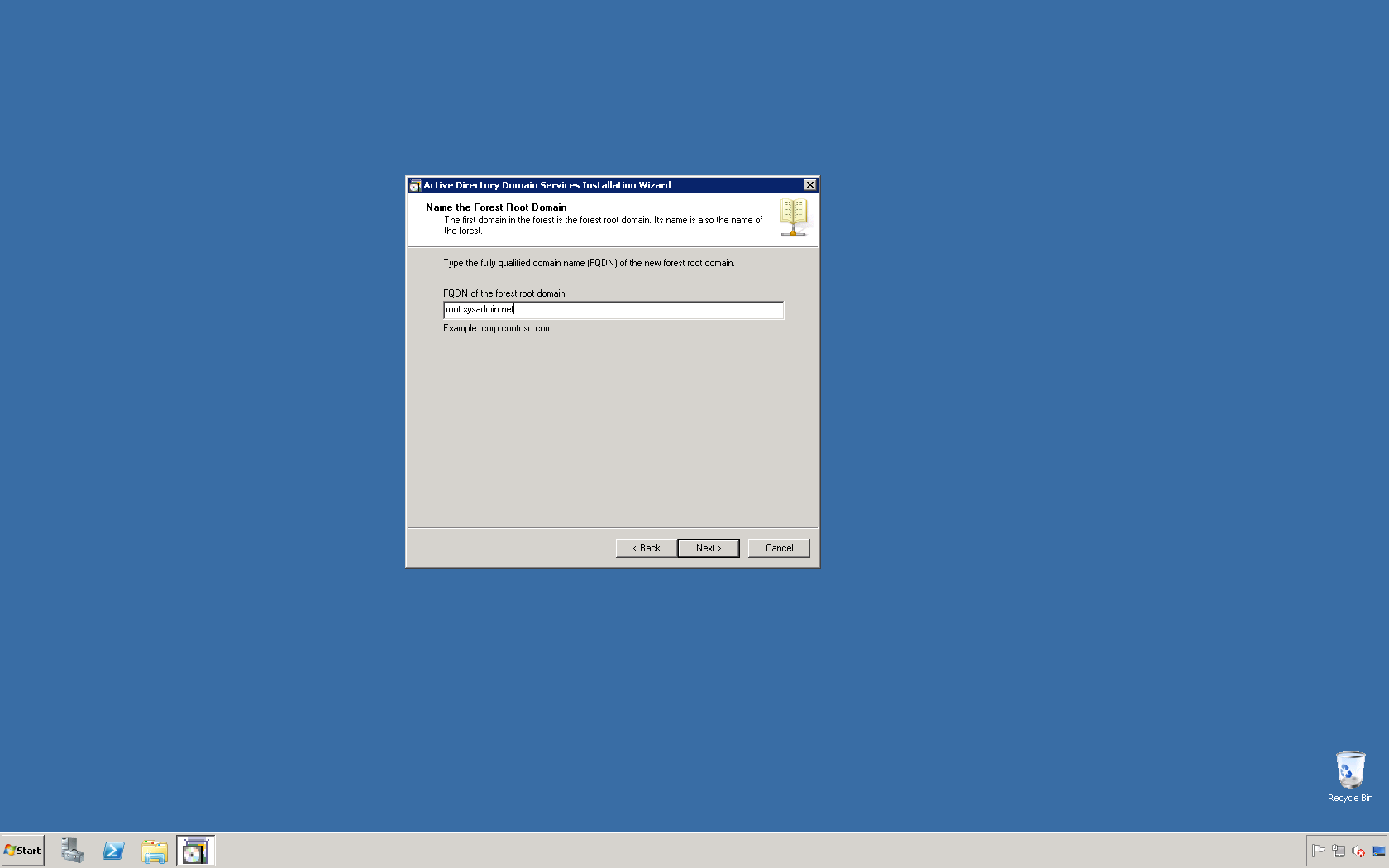
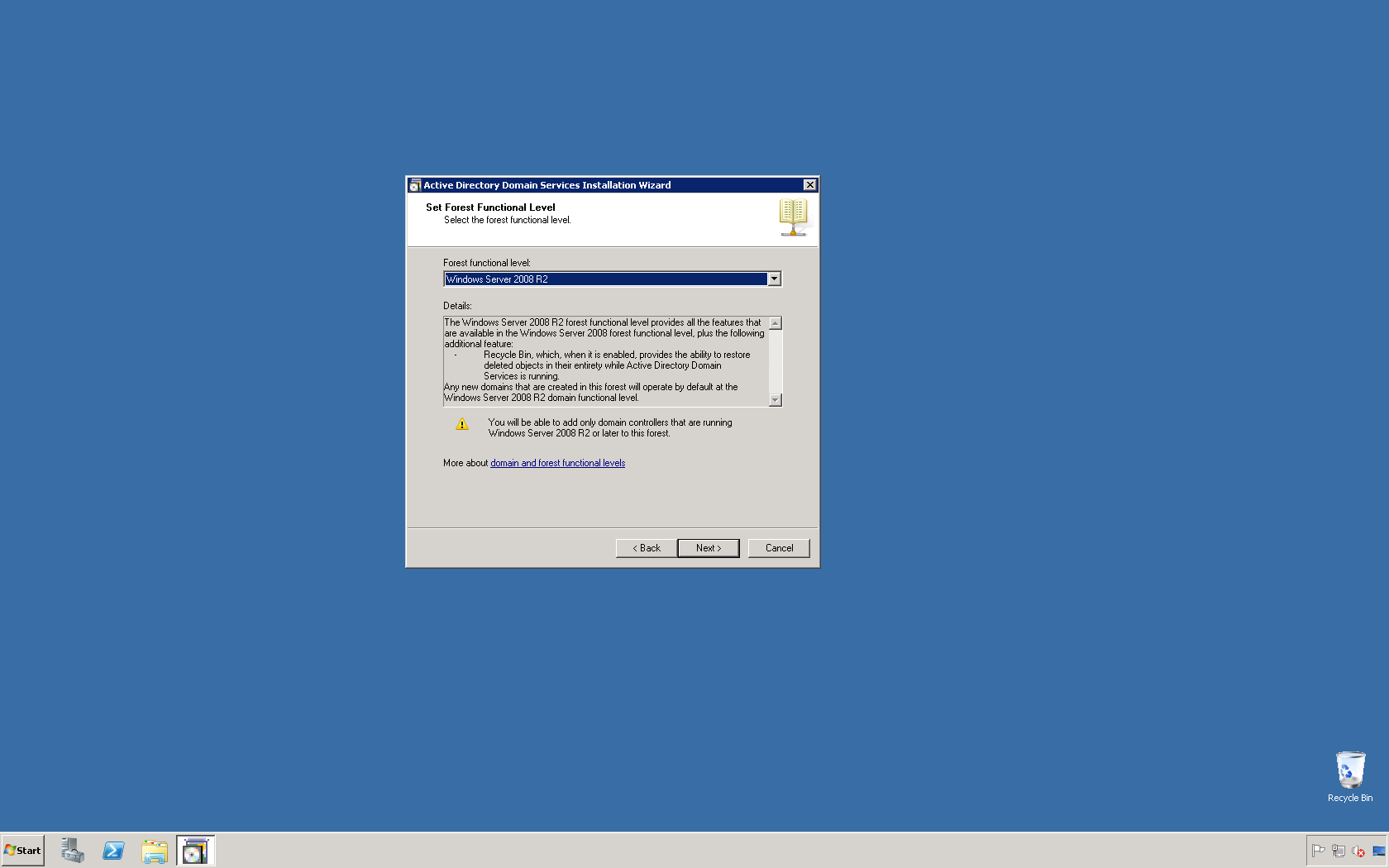
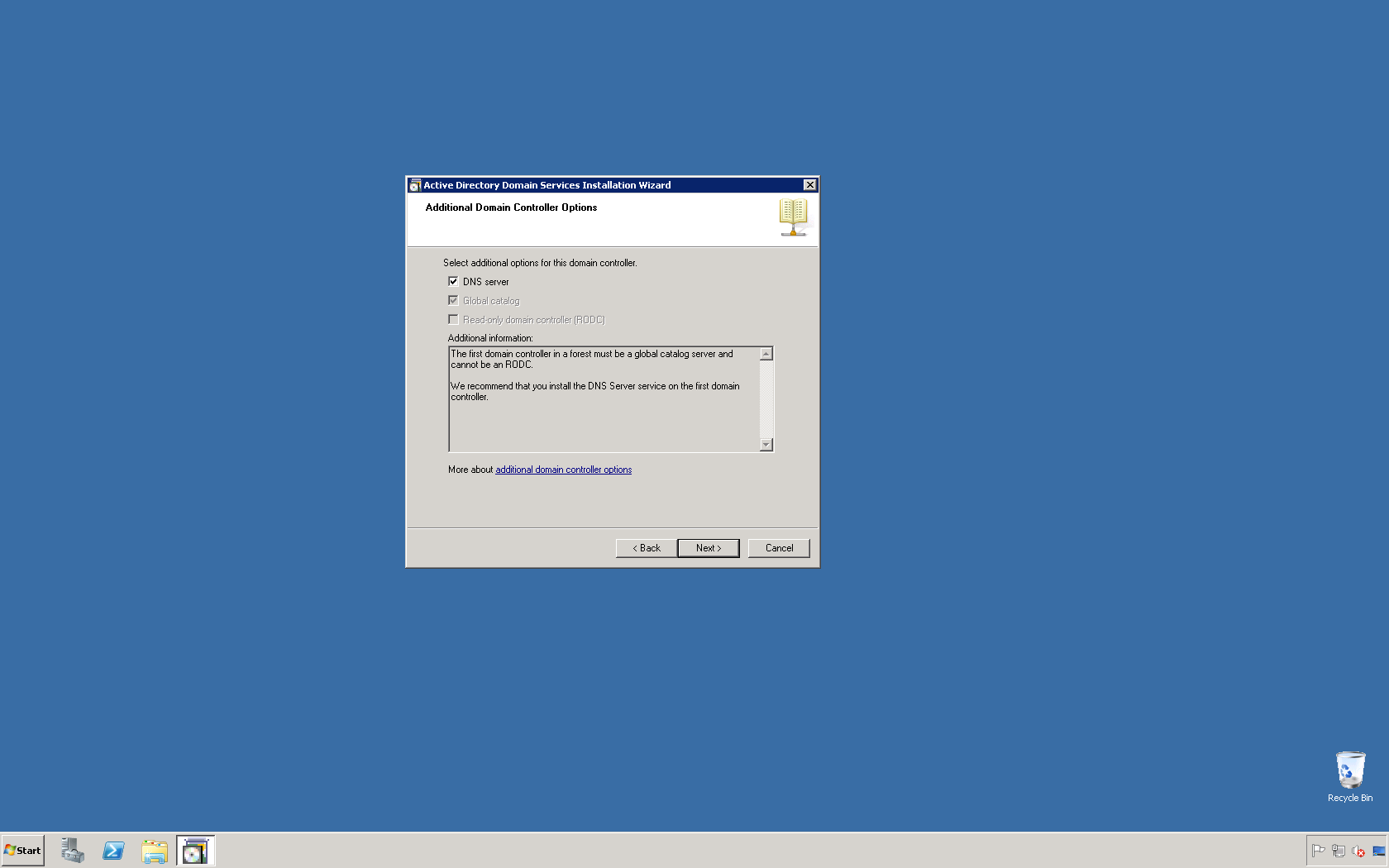
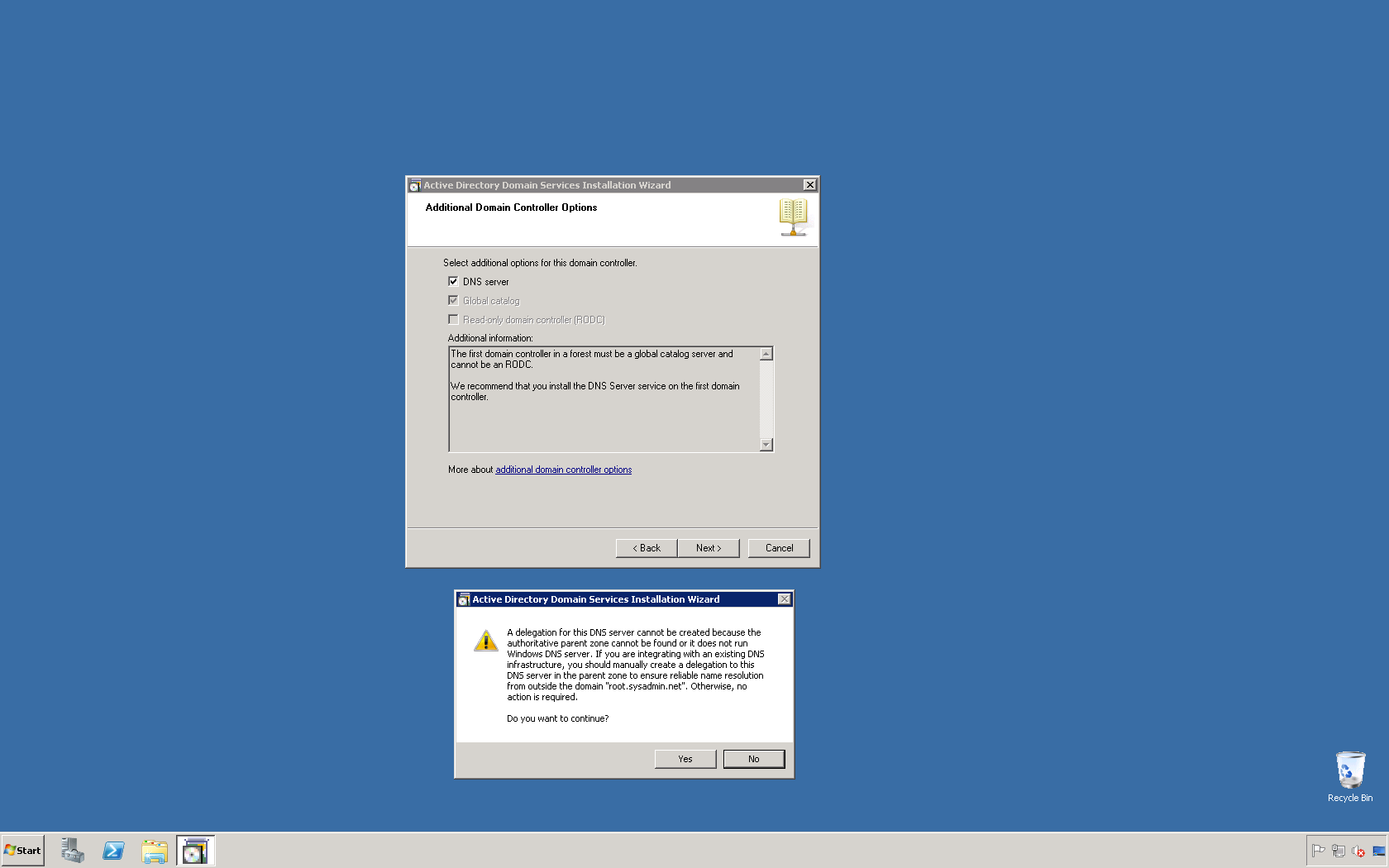
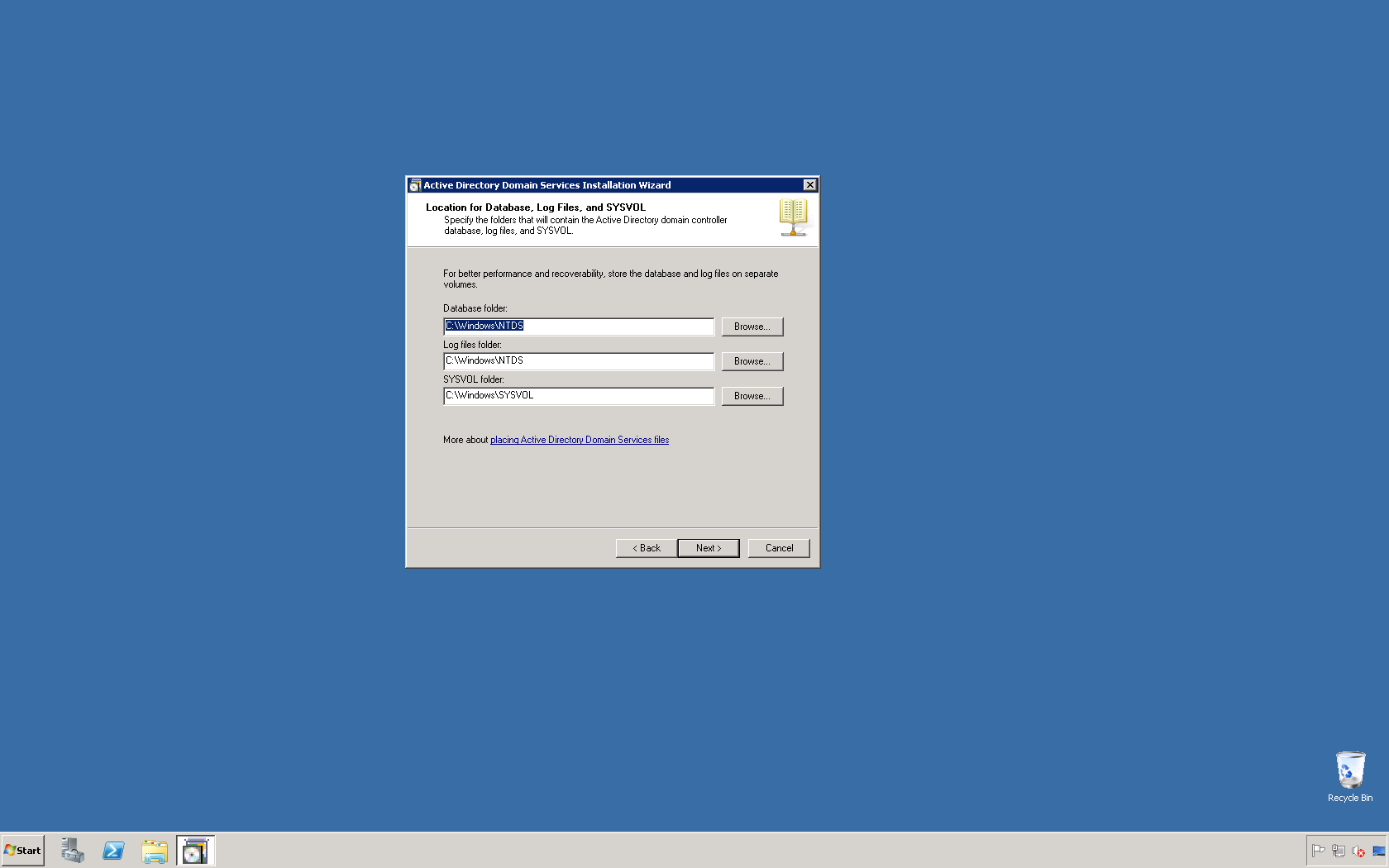
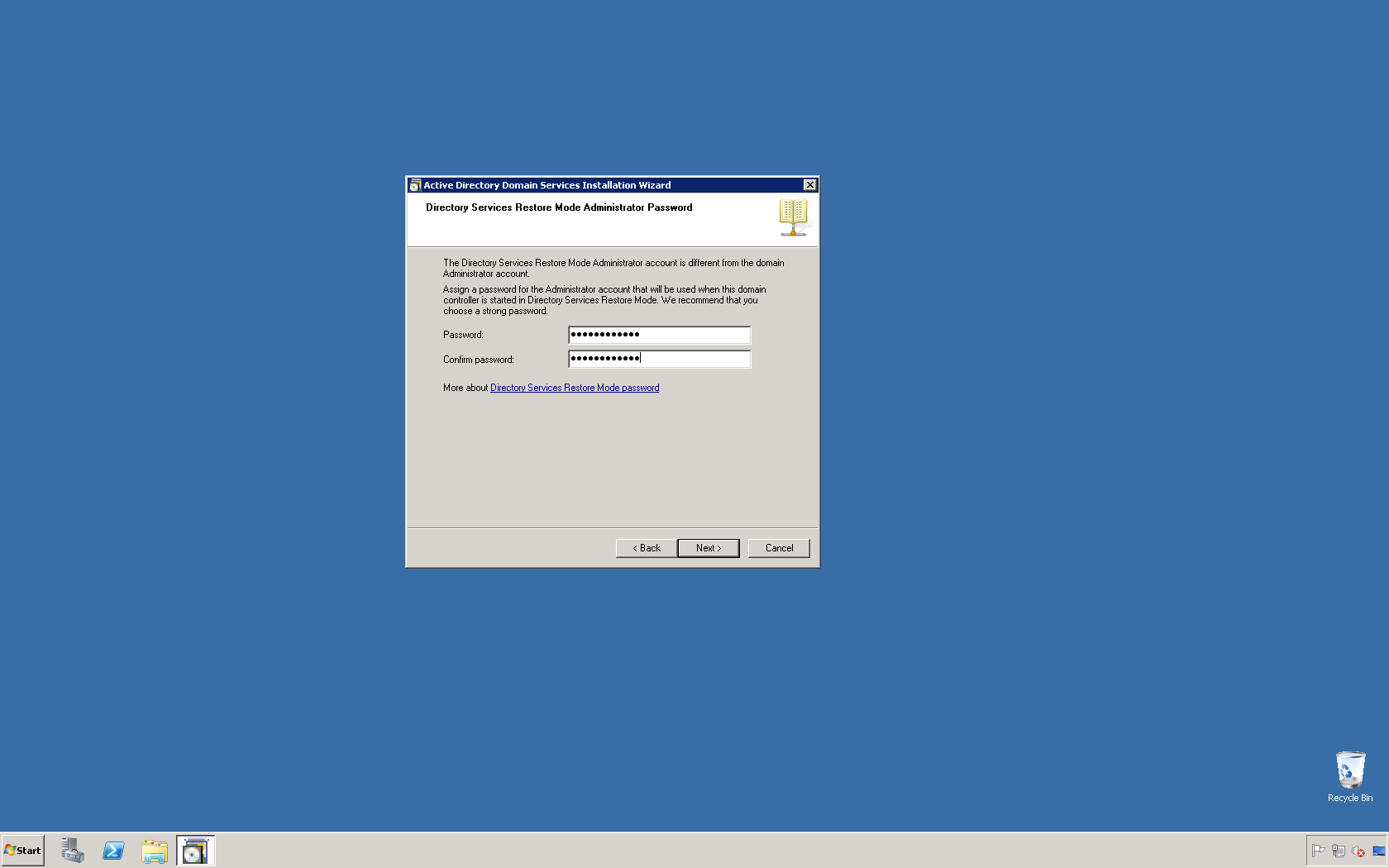
This script will list the name and account name of each user within an Active Directory group and provide the output of the results in a file and directory of your choice.
Example: Get-ADGroupMember -identity “<Group Name>” | Select Name, SamAccountName | out-file -filepath “<File Path>”